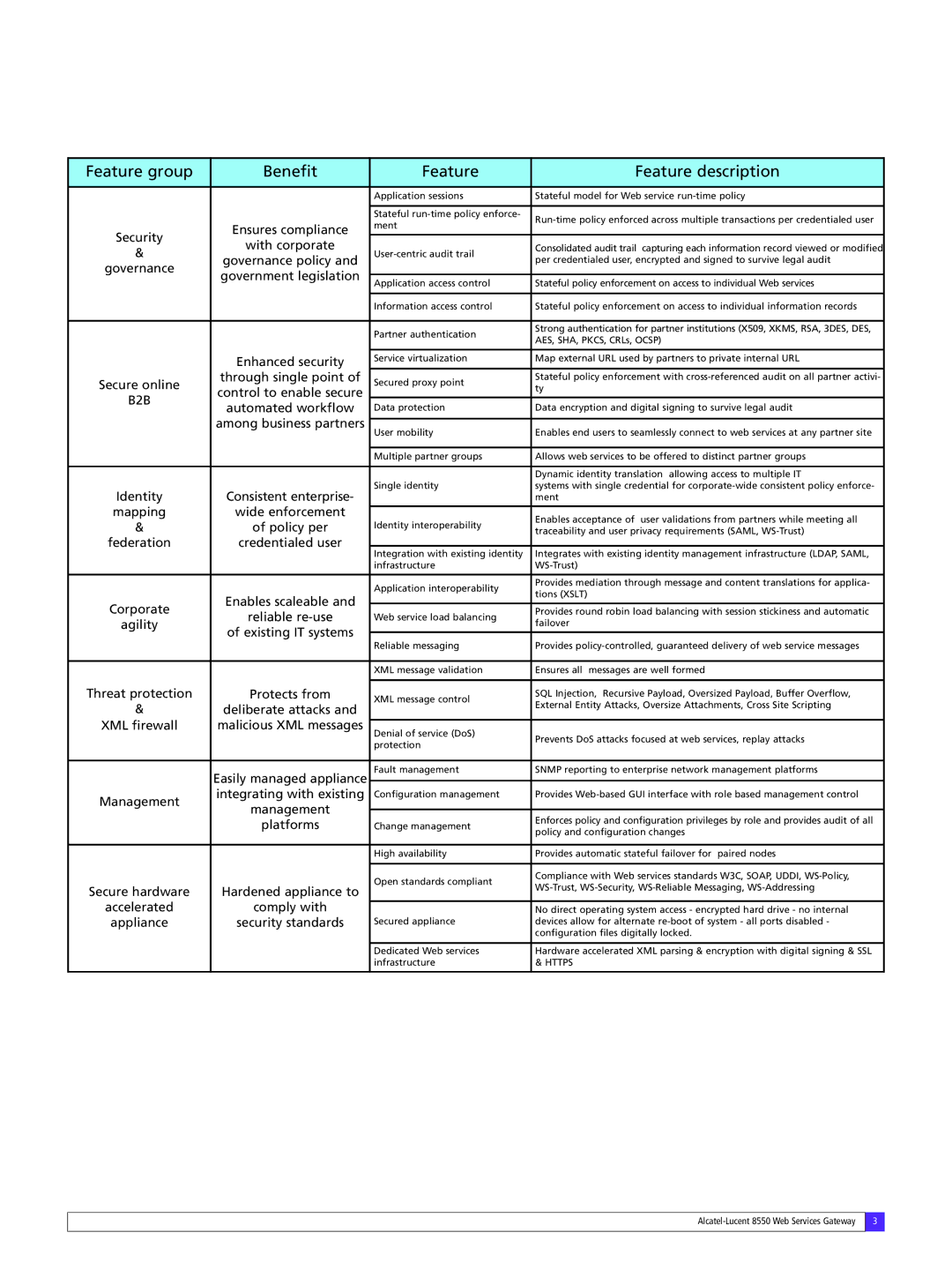
Feature group | Benefit | Feature | Feature description | |
|
|
|
| |
|
| Application sessions | Stateful model for Web service | |
|
|
|
| |
|
| Stateful | ||
| Ensures compliance | ment | ||
Security |
| |||
|
| |||
with corporate |
| Consolidated audit trail capturing each information record viewed or modified | ||
& | ||||
governance policy and | per credentialed user, encrypted and signed to survive legal audit | |||
governance |
| |||
government legislation |
|
| ||
| Application access control | Stateful policy enforcement on access to individual Web services | ||
|
|
|
| |
|
| Information access control | Stateful policy enforcement on access to individual information records | |
|
|
|
| |
|
| Partner authentication | Strong authentication for partner institutions (X509, XKMS, RSA, 3DES, DES, | |
|
| AES, SHA, PKCS, CRLs, OCSP) | ||
|
|
| ||
|
|
|
| |
| Enhanced security | Service virtualization | Map external URL used by partners to private internal URL | |
Secure online | through single point of | Secured proxy point | Stateful policy enforcement with | |
ty | ||||
control to enable secure |
| |||
B2B |
|
| ||
automated workflow | Data protection | Data encryption and digital signing to survive legal audit | ||
| ||||
| among business partners |
|
| |
| User mobility | Enables end users to seamlessly connect to web services at any partner site | ||
|
| |||
|
|
|
| |
|
| Multiple partner groups | Allows web services to be offered to distinct partner groups | |
|
|
|
| |
|
|
| Dynamic identity translation allowing access to multiple IT | |
Identity | Consistent enterprise- | Single identity | systems with single credential for | |
| ment | |||
mapping | wide enforcement | Identity interoperability | Enables acceptance of user validations from partners while meeting all | |
& | of policy per | |||
traceability and user privacy requirements (SAML, | ||||
| ||||
federation | credentialed user |
|
| |
Integration with existing identity | Integrates with existing identity management infrastructure (LDAP, SAML, | |||
|
| |||
|
| infrastructure | ||
|
|
|
| |
|
| Application interoperability | Provides mediation through message and content translations for applica- | |
| Enables scaleable and | tions (XSLT) | ||
|
| |||
Corporate |
|
| ||
| Provides round robin load balancing with session stickiness and automatic | |||
reliable | Web service load balancing | |||
agility | failover | |||
of existing IT systems |
| |||
| Reliable messaging | Provides | ||
|
| |||
|
|
|
| |
|
| XML message validation | Ensures all messages are well formed | |
Threat protection | Protects from |
|
| |
XML message control | SQL Injection, Recursive Payload, Oversized Payload, Buffer Overflow, | |||
& | deliberate attacks and | External Entity Attacks, Oversize Attachments, Cross Site Scripting | ||
| ||||
|
| |||
XML firewall | malicious XML messages |
|
| |
Denial of service (DoS) | Prevents DoS attacks focused at web services, replay attacks | |||
|
| |||
|
| protection | ||
|
|
| ||
|
|
|
| |
| Easily managed appliance | Fault management | SNMP reporting to enterprise network management platforms | |
|
|
| ||
|
|
| ||
Management | integrating with existing | Configuration management | Provides | |
management |
|
| ||
|
| Enforces policy and configuration privileges by role and provides audit of all | ||
| platforms | Change management | ||
| policy and configuration changes | |||
|
|
| ||
|
|
|
| |
|
| High availability | Provides automatic stateful failover for paired nodes | |
|
|
|
| |
|
| Open standards compliant | Compliance with Web services standards W3C, SOAP, UDDI, | |
Secure hardware | Hardened appliance to | |||
| ||||
|
| |||
accelerated | comply with |
| No direct operating system access - encrypted hard drive - no internal | |
appliance | security standards | Secured appliance | devices allow for alternate | |
|
|
| configuration files digitally locked. | |
|
| Dedicated Web services | Hardware accelerated XML parsing & encryption with digital signing & SSL | |
|
| infrastructure | & HTTPS | |
|
|
|
|
3 | |
|
|