ipo or +O4 options are not specified. This may lead to a significant increase in the compile time in comparison to a build without the +wsecurity option. Using this option may cause the compiler to invoke optimizations other than those which are part of the
The problems detected include use of unsafe APIs, use of unsafe data length argument, unsafe loop exit condition, unsafe file path use, etc.
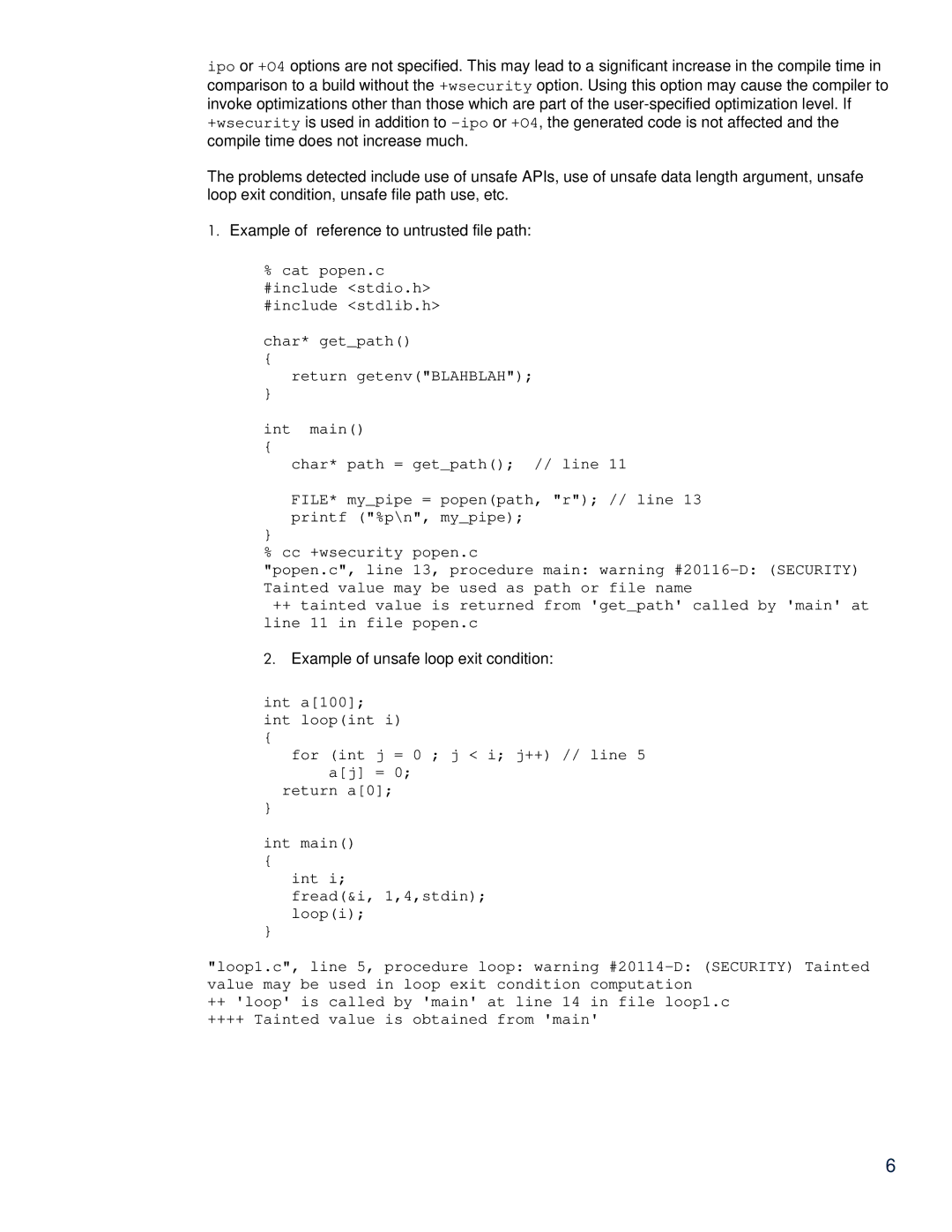
1.Example of reference to untrusted file path:
%cat popen.c #include <stdio.h> #include <stdlib.h>
char* get_path()
{
return getenv("BLAHBLAH");
}
int main()
{
char* path = get_path(); // line 11
FILE* my_pipe = popen(path, "r"); // line 13 printf ("%p\n", my_pipe);
}
% cc +wsecurity popen.c
"popen.c", line 13, procedure main: warning
++tainted value is returned from 'get_path' called by 'main' at line 11 in file popen.c
2.Example of unsafe loop exit condition:
int a[100]; int loop(int i)
{
for (int j = 0 ; j < i; j++) // line 5 a[j] = 0;
return a[0];
}
int main()
{
int i;
fread(&i, 1,4,stdin); loop(i);
}
"loop1.c", line 5, procedure loop: warning
++'loop' is called by 'main' at line 14 in file loop1.c
++++ Tainted value is obtained from 'main'
6