Authentication
SMH
SMH launches an instance of Tomcat for its exclusive use. Tomcat is used as a Java web application container within which SgmgrPI resides. For Java web applications, SMH acts as a web proxy; it redirects web requests for URLs belonging to SgmgrPI, which processes these requests and sends the responses back to HPSMH, which are forwarded back to the client.
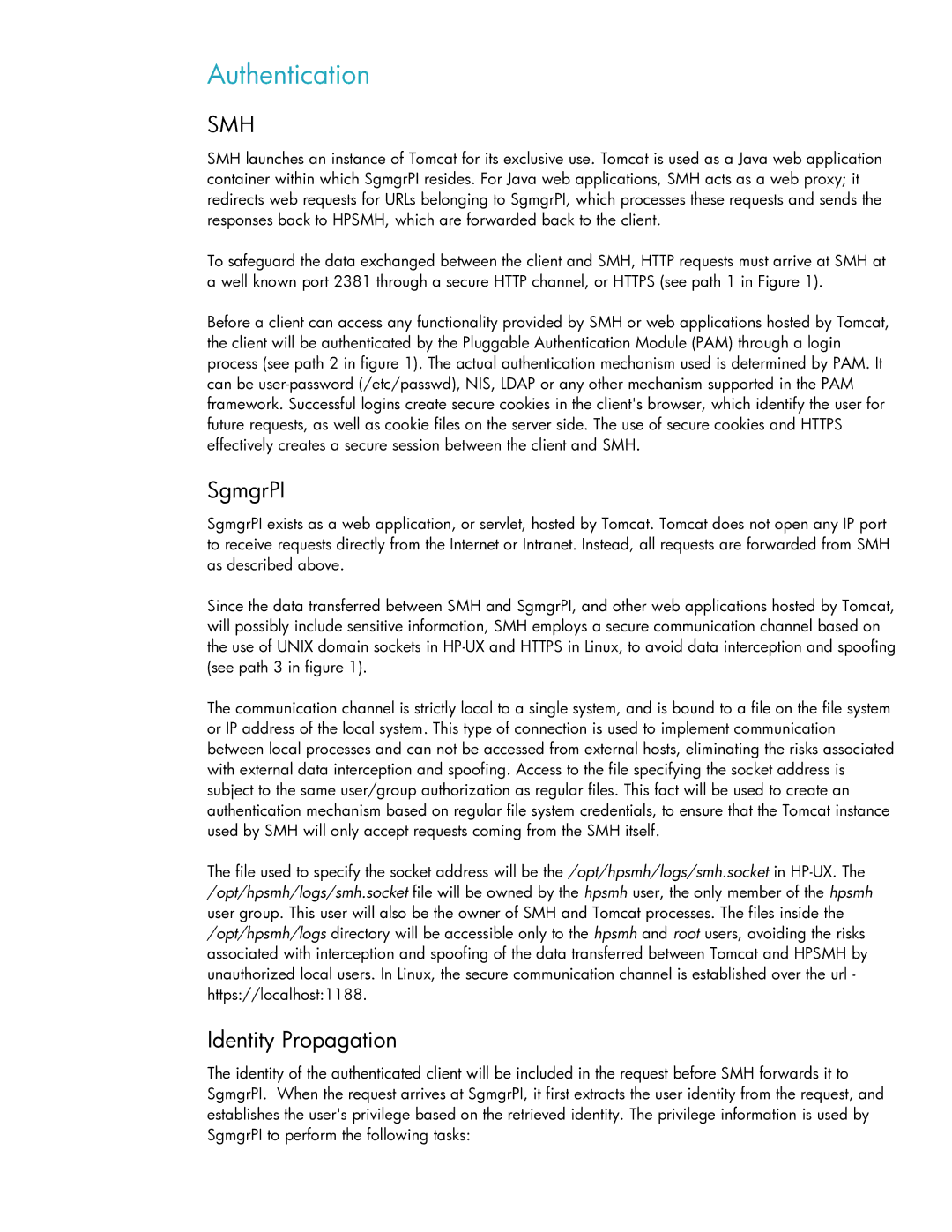
To safeguard the data exchanged between the client and SMH, HTTP requests must arrive at SMH at a well known port 2381 through a secure HTTP channel, or HTTPS (see path 1 in Figure 1).
Before a client can access any functionality provided by SMH or web applications hosted by Tomcat, the client will be authenticated by the Pluggable Authentication Module (PAM) through a login process (see path 2 in figure 1). The actual authentication mechanism used is determined by PAM. It can be
SgmgrPI
SgmgrPI exists as a web application, or servlet, hosted by Tomcat. Tomcat does not open any IP port to receive requests directly from the Internet or Intranet. Instead, all requests are forwarded from SMH as described above.
Since the data transferred between SMH and SgmgrPI, and other web applications hosted by Tomcat, will possibly include sensitive information, SMH employs a secure communication channel based on the use of UNIX domain sockets in
The communication channel is strictly local to a single system, and is bound to a file on the file system or IP address of the local system. This type of connection is used to implement communication between local processes and can not be accessed from external hosts, eliminating the risks associated with external data interception and spoofing. Access to the file specifying the socket address is subject to the same user/group authorization as regular files. This fact will be used to create an authentication mechanism based on regular file system credentials, to ensure that the Tomcat instance used by SMH will only accept requests coming from the SMH itself.
The file used to specify the socket address will be the /opt/hpsmh/logs/smh.socket in
Identity Propagation
The identity of the authenticated client will be included in the request before SMH forwards it to SgmgrPI. When the request arrives at SgmgrPI, it first extracts the user identity from the request, and establishes the user's privilege based on the retrieved identity. The privilege information is used by SgmgrPI to perform the following tasks: