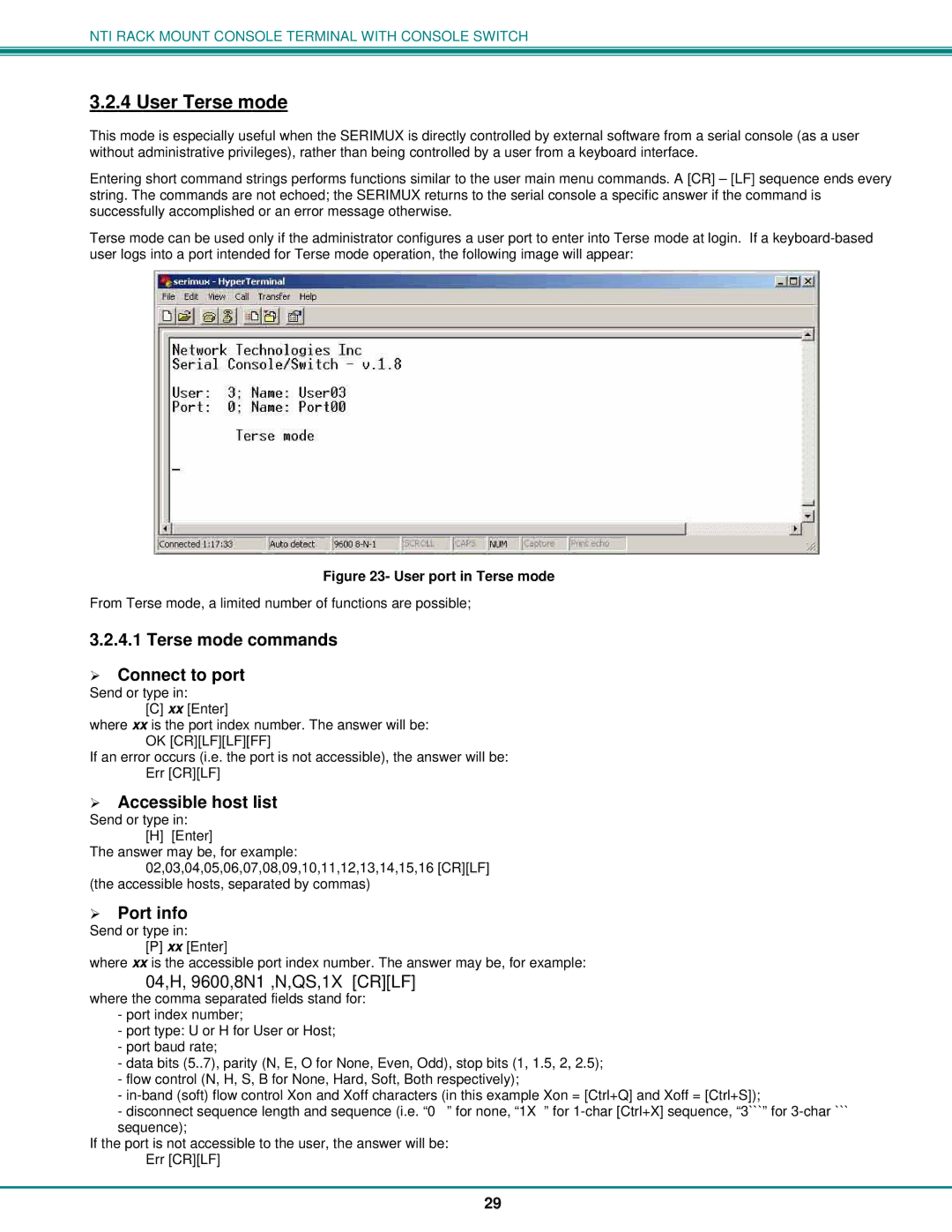
T15-RS16, 8 specifications
Network Technology 8, commonly referred to as T15-RS16, represents a significant advancement in the realm of telecommunication and data networking. This technology is designed to enhance the capabilities of network infrastructures, enabling higher data transfer rates, improved reliability, and greater scalability. As the demand for faster and more efficient data transfer continues to grow, T15-RS16 has emerged as a vital solution for various industries.One of the main features of T15-RS16 is its ability to support high-speed data transmission. This technology integrates advanced modulation techniques and signal processing algorithms that allow for data rates reaching up to several gigabits per second. This enables organizations to handle large volumes of data seamlessly, which is crucial for activities such as cloud computing, big data analytics, and real-time streaming services.
Another key characteristic of T15-RS16 is its robust error correction capabilities. The technology employs sophisticated error detection and correction mechanisms, ensuring that data integrity is maintained even in adverse conditions. This is particularly important for applications where accuracy is paramount, such as financial transactions and medical data transmission.
T15-RS16 also boasts scalability, making it an attractive option for both small enterprises and large corporations. It can easily adapt to the growing needs of businesses by allowing for the addition of more devices without compromising on performance. This future-proof aspect is essential in today's rapidly evolving technological landscape, where businesses seek to invest in solutions that can grow with them.
In terms of compatibility, T15-RS16 is designed to work seamlessly with existing network infrastructures. This allows organizations to upgrade their systems without needing to overhaul their entire network, providing significant cost savings. Moreover, the technology supports various networking standards, ensuring that it can easily integrate with multiple devices and platforms.
Security is another critical aspect of T15-RS16. This technology incorporates advanced encryption protocols that safeguard data against unauthorized access and cyber threats. Organizations can rely on T15-RS16 to ensure the confidentiality and security of their sensitive information.
In conclusion, Network Technology 8, or T15-RS16, offers a powerful combination of high-speed transmission, robust error correction, scalability, compatibility, and security. As organizations continue to embrace digital transformation, the need for efficient and reliable network technologies such as T15-RS16 becomes increasingly vital to meet the demands of modern computing and connectivity.