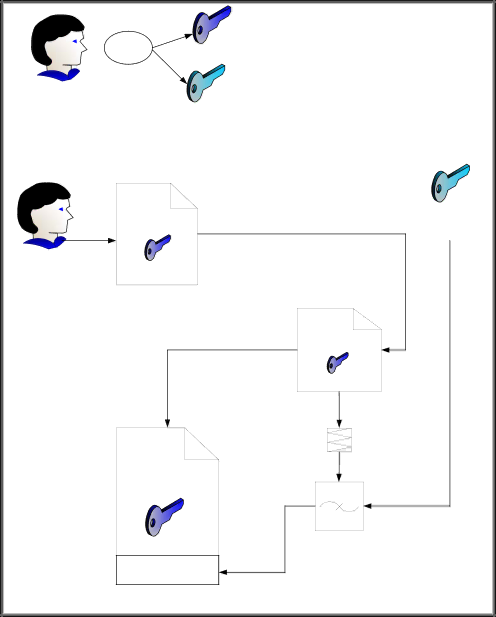
Create | Jack’s Public Key |
| |
Key Pair |
| ||
Jack |
|
| |
| Jack’s Private Key |
| |
Identity Info + | Jack’s Private Key | ||
(Stays Private) | |||
|
| ||
Jack |
|
| |
Jack’s Public Key |
| ||
|
| Identity Info + | |
|
| Jack’s Public Key | |
|
| Preliminary Certificate | |
Identity Info + | |||
| |||
Jack’s Public Key | Encryption | ||
Digital Signature |
| ||
Jack’s |
| ||
Certificate |
| ||
Figure 21 - Self-Signed Certificate
Basically, Jack’s private key does the signing on his public key certificate. A root (top of the chain) certificate authority is going to go through the same process. So why is it okay for a Root CA to have a
Also, we should take care to point out that there is usually a difference between Internet trust using certificates and Intranet trust using certificates. Internet trust will involve
There is one other important thing to cover about certificates. Each certificate has a one or more “certificate purposes” that the certificate can be used for. For example, a Jetdirect
19