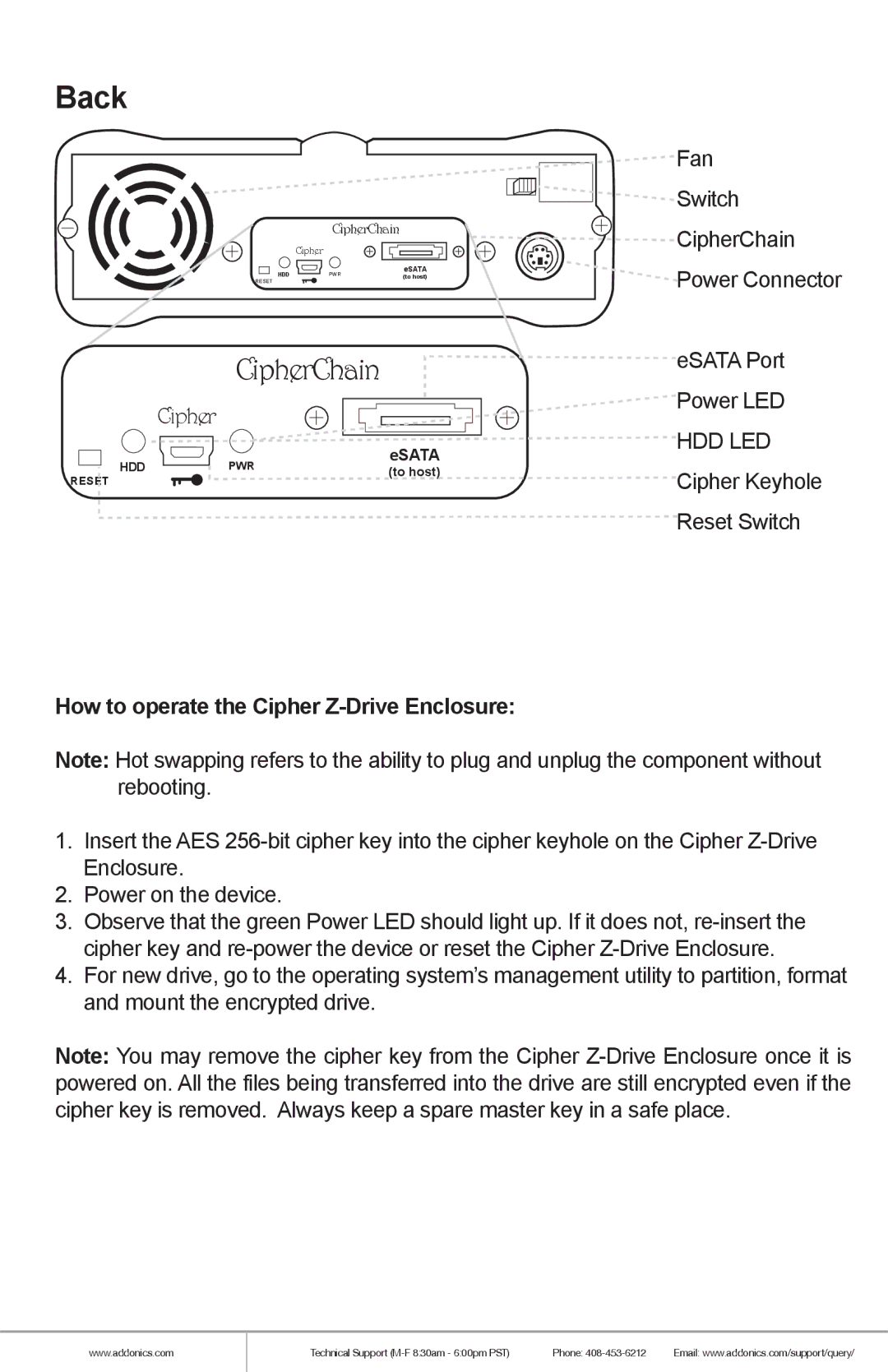
ZESAES256, ZSAES256EU specifications
Addonics Technologies has carved out a prominent niche in the realm of data security and storage solutions, with their offerings such as the ZESAES256 and ZSAES256EU exemplifying their commitment to high-performance cryptographic technology. These products primarily serve the purpose of securing sensitive data through advanced encryption standards, ensuring both confidentiality and integrity.The ZESAES256 and ZSAES256EU are built around the AES (Advanced Encryption Standard) algorithm, which is widely recognized for its strong security framework. The '256' in their names indicates that they utilize a 256-bit key length, which significantly enhances the level of security compared to shorter key lengths, making it nearly impervious to brute force attacks. This is especially critical for organizations that handle sensitive information, as data breaches can lead to severe financial and reputational damage.
One of the main features of these devices is their capability for high-speed encryption and decryption processes. This feature ensures that while data is being secured, it does not compromise system performance. The ZESAES256 and ZSAES256EU are engineered to provide seamless integration with various storage solutions, making them ideal for both enterprise-level applications and individual use.
Additionally, these products are designed with user-friendliness in mind. The interface is intuitive, allowing users to easily configure their encryption settings without the need for specialized technical knowledge. This accessibility is crucial for businesses that need to implement robust security measures quickly and efficiently.
In the realm of connectivity, both the ZESAES256 and ZSAES256EU support a variety of interfaces, enabling them to work with many types of storage devices, including hard drives, SSDs, and USB flash drives. This flexibility allows users to secure their data across different platforms, enhancing overall data protection strategies.
The physical design of these devices also reflects durability and reliability. Constructed with high-quality materials, they are built to withstand the rigors of both environmental conditions and daily usage. Their compact size adds to their appeal, making them an unobtrusive addition to any workspace.
In conclusion, Addonics Technologies' ZESAES256 and ZSAES256EU stand out as advanced solutions for data encryption, balancing security, performance, and ease of use. With their strong AES-256 encryption, fast processing speeds, and versatile connectivity options, these devices are indispensable for anyone looking to safeguard sensitive information in today’s digital landscape.