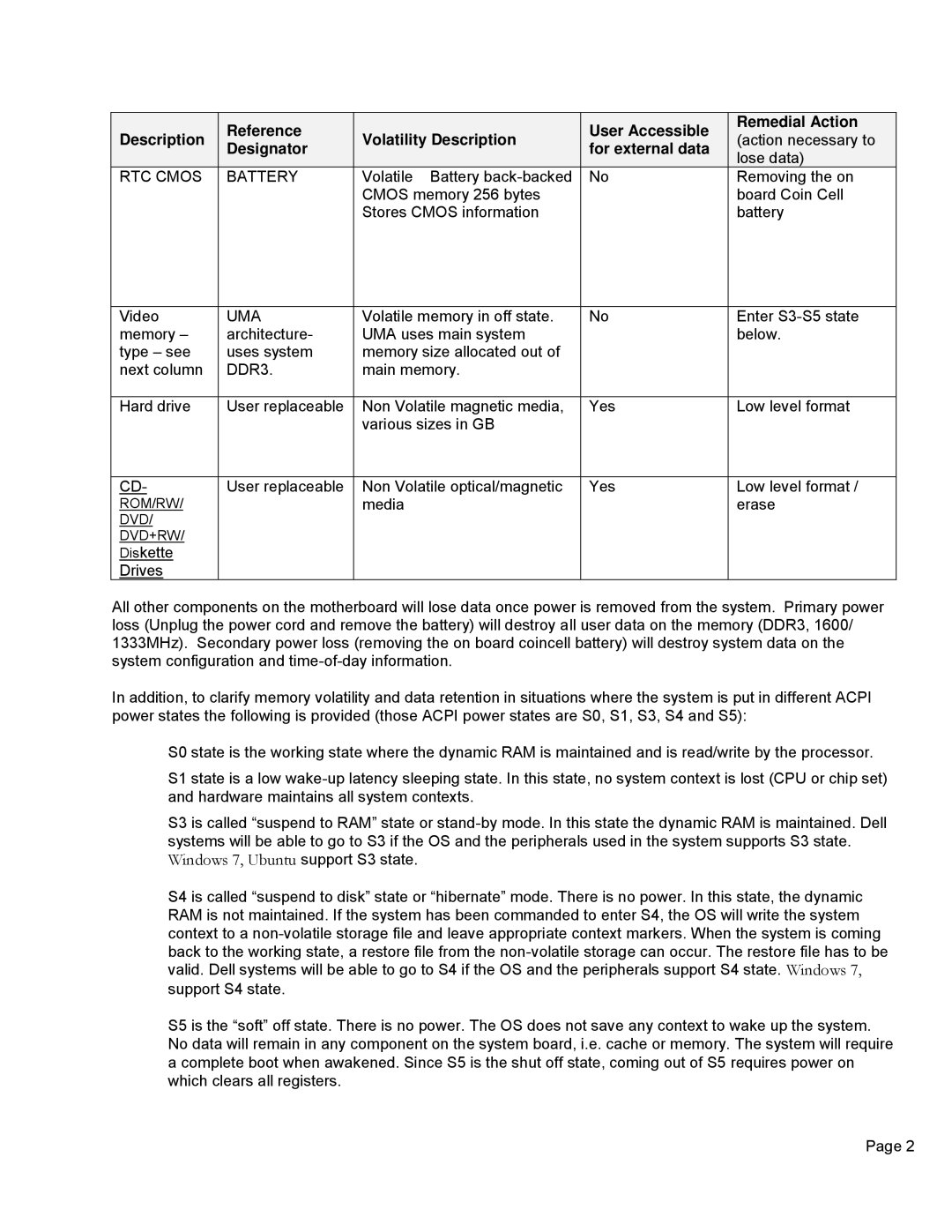
3010 specifications
The Dell PowerEdge T310 is a versatile tower server that is designed for small to medium-sized businesses looking for a reliable and efficient server solution. The T310 offers a range of features and technologies to meet various IT needs, making it a popular choice among businesses.One of the standout features of the Dell T310 is its robust processing power. It is equipped with Intel's Xeon processor, which delivers outstanding performance and energy efficiency. This multi-core architecture allows for enhanced multitasking capabilities, ensuring that businesses can run multiple applications simultaneously without degradation in performance.
In terms of memory, the T310 supports up to 32GB of DDR3 RAM, providing ample space for data-intensive tasks. This capacity makes it suitable for applications such as virtualization, database management, and file sharing, empowering organizations to operate more efficiently.
Storage options on the Dell PowerEdge T310 are also impressive. The server supports multiple hard drive configurations, including up to four 3.5-inch SATA or SAS drives. This scalability allows businesses to customize their storage solutions based on their specific requirements for data storage and retrieval. RAID configurations offer additional data protection and improved performance, ensuring that critical data is always safe.
The T310 also features advanced management technologies, including Dell's OpenManage systems management console. This tool provides IT administrators with the ability to monitor and manage systems with ease, enabling proactive maintenance and troubleshooting. This not only improves the server's uptime but also enhances overall operational efficiency.
Security is another critical aspect of the T310 design. Equipped with features such as a Trusted Platform Module (TPM) and system lock, the server provides robust protection against unauthorized access. These security features ensure that sensitive business data remains protected from potential threats.
Furthermore, the Dell PowerEdge T310 has a compact form factor, making it an excellent choice for businesses with limited space. Its quiet operation and efficient cooling system allow it to blend seamlessly into office environments without causing disturbances.
In conclusion, the Dell PowerEdge T310 is a powerful, flexible, and secure server that caters to the needs of small to medium-sized businesses. With its advanced processing capabilities, significant memory capacity, versatile storage options, and strong management features, the T310 stands out as a reliable solution for various IT demands. Its combination of performance, scalability, and security makes it an ideal choice for businesses looking to enhance their IT infrastructure.