Create | Jack’s Public Key |
|
|
Key Pair |
|
| |
Jack |
|
|
|
| Jack’s Private Key |
|
|
|
|
| CA’s Public Key |
Identity Info + |
|
| |
Jack |
| Certificate Authority | CA’s Private Key |
Jack’s Public Key | |||
| (Also performs Identity Verification on Jack) | ||
Certificate Request |
|
| |
Jack’s Private Key |
|
|
|
(Stays Private) |
| Identity Info + |
|
|
|
| |
|
| CA Info + |
|
|
| Jack’s Public Key |
|
|
| Preliminary Certificate |
|
Identity Info + | |||
|
| ||
CA Info + |
|
| |
Jack’s Public Key | Encryption |
| |
CA’s Digital |
|
| |
Signature |
|
| |
Jack’s Public Key |
|
| |
Certificate |
|
| |
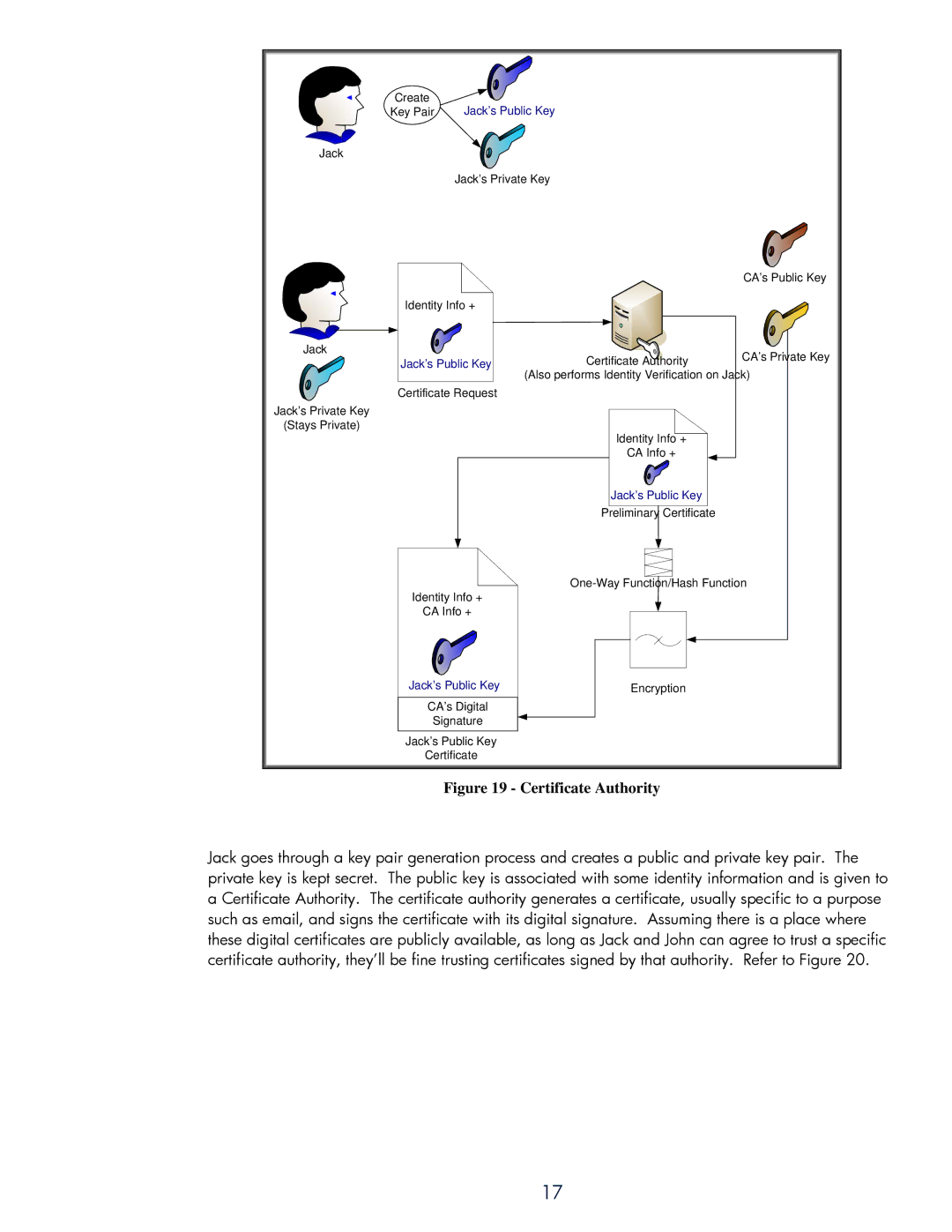
Figure 19 - Certificate Authority
Jack goes through a key pair generation process and creates a public and private key pair. The private key is kept secret. The public key is associated with some identity information and is given to a Certificate Authority. The certificate authority generates a certificate, usually specific to a purpose such as email, and signs the certificate with its digital signature. Assuming there is a place where these digital certificates are publicly available, as long as Jack and John can agree to trust a specific certificate authority, they’ll be fine trusting certificates signed by that authority. Refer to Figure 20.
17