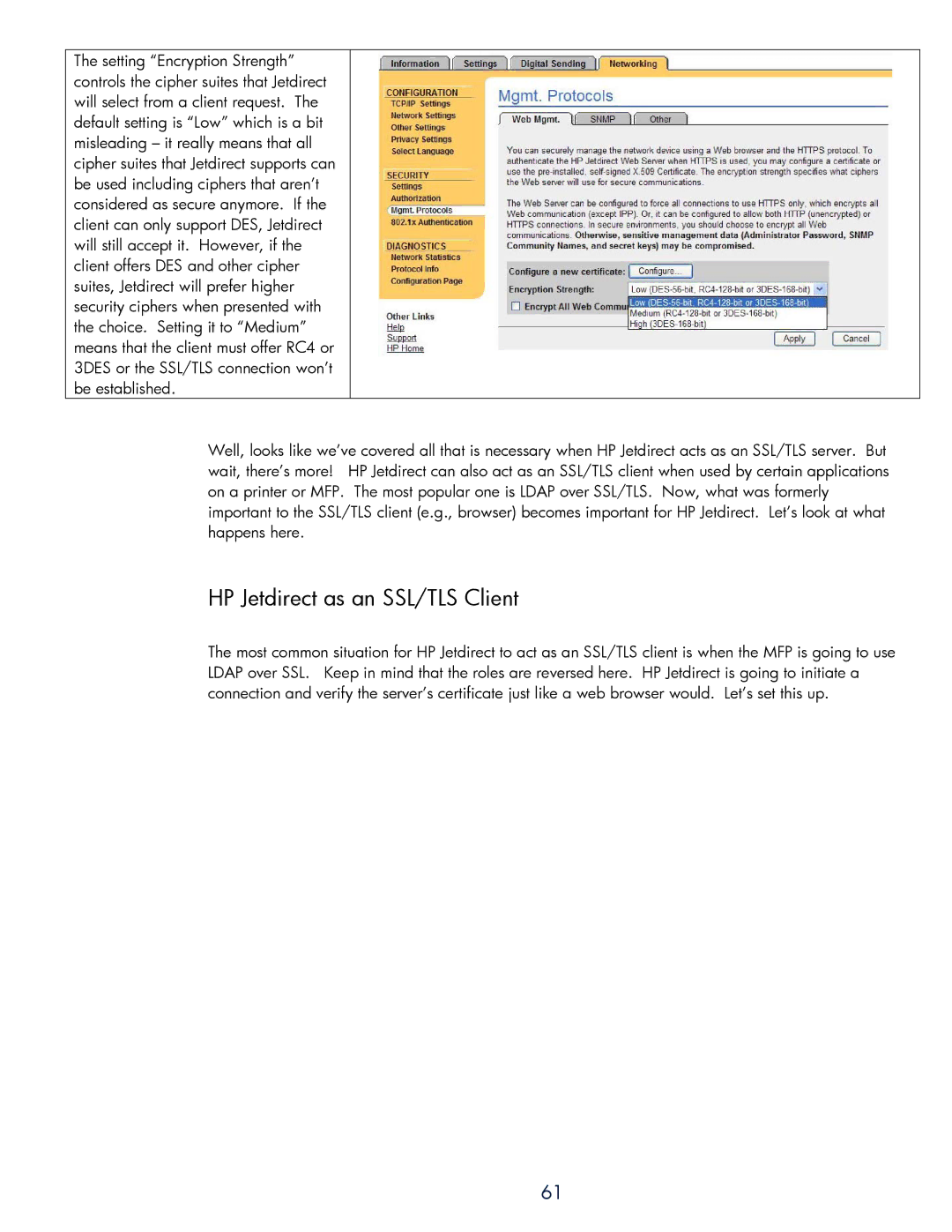
The setting “Encryption Strength” controls the cipher suites that Jetdirect will select from a client request. The default setting is “Low” which is a bit misleading – it really means that all cipher suites that Jetdirect supports can be used including ciphers that aren’t considered as secure anymore. If the client can only support DES, Jetdirect will still accept it. However, if the client offers DES and other cipher suites, Jetdirect will prefer higher security ciphers when presented with the choice. Setting it to “Medium” means that the client must offer RC4 or 3DES or the SSL/TLS connection won’t be established.
Well, looks like we’ve covered all that is necessary when HP Jetdirect acts as an SSL/TLS server. But wait, there’s more! HP Jetdirect can also act as an SSL/TLS client when used by certain applications on a printer or MFP. The most popular one is LDAP over SSL/TLS. Now, what was formerly important to the SSL/TLS client (e.g., browser) becomes important for HP Jetdirect. Let’s look at what happens here.
HP Jetdirect as an SSL/TLS Client
The most common situation for HP Jetdirect to act as an SSL/TLS client is when the MFP is going to use LDAP over SSL. Keep in mind that the roles are reversed here. HP Jetdirect is going to initiate a connection and verify the server’s certificate just like a web browser would. Let’s set this up.
61