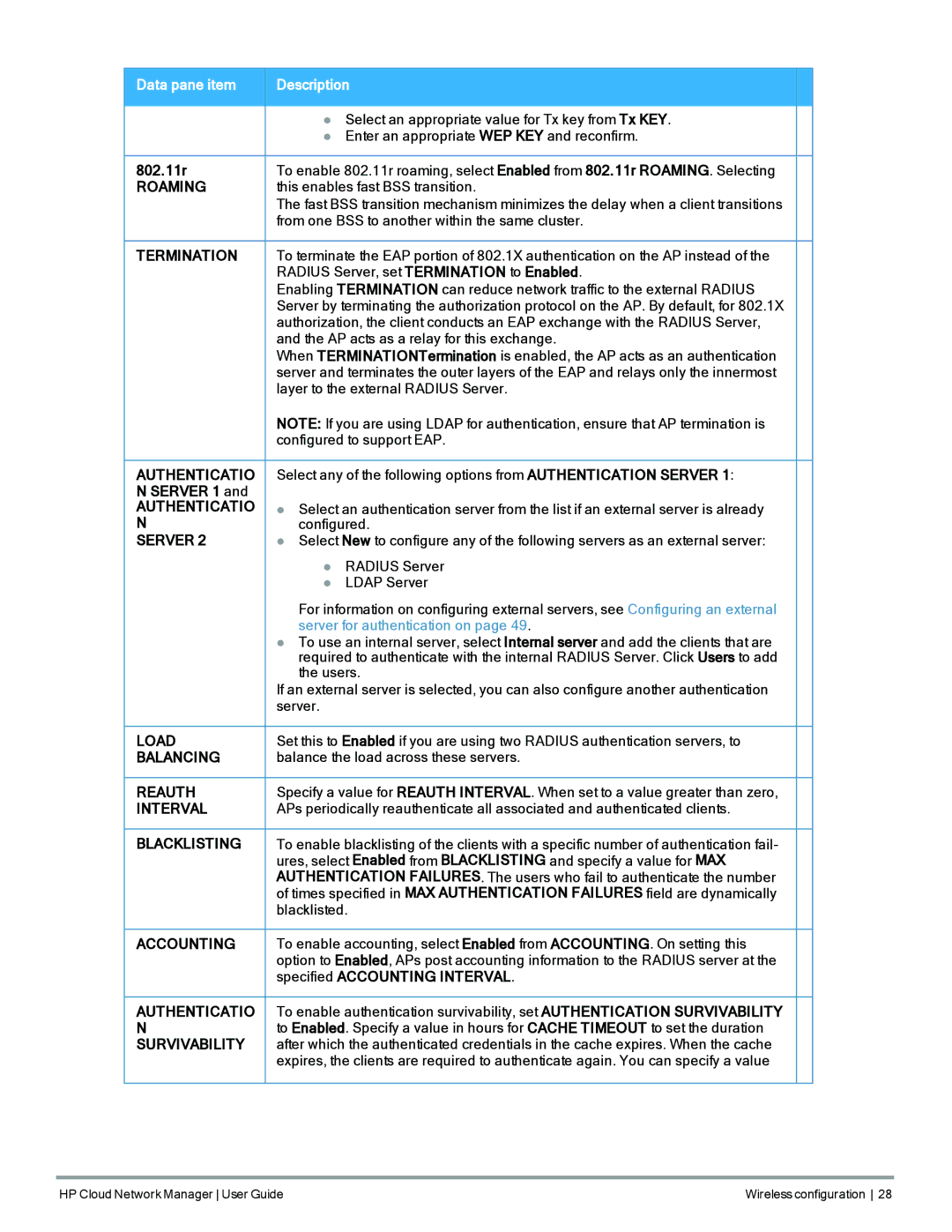
Cloud Network Manager Software specifications
HP Cloud Network Manager is a robust software solution designed to simplify and enhance the management of network infrastructure in cloud environments. As organizations increasingly shift toward cloud computing, they require comprehensive tools to oversee complex network deployments. HP Cloud Network Manager rises to this challenge, offering a powerful suite of features aimed at optimizing performance, automating tasks, and ensuring reliable connectivity.One of the main features of HP Cloud Network Manager is its intuitive dashboard, which provides users with real-time insights into network operations. This centralized interface allows administrators to monitor the status of various components, identify potential issues, and respond swiftly to anomalies. With advanced analytics capabilities, the software empowers users to make data-driven decisions that enhance network efficiency.
Another critical feature of this software is its automation capabilities. HP Cloud Network Manager simplifies routine network management tasks, such as configuration, provisioning, and software updates, allowing IT teams to focus on strategic initiatives rather than mundane maintenance. Automation reduces the risk of human error and accelerates deployment times, significantly increasing operational agility.
The software also supports multi-cloud environments, enabling organizations to manage their network resources across different cloud platforms seamlessly. This flexibility is essential for businesses that utilize various cloud providers and wish to maintain a unified network strategy. Coupled with its compatibility with open standards, HP Cloud Network Manager facilitates integration with existing IT ecosystems, ensuring a smooth transition to advanced cloud solutions.
Security is a top priority in today's digital landscape, and HP Cloud Network Manager includes integrated security features to protect network assets. It provides visibility into traffic patterns, helping to detect and mitigate potential threats before they become significant issues. Enhanced security protocols ensure that sensitive data remains protected during transit and at rest, aligning with compliance requirements.
Finally, HP Cloud Network Manager is built on cutting-edge technologies, including artificial intelligence and machine learning, which enable proactive network management. These technologies predict network behavior, assisting administrators in optimizing resources and anticipating potential challenges. As a result, organizations can achieve enhanced reliability and performance from their network infrastructure.
In summary, HP Cloud Network Manager is an essential tool for businesses looking to improve their cloud network management capabilities. With its powerful features, supportive technologies, and commitment to security, it stands out as a reliable solution for navigating the complexities of modern network environments.