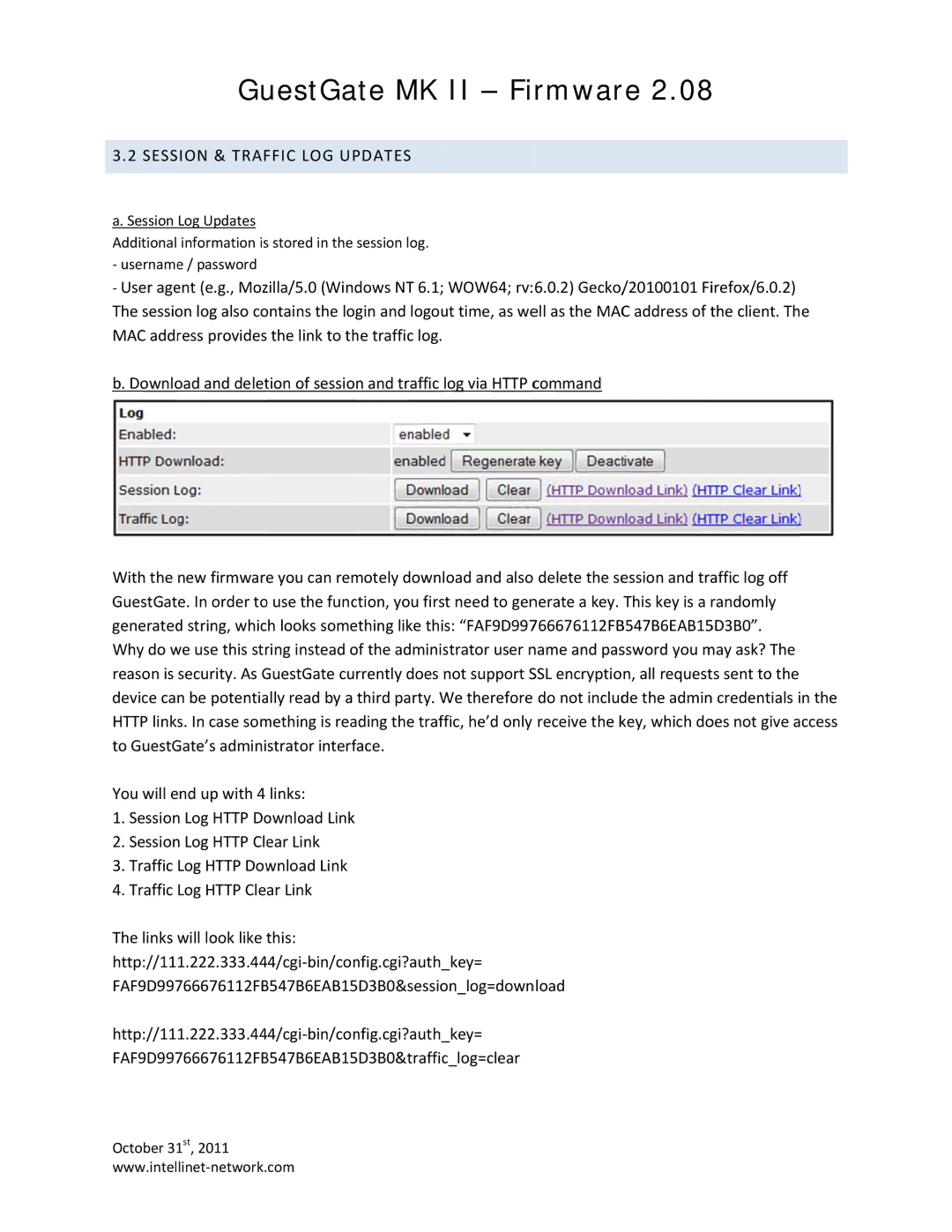
MK II specifications
Intellinet Network Solutions MK II is an advanced networking device designed to address the demands of modern communication technologies. This next-generation solution builds upon the strengths of its predecessor, offering enhanced performance, scalability, and security features suitable for a variety of networking environments.One of the hallmark features of the MK II is its support for high-speed data processing, facilitating rapid data transfer rates that are essential for businesses reliant on real-time communication and data sharing. With Gigabit Ethernet capabilities, the MK II can efficiently manage large volumes of traffic while maintaining optimal performance. This design ensures that organizations can easily scale their operations without encountering performance bottlenecks.
The MK II incorporates advanced routing protocols, such as OSPF and BGP, allowing for dynamic routing capabilities that adapt to network changes. This flexibility ensures improved network resilience and redundancy. In cases of link failure or network congestion, the device can reroute traffic seamlessly, thereby minimizing downtime and preserving user experience.
Security is another critical aspect of the Intellinet MK II. It integrates robust firewall features alongside intrusion detection and prevention systems. These security measures are crucial in safeguarding sensitive data against unauthorized access and cyber threats. The MK II also supports secure VPN connections, enabling remote employees to access the corporate network safely and efficiently.
In addition to these features, the MK II supports the latest wireless technologies, including Wi-Fi 6, which enhances connectivity and performance for mobile devices. This compatibility is particularly beneficial for organizations looking to implement smart offices and IoT solutions, as it provides a more reliable and faster wireless experience.
With an intuitive management interface, network administrators can efficiently monitor performance metrics, configure settings, and respond to issues in real-time. This accessibility streamlines operations and facilitates better decision-making regarding network management and optimization.
In summary, the Intellinet Network Solutions MK II stands out with its high-speed data processing, advanced routing protocols, robust security features, and support for modern wireless technologies. Its user-friendly management interface further enhances its appeal, making it a comprehensive solution for businesses seeking improved networking capabilities.