TL-R600VPN SafeStream Gigabit Broadband VPN Router User Guide
TM
43
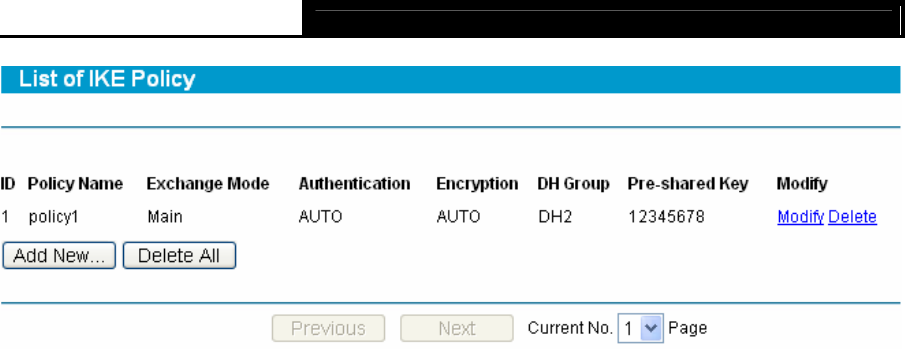
Figure 4-38
¾ Policy Name: The unique name to the IKE policy for identification and management
purposes.
¾ Exchange Mode: Displays the IKE Exchange Mode in phase 1, and the remote VPN peer
uses the same mode.
z Main: Main mode provides identity protection and exchanges more information,
which applies to the scenarios with higher requirement for identity protection.
z Aggressive: Aggressive Mode establishes a faster connection but with lower
security, which applies to scenarios with lower requirement for identity protection.
¾ Authentication: The authentication algorithm for IKE negotiation. Options include:
z MD5: MD5 (Message Digest Algorithm) takes a message of arbitrary length and
generates a 128-bit message digest.
z SHA1: SHA1 (Secure Hash Algorithm) takes a message less than 2^64 (the 64th
power of 2) in bits and generates a 160-bit message digest.
¾ Encryption: The encryption algorithm for IKE negotiation. Options include:
z DES: DES (Data Encryption Standard) encrypts a 64-bit block of plain text with a
56-bit key.
z 3DES: Triple DES, encrypts a plain text with 168-bit key.
z AES128: Uses the AES algorithm and 128-bit key for encryption.
z AES192: Uses the AES algorithm and 192-bit key for encryption.
z AES256: Uses the AES algorithm and 256-bit key for encryption.
¾ DH Group: The DH (Diffie-Hellman) group to be used in key negotiation phase 1. The DH
Group sets the strength of the algorithm in bits. Options include DH1, DH2 and DH5.
z DH1: 768 bits
z DH2: 1024 bits