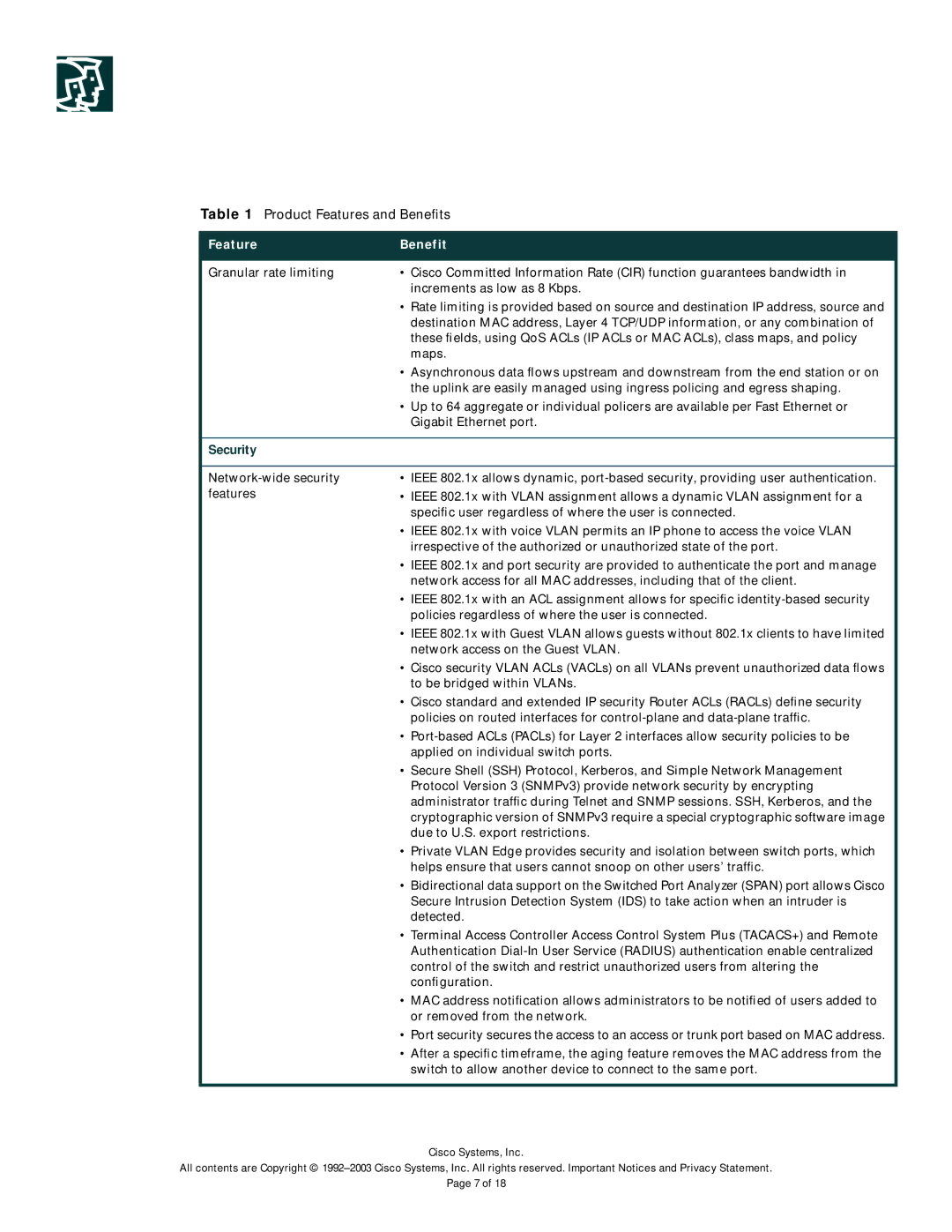
Table 1 Product Features and Benefits
Feature | Benefit |
|
|
Granular rate limiting | • Cisco Committed Information Rate (CIR) function guarantees bandwidth in |
| increments as low as 8 Kbps. |
| • Rate limiting is provided based on source and destination IP address, source and |
| destination MAC address, Layer 4 TCP/UDP information, or any combination of |
| these fields, using QoS ACLs (IP ACLs or MAC ACLs), class maps, and policy |
| maps. |
| • Asynchronous data flows upstream and downstream from the end station or on |
| the uplink are easily managed using ingress policing and egress shaping. |
| • Up to 64 aggregate or individual policers are available per Fast Ethernet or |
| Gigabit Ethernet port. |
Security
•IEEE 802.1x allows dynamic,
•IEEE 802.1x with VLAN assignment allows a dynamic VLAN assignment for a specific user regardless of where the user is connected.
•IEEE 802.1x with voice VLAN permits an IP phone to access the voice VLAN irrespective of the authorized or unauthorized state of the port.
•IEEE 802.1x and port security are provided to authenticate the port and manage network access for all MAC addresses, including that of the client.
•IEEE 802.1x with an ACL assignment allows for specific
•IEEE 802.1x with Guest VLAN allows guests without 802.1x clients to have limited network access on the Guest VLAN.
•Cisco security VLAN ACLs (VACLs) on all VLANs prevent unauthorized data flows to be bridged within VLANs.
•Cisco standard and extended IP security Router ACLs (RACLs) define security policies on routed interfaces for
•
•Secure Shell (SSH) Protocol, Kerberos, and Simple Network Management Protocol Version 3 (SNMPv3) provide network security by encrypting administrator traffic during Telnet and SNMP sessions. SSH, Kerberos, and the cryptographic version of SNMPv3 require a special cryptographic software image due to U.S. export restrictions.
•Private VLAN Edge provides security and isolation between switch ports, which helps ensure that users cannot snoop on other users’ traffic.
•Bidirectional data support on the Switched Port Analyzer (SPAN) port allows Cisco Secure Intrusion Detection System (IDS) to take action when an intruder is detected.
•Terminal Access Controller Access Control System Plus (TACACS+) and Remote Authentication
•MAC address notification allows administrators to be notified of users added to or removed from the network.
•Port security secures the access to an access or trunk port based on MAC address.
•After a specific timeframe, the aging feature removes the MAC address from the switch to allow another device to connect to the same port.
Cisco Systems, Inc.
All contents are Copyright ©
Page 7 of 18