Cryptographic Key Management
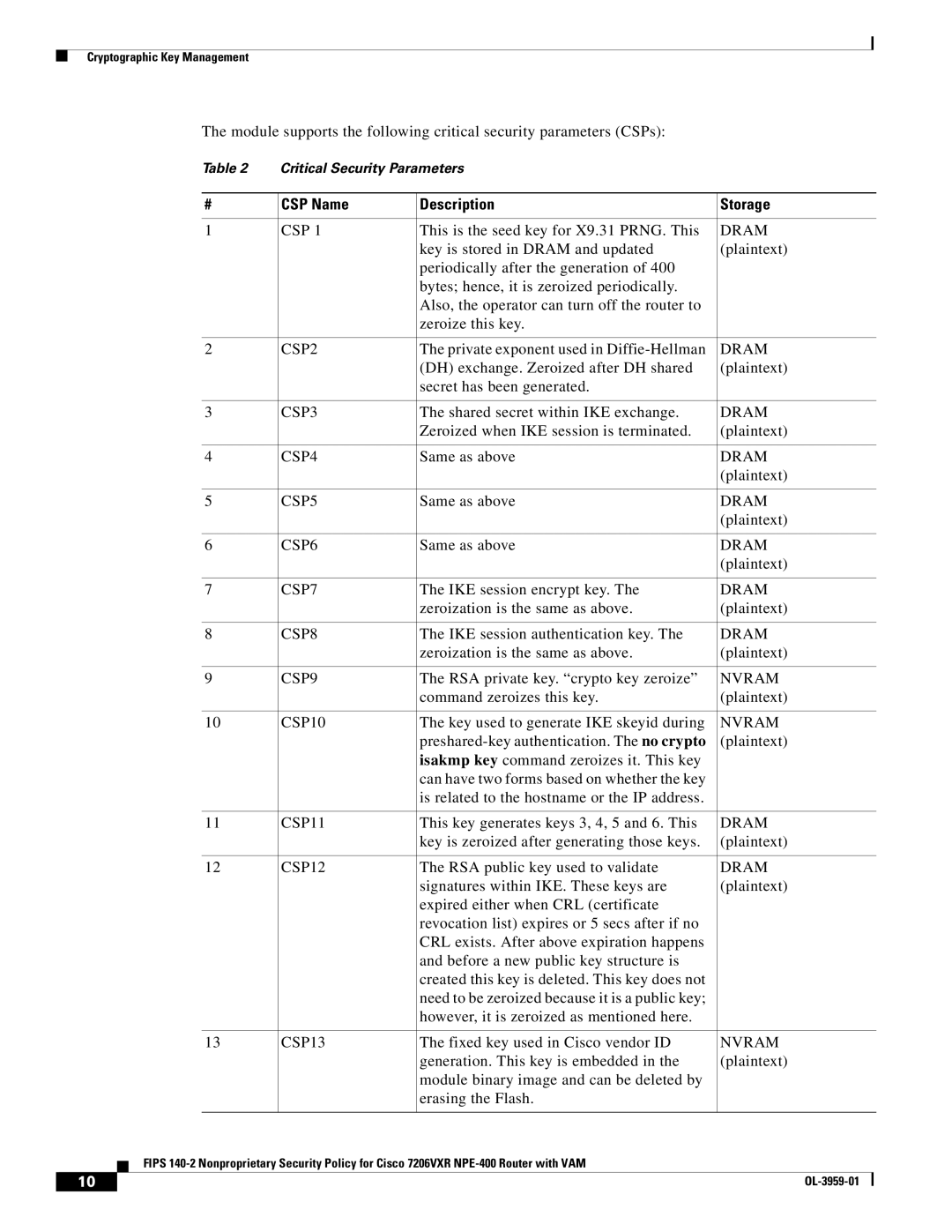
The module supports the following critical security parameters (CSPs):
|
|
|
| Table 2 | Critical Security Parameters |
|
| |
|
|
|
|
|
| |||
# | CSP Name | Description | Storage |
| ||||
|
|
|
|
|
| |||
1 | CSP 1 | This is the seed key for X9.31 PRNG. This | DRAM |
| ||||
|
|
|
|
|
| key is stored in DRAM and updated | (plaintext) |
|
|
|
|
|
|
| periodically after the generation of 400 |
|
|
|
|
|
|
|
| bytes; hence, it is zeroized periodically. |
|
|
|
|
|
|
|
| Also, the operator can turn off the router to |
|
|
|
|
|
|
|
| zeroize this key. |
|
|
|
|
|
|
|
| |||
2 | CSP2 | The private exponent used in | DRAM |
| ||||
|
|
|
|
|
| (DH) exchange. Zeroized after DH shared | (plaintext) |
|
|
|
|
|
|
| secret has been generated. |
|
|
|
|
|
|
|
| |||
3 | CSP3 | The shared secret within IKE exchange. | DRAM |
| ||||
|
|
|
|
|
| Zeroized when IKE session is terminated. | (plaintext) |
|
|
|
|
|
|
| |||
4 | CSP4 | Same as above | DRAM |
| ||||
|
|
|
|
|
|
| (plaintext) |
|
|
|
|
|
|
| |||
5 | CSP5 | Same as above | DRAM |
| ||||
|
|
|
|
|
|
| (plaintext) |
|
|
|
|
|
|
| |||
6 | CSP6 | Same as above | DRAM |
| ||||
|
|
|
|
|
|
| (plaintext) |
|
|
|
|
|
|
| |||
7 | CSP7 | The IKE session encrypt key. The | DRAM |
| ||||
|
|
|
|
|
| zeroization is the same as above. | (plaintext) |
|
|
|
|
|
|
| |||
8 | CSP8 | The IKE session authentication key. The | DRAM |
| ||||
|
|
|
|
|
| zeroization is the same as above. | (plaintext) |
|
|
|
|
|
|
| |||
9 | CSP9 | The RSA private key. “crypto key zeroize” | NVRAM |
| ||||
|
|
|
|
|
| command zeroizes this key. | (plaintext) |
|
|
|
|
|
|
| |||
10 | CSP10 | The key used to generate IKE skeyid during | NVRAM |
| ||||
|
|
|
|
|
| (plaintext) |
| |
|
|
|
|
|
| isakmp key command zeroizes it. This key |
|
|
|
|
|
|
|
| can have two forms based on whether the key |
|
|
|
|
|
|
|
| is related to the hostname or the IP address. |
|
|
|
|
|
|
|
| |||
11 | CSP11 | This key generates keys 3, 4, 5 and 6. This | DRAM |
| ||||
|
|
|
|
|
| key is zeroized after generating those keys. | (plaintext) |
|
|
|
|
|
|
| |||
12 | CSP12 | The RSA public key used to validate | DRAM |
| ||||
|
|
|
|
|
| signatures within IKE. These keys are | (plaintext) |
|
|
|
|
|
|
| expired either when CRL (certificate |
|
|
|
|
|
|
|
| revocation list) expires or 5 secs after if no |
|
|
|
|
|
|
|
| CRL exists. After above expiration happens |
|
|
|
|
|
|
|
| and before a new public key structure is |
|
|
|
|
|
|
|
| created this key is deleted. This key does not |
|
|
|
|
|
|
|
| need to be zeroized because it is a public key; |
|
|
|
|
|
|
|
| however, it is zeroized as mentioned here. |
|
|
|
|
|
|
|
| |||
13 | CSP13 | The fixed key used in Cisco vendor ID | NVRAM |
| ||||
|
|
|
|
|
| generation. This key is embedded in the | (plaintext) |
|
|
|
|
|
|
| module binary image and can be deleted by |
|
|
|
|
|
|
|
| erasing the Flash. |
|
|
|
|
|
|
|
|
|
|
|
|
|
| FIPS |
|
| |||
|
|
|
|
| ||||
|
|
|
|
|
|
|
|
|
| 10 |
|
|
|
|
|
| |
|
|
|
|
|
|
| ||