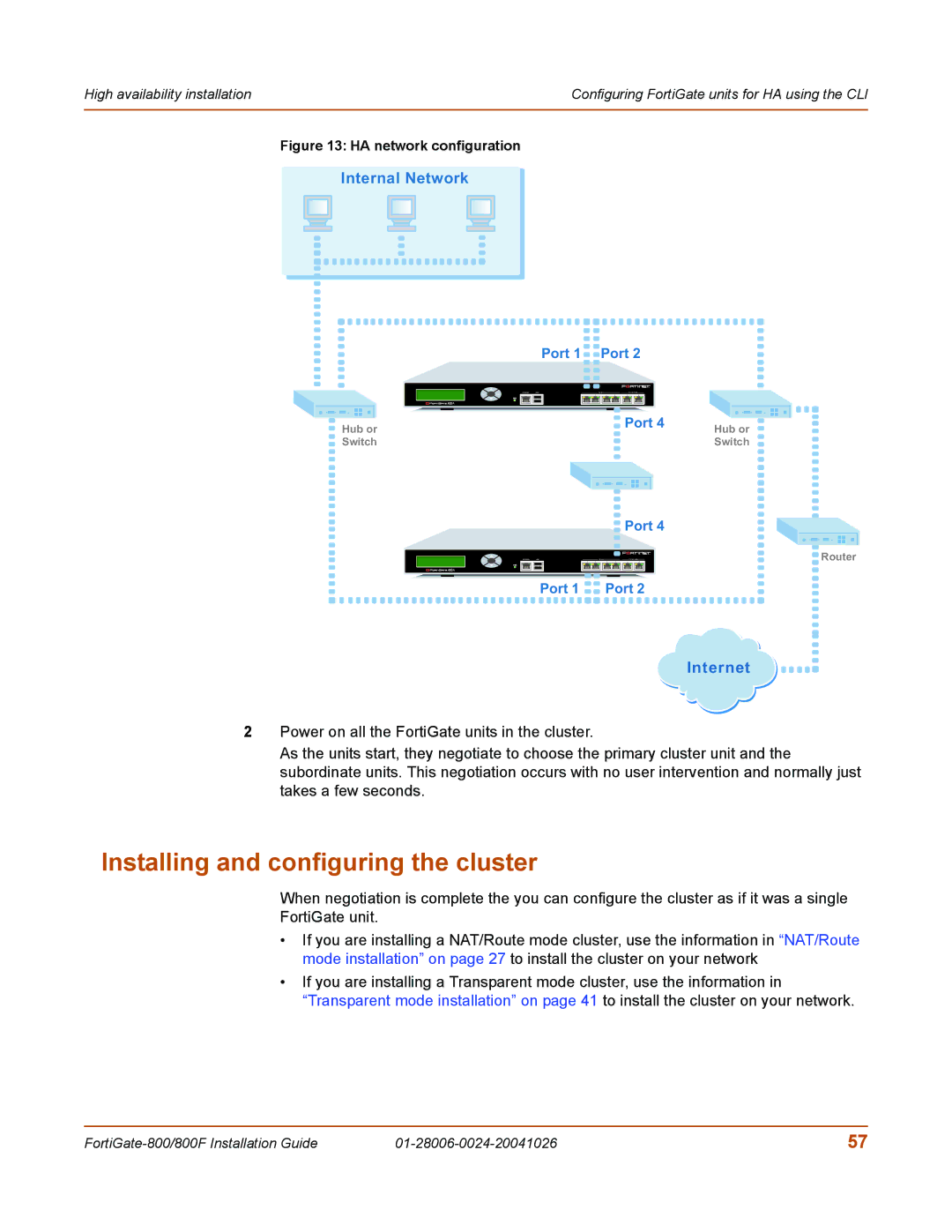
800F, 800 specifications
Fortinet, a leader in cybersecurity solutions, has made significant strides in fortifying enterprise networks with its FortiGate 800 and 800F series. These next-generation firewalls are designed to deliver high performance and security for organizations seeking to protect their critical assets while ensuring optimal network efficiency.The FortiGate 800 and 800F series are built on Fortinet's proprietary Security Fabric architecture, which provides a consolidated approach to security. This architecture allows organizations to leverage seamless integration across various security solutions and services, enhancing visibility and control. With a focus on scalability, these models support various deployment scenarios—from branch offices to data centers—making them versatile options for organizations of any size.
One of the standout features of the FortiGate 800 and 800F series is their robust threat intelligence capabilities. Powered by FortiGuard Labs, these firewalls provide real-time threat intelligence that enables proactive threat mitigation and incident response. This not only helps to defend against known threats but also enhances the firewall’s ability to identify emerging threats, ensuring comprehensive protection.
The series boasts impressive performance metrics. The FortiGate 800F can process up to 20 Gbps of firewall throughput and 1.5 million concurrent sessions, making it a suitable choice for high-performance environments. Additionally, the built-in SSL inspection capabilities allow organizations to decrypt and inspect encrypted traffic, which is crucial for detecting hidden threats.
The FortiGate 800 and 800F also feature advanced security technologies, including Intrusion Prevention System (IPS), antivirus, web filtering, and application control, all managed through a unified interface. This centralization simplifies management and reduces administrative overhead, allowing IT teams to focus on strategic initiatives.
Another significant characteristic of the FortiGate 800F is its energy efficiency. The design includes hardware optimizations that not only enhance performance but also reduce power consumption, aligning with the growing emphasis on sustainability practices.
In summary, the Fortinet FortiGate 800 and 800F series are comprehensive network security solutions that leverage advanced technologies to provide organizations with the security, performance, and flexibility necessary in today's threat landscape. With their robust threat intelligence and high throughput capabilities, these firewalls are well-suited for enterprises looking to fortify their defenses against an ever-evolving array of cyber threats.