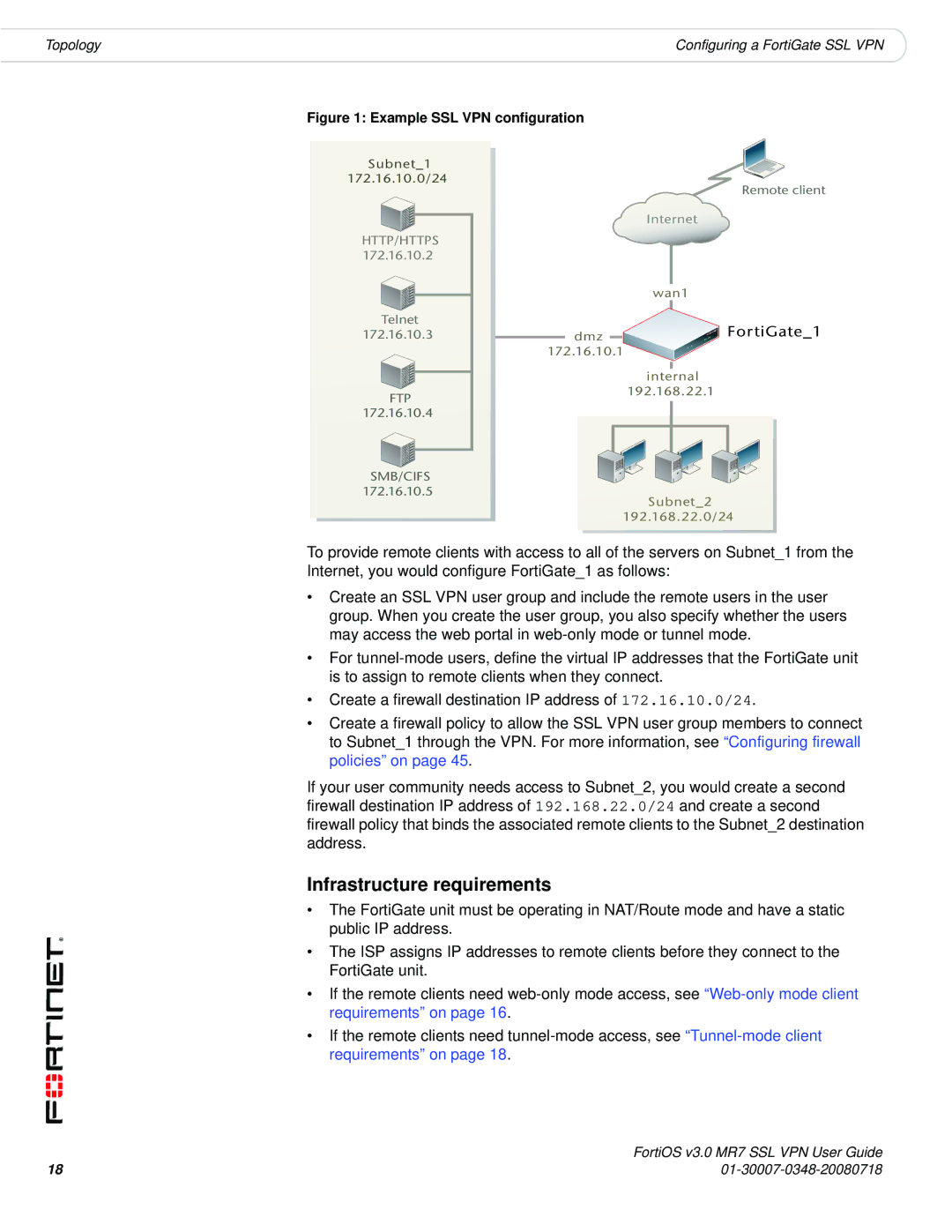
FORTIOS V3.0 MR7 specifications
Fortinet's FortiOS v3.0 MR7 marks a significant advancement in network security and management, providing organizations with enhanced features, technologies, and characteristics to better protect their IT environments. This version of FortiOS is designed to facilitate comprehensive security and optimized performance, ensuring that organizations can safeguard their networks against evolving threats.One of the main features in FortiOS v3.0 MR7 is its robust firewall capabilities. The stateful firewall technology enables dynamic packet filtering based on predefined security policies. This strengthens the organization's perimeter defense by allowing or denying traffic based on user-defined rules. Additionally, the integrated Application Control feature extends the firewall's capabilities by identifying and controlling applications regardless of port usage, enabling organizations to enforce security policies on a finer-grained level.
FortiOS v3.0 MR7 also introduces advanced intrusion prevention system (IPS) functionalities. The next-generation IPS utilizes deep packet inspection and real-time threat intelligence to detect and block attacks before they can compromise the network. Coupled with Fortinet’s threat research team, which ensures timely updates of security signatures, this system helps organizations mitigate risks posed by sophisticated cyber threats.
Another key characteristic of FortiOS v3.0 MR7 is its enhanced VPN capabilities. The support for both SSL and IPsec VPN allows secure remote access for employees and offers flexible options for secure communication over the internet. This feature is essential for organizations that embrace remote work, ensuring that sensitive data remains protected regardless of the user's location.
In addition to its powerful security features, FortiOS v3.0 MR7 includes advanced reporting and logging capabilities. Users can generate detailed reports that highlight security events, traffic patterns, and performance metrics. This data not only improves visibility into network security but also assists in compliance with regulatory requirements.
Moreover, the platform's user-friendly interface enhances the overall management experience. Administrators can quickly configure settings, monitor activity, and respond to incidents effectively. With centralized management capabilities, FortiOS v3.0 MR7 allows organizations to manage multiple devices from a single console, simplifying operations and reducing administrative overhead.
In summary, Fortinet's FortiOS v3.0 MR7 integrates a wealth of security features, including a stateful firewall, advanced IPS, VPN support, and comprehensive reporting functions. Together, these technologies ensure that organizations can maintain a strong security posture in an increasingly complex threat landscape.