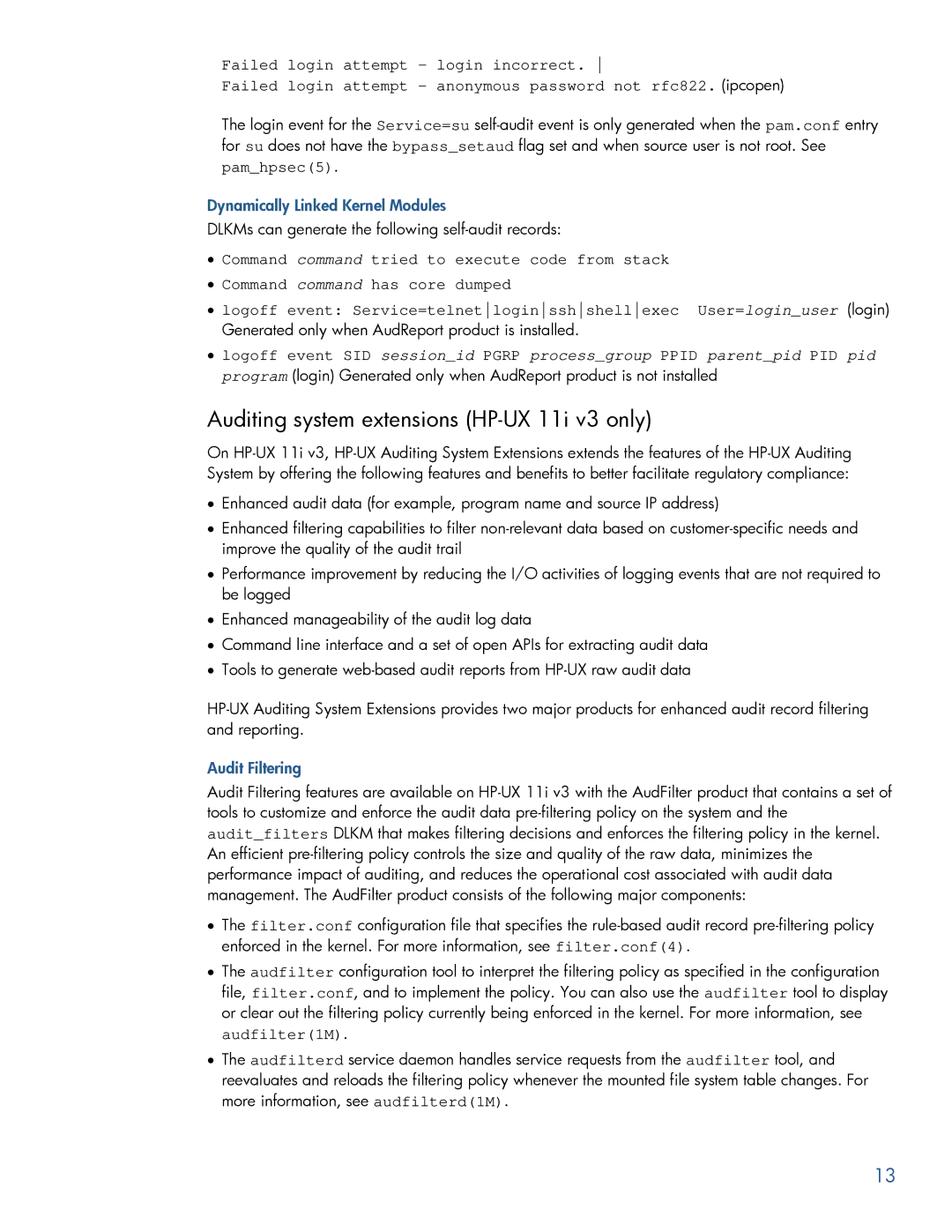
Failed login attempt - login incorrect.
Failed login attempt - anonymous password not rfc822. (ipcopen)
The login event for the Service=su
Dynamically Linked Kernel Modules
DLKMs can generate the following
•Command command tried to execute code from stack
•Command command has core dumped
•logoff event: Service=telnetloginsshshellexec User=login_user (login) Generated only when AudReport product is installed.
•logoff event SID session_id PGRP process_group PPID parent_pid PID pid program (login) Generated only when AudReport product is not installed
Auditing system extensions (HP-UX 11i v3 only)
On
•Enhanced audit data (for example, program name and source IP address)
•Enhanced filtering capabilities to filter
•Performance improvement by reducing the I/O activities of logging events that are not required to be logged
•Enhanced manageability of the audit log data
•Command line interface and a set of open APIs for extracting audit data
•Tools to generate
Audit Filtering
Audit Filtering features are available on
•The filter.conf configuration file that specifies the
•The audfilter configuration tool to interpret the filtering policy as specified in the configuration file, filter.conf, and to implement the policy. You can also use the audfilter tool to display or clear out the filtering policy currently being enforced in the kernel. For more information, see audfilter(1M).
•The audfilterd service daemon handles service requests from the audfilter tool, and reevaluates and reloads the filtering policy whenever the mounted file system table changes. For more information, see audfilterd(1M).
13