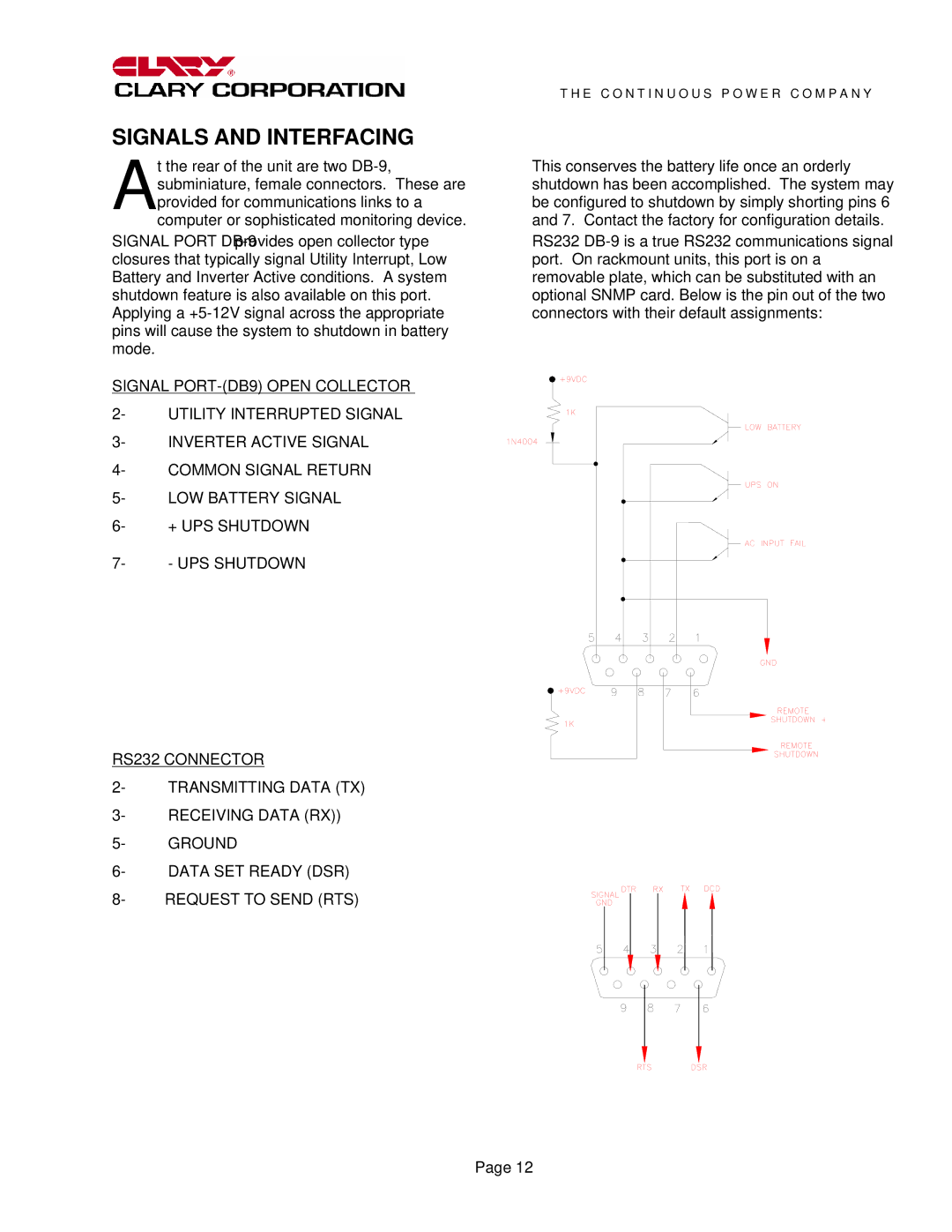
CMN4000R, CMN3000R specifications
The HSM CMN3000R and CMN4000R are advanced data security solutions designed for organizations that require high levels of data protection and compliance. Both models are part of HSM's larger portfolio of hardware security modules (HSMs) that ensure the confidentiality, integrity, and availability of sensitive information.One of the most notable features of the CMN3000R and CMN4000R is their robust encryption capabilities. These devices support a variety of encryption algorithms including AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and ECC (Elliptic Curve Cryptography). This flexibility allows organizations to choose the encryption standards that best meet their security needs, ensuring strong data protection against unauthorized access.
Both models are equipped with HSM's cutting-edge key management technology. This includes secure key generation, distribution, storage, and destruction, ensuring the lifecycle of cryptographic keys is managed securely. The modules are designed to comply with global security standards such as FIPS 140-2 Level 3, ensuring they meet stringent regulatory and industry requirements.
Another prominent feature of the HSM CMN3000R and CMN4000R is their high availability options, which support redundant setups and failover capabilities. This ensures that critical security operations can continue uninterrupted, even in the event of hardware failure. This is particularly important for organizations that rely on real-time data encryption and decryption for operational continuity.
The devices also boast impressive performance metrics. The CMN4000R, in particular, is designed to handle high throughput, with the ability to process thousands of cryptographic operations per second, making it ideal for large-scale applications where speed is essential.
In terms of connectivity, both models feature multiple interfaces including USB, Ethernet, and serial options, allowing them to integrate seamlessly with existing infrastructures. This adaptability enables organizations to deploy the HSMs in a variety of environments, whether on-premises or in cloud-based systems.
Additionally, the CMN3000R and CMN4000R provide strong physical security features such as tamper-evident sealing and hardware-based protection against physical attacks, safeguarding against unauthorized access to the device itself.
In conclusion, the HSM CMN3000R and CMN4000R represent cutting-edge solutions for organizations determined to bolster their data security posture. With their comprehensive encryption capabilities, advanced key management, high availability options, impressive performance, and robust physical security features, these HSMs stand out as essential tools in the fight against data breaches and cyber threats.