NETGEAR, Inc
Regulatory Compliance Information
Europe EU Declaration of Conformity
FCC Requirements for Operation in the United States
FCC Information to User
FCC Guidelines for Human Exposure
FCC Radio Frequency Interference Warnings & Instructions
FCC Declaration Of Conformity
Product and Publication Details
Contents
Chapter Restricting Access From Your Network
Chapter Using Network Monitoring Tools
Appendix a Technical Specifications
Conventions, Formats, and Scope
About This Manual
How to Print This Manual
How to Use This Manual
Revision History
Publication Revision History
Version Date Description V1.0 February Original publication
Xiv
Using the Setup Manual
Chapter Configuring Basic Connectivity
Logging In to Your Wireless Router
V1.0, February
V1.0, February
Viewing and Configuring Basic ISP Settings
ISP does not require login
V1.0, February
ISP does require login
V1.0, February
V1.0, February
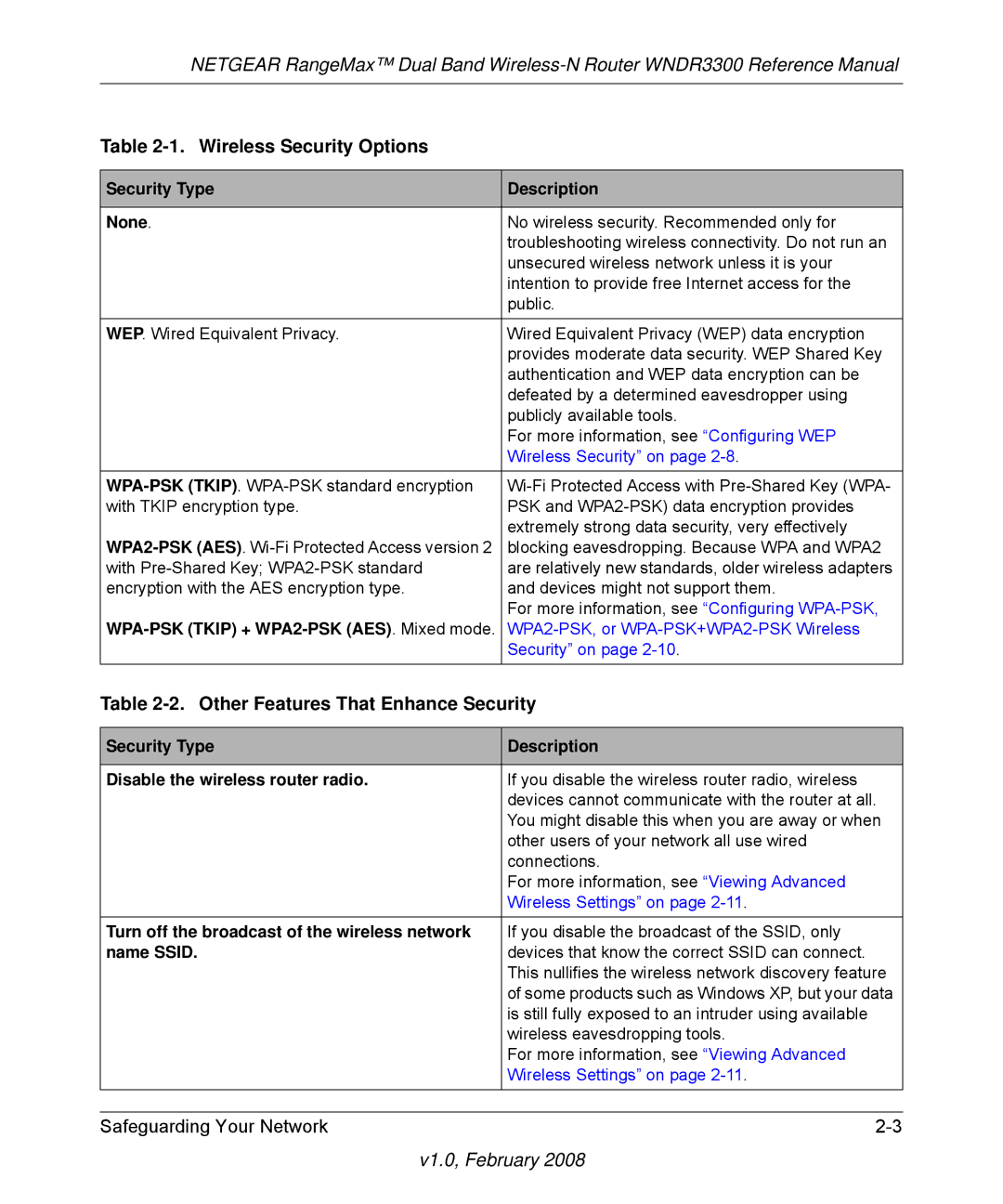
Choosing Appropriate Wireless Security
Chapter Safeguarding Your Network
Wireless data
Security options
Range up to 300 foot radius
Other Features That Enhance Security
Wireless Security Options
Recording Basic Wireless Settings Setup Information
Use WPS Wi-Fi Protected Setup
Modify your firewall’s rules
Changing Basic Wireless Settings
11G SSID. NETGEAR-2.4-G
Viewing Basic Wireless Settings
V1.0, February
Configuring WEP Wireless Security
V1.0, February
V1.0, February
Viewing Advanced Wireless Settings
Using WPS Security Wi-Fi Protected Setup
Push Button Configuration
PIN Entry
Configuring the WPS Settings
You can add WPS-enabled and non-WPS-enabled client devices
Adding Additional Non-WPS-Enabled Clients
Adding Additional WPS-Enabled Clients
Restricting Wireless Access by MAC Address
V1.0, February
Select the Turn Access Control On check box
Changing the Administrator Password
Backing Up Your Configuration
Understanding Your Firewall
V1.0, February
Restricting Access From Your Network
Content Filtering Overview
Blocking Access to Internet Sites
V1.0, February
Blocking Access to Internet Services
Configuring a User-Defined Service
Scheduling Blocking
Blocking Services by IP Address Range
Viewing Logs of Web Access or Attempted Web Access
Configuring E-mail Alert and Web Access Log Notifications
Log Entry Descriptions
Field Description
V1.0, February
Setting the Time
V1.0, February
Using the LAN Setup Options
Chapter Customizing Your Network Settings
Configuring LAN TCP/IP Setup Parameters
Configuring a Device Name
Using the Router as a Dhcp Server
Using Address Reservation
Using a Dynamic DNS Service
Select the Use a Dynamic DNS Service check box
Configuring the WAN Setup Options
Setting Up a Default DMZ Server
Disabling the SPI Firewall
Responding to a Ping on the Internet WAN Port
Setting the MTU Size
Configuring NAT Filtering
Configuring Static Routes
V1.0, February
V1.0, February
V1.0, February
Allowing Inbound Connections To Your Network
Chapter Fine-Tuning Your Network
V1.0, February
How Port Triggering Changes the Communication Process
V1.0, February
How Port Forwarding Changes the Communication Process
How Port Forwarding Differs from Port Triggering
Configuring Port Forwarding to Local Servers
Adding a Custom Service
Application Example Making a Local Web Server Public
Editing or Deleting a Port Forwarding Entry
To the instructions in Using Universal Plug and Play on
Configuring Port Triggering
Clear the Disable Port Triggering check box
Click Add Service
Using Universal Plug and Play
Identify critical wireless links
Optimizing Wireless Performance
Reduce interference
Configuring Quality of Service
Using WMM QoS for Wireless Multimedia Applications
QoS for Applications and Online Gaming
Configuring QoS for Internet Access
Click Add Priority Rule
QoS for a Router LAN Port
QoS for a MAC Address
Editing or Deleting an Existing QoS Policy
MSN
Changing the MTU
Optimizing Your Network Bandwidth
Common MTU Sizes
Application
RangeMax Dual Band Wireless-N Router WNDR3300
Overview of Home and Small Office Networking Technologies
Assessing Your Speed Requirements
Theoretical Transfer Time for 1 Gigabyte
Network Connection Theoretical Raw Transfer Time
Viewing Wireless Router Status Information
Chapter Using Network Monitoring Tools
1describes the router status fields
Wireless Router Status Fields
Dhcp
270Mbps at 5GHz & 54Mbps at 2.4GHz mode, there are two
270Mbps at 2.4GHz mode and Up to 130Mbps at 2.4GHz mode,
Connection Status Settings
Router Statistics
Viewing a List of Attached Devices
Managing the Configuration File
Backing Up and Restoring the Configuration
Upgrading the Router Software
Erasing the Configuration
V1.0, February
Upgrading Automatically to New Router Software
Upgrading Manually to New Router Software
Select the Turn Remote Management On check box
Enabling Remote Management Access
V1.0, February
Chapter Troubleshooting
Troubleshooting Quick Tips
Be sure to restart your network in this sequence
Troubleshooting Basic Functions
Make sure that the Ethernet cables are securely plugged
Check the Test light to verify correct router operation
Power light is not on or is blinking
Lights never turn off
Internet or Ethernet port lights are not on
Wireless light is not on
Troubleshooting the Web Configuration Interface
Troubleshooting the Internet Connection
Troubleshooting a Network Using the Ping Utility
Request timed out
Testing the LAN Path to Your Router
Testing the Path from Your Computer to a Remote Device
Problems with Date and Time
Using Your Wireless Card Setup Program
Solving Wireless Connection Problems
Setting Up and Testing Basic Wireless Connectivity
V1.0, January
V1.0, January
Restoring the Default Configuration and Password
V1.0, January
Appendix a Technical Specifications
Default Configuration Settings
Table A-1. WNDR3300 Router Default Configuration Settings
Network Protocol and Standards Compatibility
Feature Default Setting Wireless
11N Ssid NETGEAR-DualBand-N
Firewall
Electromagnetic Emissions
Feature Default Setting Power Adapter
Physical Specifications
Environmental Specifications
Feature Default Setting Interface Specifications
Restoring the Default User Name and Password
V1.0, February
V1.0, February
Document Link
Appendix B Related Documents
V1.0, February
Index
Index-2
Index-3
Index-4
Index-5
Index-6