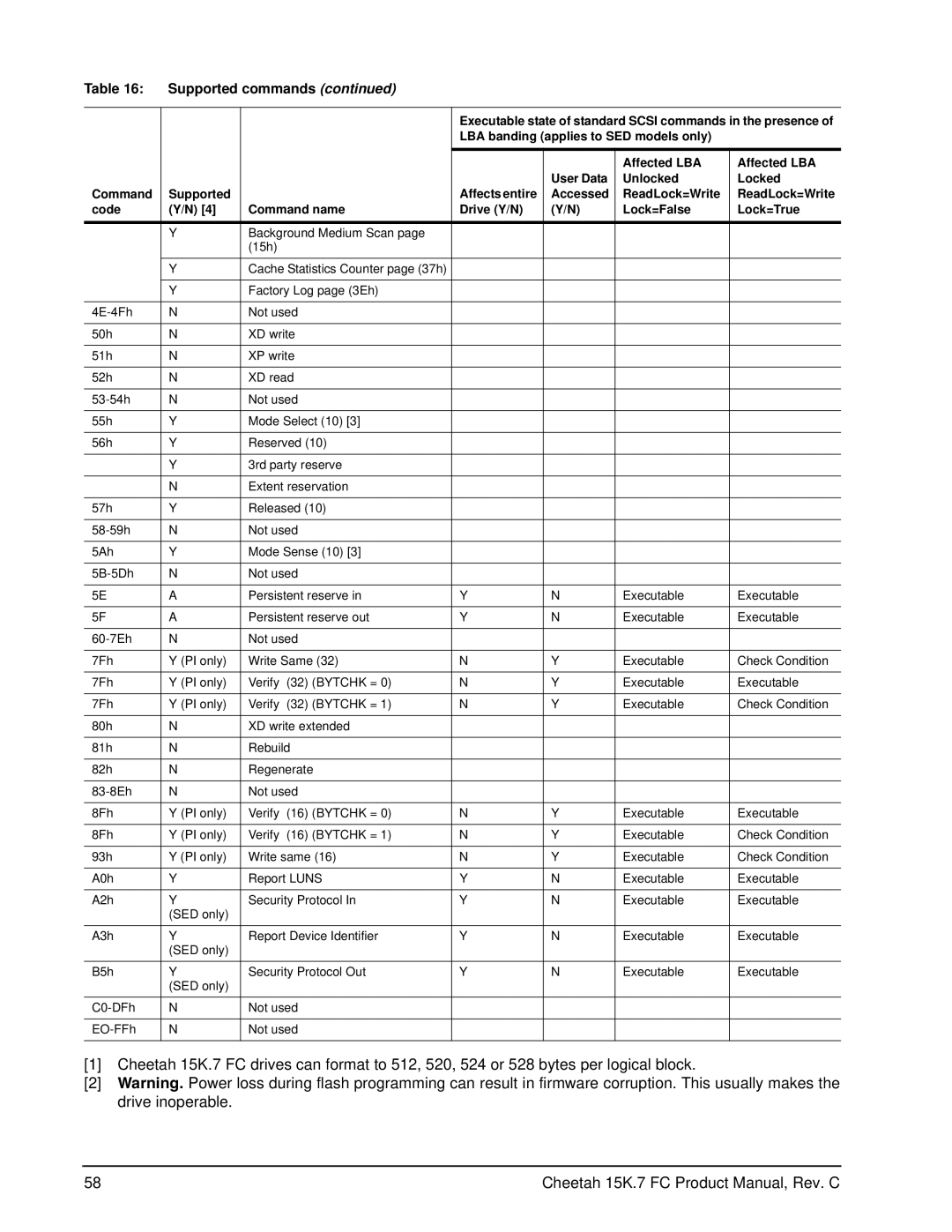
Table 16: | Supported commands (continued) |
|
|
|
| |
|
|
|
|
|
|
|
|
|
| Executable state of standard SCSI commands in the presence of | |||
|
|
| LBA banding (applies to SED models only) |
| ||
|
|
|
|
|
|
|
|
|
|
|
| Affected LBA | Affected LBA |
|
|
|
| User Data | Unlocked | Locked |
Command | Supported |
| Affects entire | Accessed | ReadLock=Write | ReadLock=Write |
code | (Y/N) [4] | Command name | Drive (Y/N) | (Y/N) | Lock=False | Lock=True |
| Y | Background Medium Scan page |
|
|
|
|
|
| (15h) |
|
|
|
|
|
|
|
|
|
|
|
| Y | Cache Statistics Counter page (37h) |
|
|
|
|
|
|
|
|
|
|
|
| Y | Factory Log page (3Eh) |
|
|
|
|
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
50h | N | XD write |
|
|
|
|
|
|
|
|
|
|
|
51h | N | XP write |
|
|
|
|
|
|
|
|
|
|
|
52h | N | XD read |
|
|
|
|
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
55h | Y | Mode Select (10) [3] |
|
|
|
|
|
|
|
|
|
|
|
56h | Y | Reserved (10) |
|
|
|
|
|
|
|
|
|
|
|
| Y | 3rd party reserve |
|
|
|
|
|
|
|
|
|
|
|
| N | Extent reservation |
|
|
|
|
|
|
|
|
|
|
|
57h | Y | Released (10) |
|
|
|
|
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
5Ah | Y | Mode Sense (10) [3] |
|
|
|
|
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
5E | A | Persistent reserve in | Y | N | Executable | Executable |
|
|
|
|
|
|
|
5F | A | Persistent reserve out | Y | N | Executable | Executable |
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
7Fh | Y (PI only) | Write Same (32) | N | Y | Executable | Check Condition |
|
|
|
|
|
|
|
7Fh | Y (PI only) | Verify (32) (BYTCHK = 0) | N | Y | Executable | Executable |
|
|
|
|
|
|
|
7Fh | Y (PI only) | Verify (32) (BYTCHK = 1) | N | Y | Executable | Check Condition |
|
|
|
|
|
|
|
80h | N | XD write extended |
|
|
|
|
|
|
|
|
|
|
|
81h | N | Rebuild |
|
|
|
|
|
|
|
|
|
|
|
82h | N | Regenerate |
|
|
|
|
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
8Fh | Y (PI only) | Verify (16) (BYTCHK = 0) | N | Y | Executable | Executable |
|
|
|
|
|
|
|
8Fh | Y (PI only) | Verify (16) (BYTCHK = 1) | N | Y | Executable | Check Condition |
|
|
|
|
|
|
|
93h | Y (PI only) | Write same (16) | N | Y | Executable | Check Condition |
|
|
|
|
|
|
|
A0h | Y | Report LUNS | Y | N | Executable | Executable |
|
|
|
|
|
|
|
A2h | Y | Security Protocol In | Y | N | Executable | Executable |
| (SED only) |
|
|
|
|
|
|
|
|
|
|
|
|
A3h | Y | Report Device Identifier | Y | N | Executable | Executable |
| (SED only) |
|
|
|
|
|
|
|
|
|
|
|
|
B5h | Y | Security Protocol Out | Y | N | Executable | Executable |
| (SED only) |
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
N | Not used |
|
|
|
| |
|
|
|
|
|
|
|
[1]Cheetah 15K.7 FC drives can format to 512, 520, 524 or 528 bytes per logical block.
[2]Warning. Power loss during flash programming can result in firmware corruption. This usually makes the drive inoperable.
58 | Cheetah 15K.7 FC Product Manual, Rev. C |