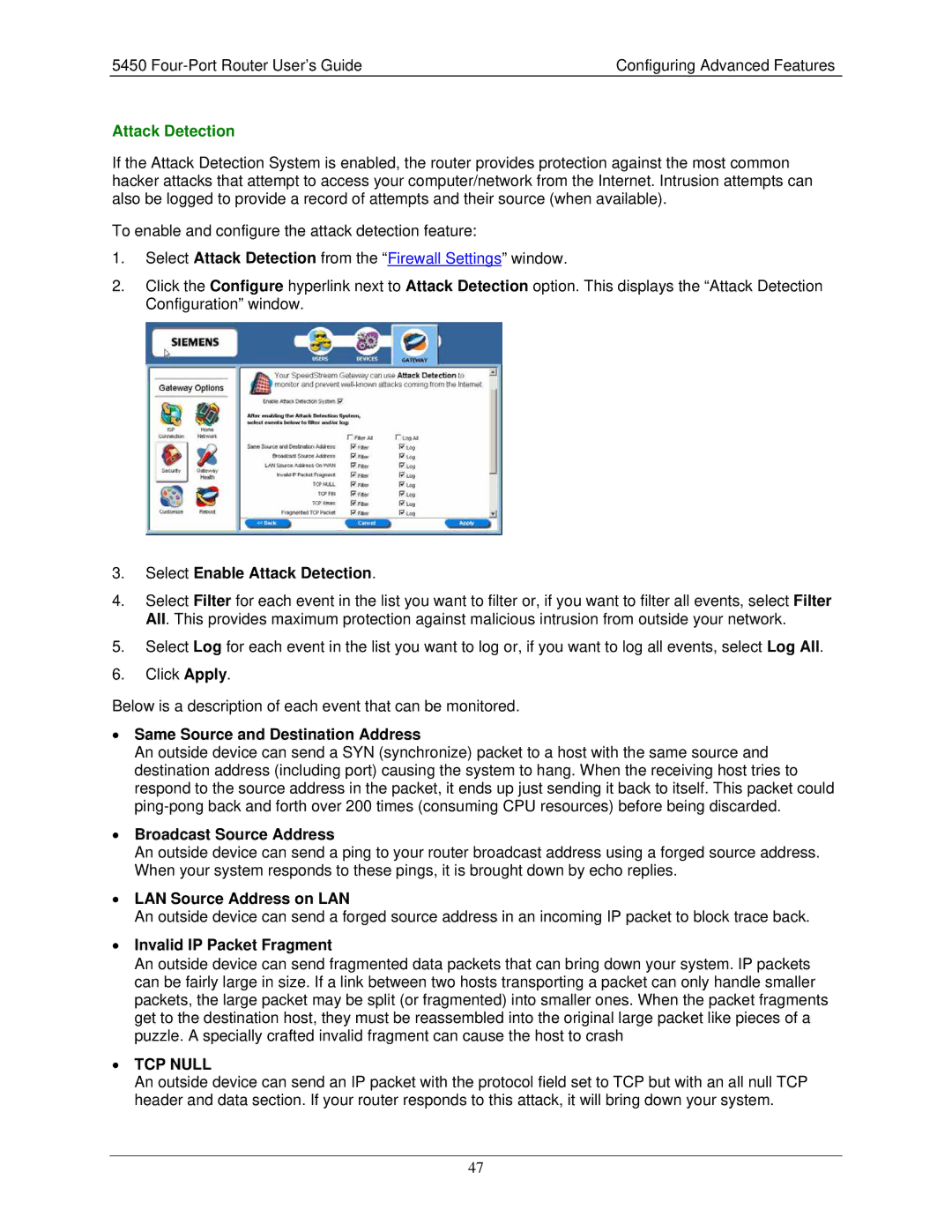
5450 specifications
The Siemens 5450 is a state-of-the-art industrial automation platform designed to enhance manufacturing processes and improve operational efficiency. This advanced system integrates robust hardware and innovative software solutions, making it a vital tool for businesses looking to stay competitive in a rapidly evolving landscape.One of the main features of the Siemens 5450 is its modular architecture, allowing for easy customization and scalability. This means organizations can tailor the system according to their specific needs, expanding capabilities as their operations grow. The system accommodates a variety of modules, including I/O, communication, and processing units, ensuring that it can support diverse applications across industries.
The Siemens 5450 is also equipped with the latest technologies in connectivity and communication. It supports industrial Ethernet, enabling seamless integration with existing network infrastructure, and facilitating real-time data exchange. This connectivity ensures that production processes are monitored and controlled efficiently, maximizing productivity while minimizing downtime.
Another significant characteristic of the Siemens 5450 is its sophisticated processing power. The platform is built on high-performance processors that provide rapid data processing capabilities. This performance is crucial for applications that require quick decision-making, such as quality control and machine management. Additionally, the system supports advanced algorithms for predictive maintenance, allowing businesses to anticipate equipment failures before they occur.
Security is a top priority for the Siemens 5450. The platform incorporates various security measures, including user authentication, data encryption, and secure communication protocols. These features protect sensitive information and maintain the integrity of the system, which is critical in today’s connected industrial environments.
Furthermore, the Siemens 5450 boasts an intuitive user interface that simplifies operation and monitoring. The graphical interface is designed for ease of use, allowing operators to navigate through processes and data effortlessly. This usability enhances training for new staff and reduces the potential for human error.
In conclusion, the Siemens 5450 is a comprehensive industrial automation platform that combines flexibility, advanced communication, and powerful processing capabilities. Its focus on security and user-centered design makes it an ideal choice for companies aiming to streamline operations and embrace the future of manufacturing technology.