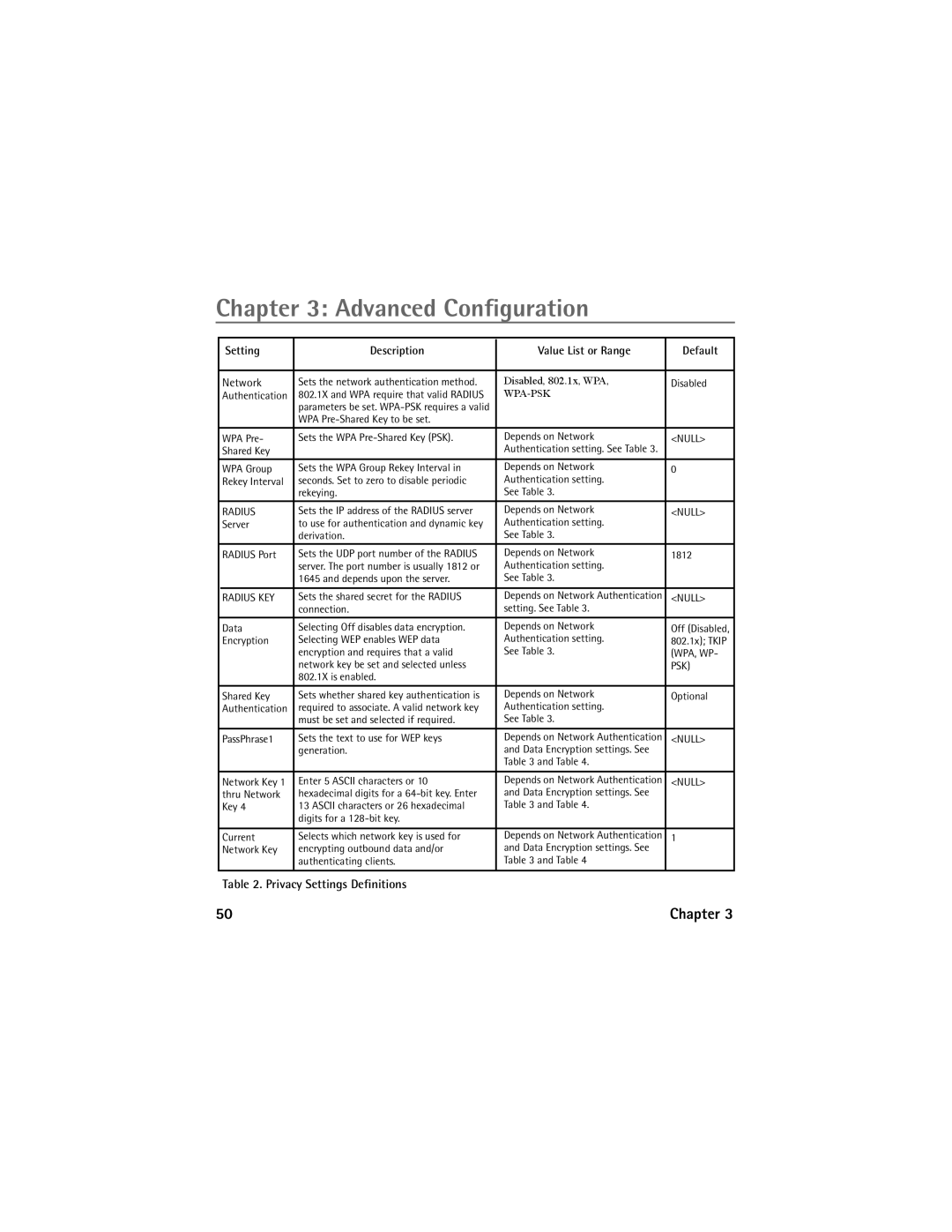
Network Router specifications
Technicolor, a name synonymous with innovative technology, has made significant strides in the realm of networking solutions, particularly with its Thomson Network Router series. These routers are engineered to meet the growing demands of high-speed internet access, catering to both residential and business environments.One of the main features of the Technicolor Thomson Network Router is its robust performance. Equipped with advanced processing capabilities, these routers are designed to facilitate seamless browsing, streaming, and gaming experiences across multiple devices simultaneously. With support for high-definition content and online gaming, users can enjoy a smooth internet experience without interruptions.
In terms of wireless technology, Technicolor routers often come with dual-band capabilities. This means they operate on both the 2.4 GHz and 5 GHz frequency bands, allowing users to optimize their connectivity based on their needs. The 2.4 GHz band offers a wider range, ideal for general browsing and connecting IoT devices, while the 5 GHz band supports higher speeds, perfect for bandwidth-intensive activities.
Security is another critical aspect of the Technicolor Thomson Network Router. The routers feature advanced security protocols such as WPA3, ensuring that users' data is encrypted and safe from unauthorized access. Furthermore, they may include built-in firewall protection and parental control features, allowing for a safer online environment for families.
Technicolor routers also support the latest networking technologies, including IPv6, which facilitates a greater number of devices to connect seamlessly and enhances overall network efficiency. The routers often come with Quality of Service (QoS) settings, allowing users to prioritize bandwidth for certain applications, ensuring a better experience for critical tasks like video conferencing or online gaming.
Additionally, the Technicolor Thomson Network Router series may incorporate easy setup and management features. Many models offer intuitive web interfaces or mobile applications, enabling users to monitor their network performance, manage connected devices, and configure settings with ease.
In summary, the Technicolor Thomson Network Router series stands out for its powerful performance, advanced security features, and user-friendly management options. With support for contemporary technologies and dual-band connectivity, these routers are well-equipped to handle the needs of modern households and businesses alike, making them a reliable choice for anyone looking to enhance their internet experience.