Build a security application
The Administrator can combine options on the application page to perform many useful security applications. There are two
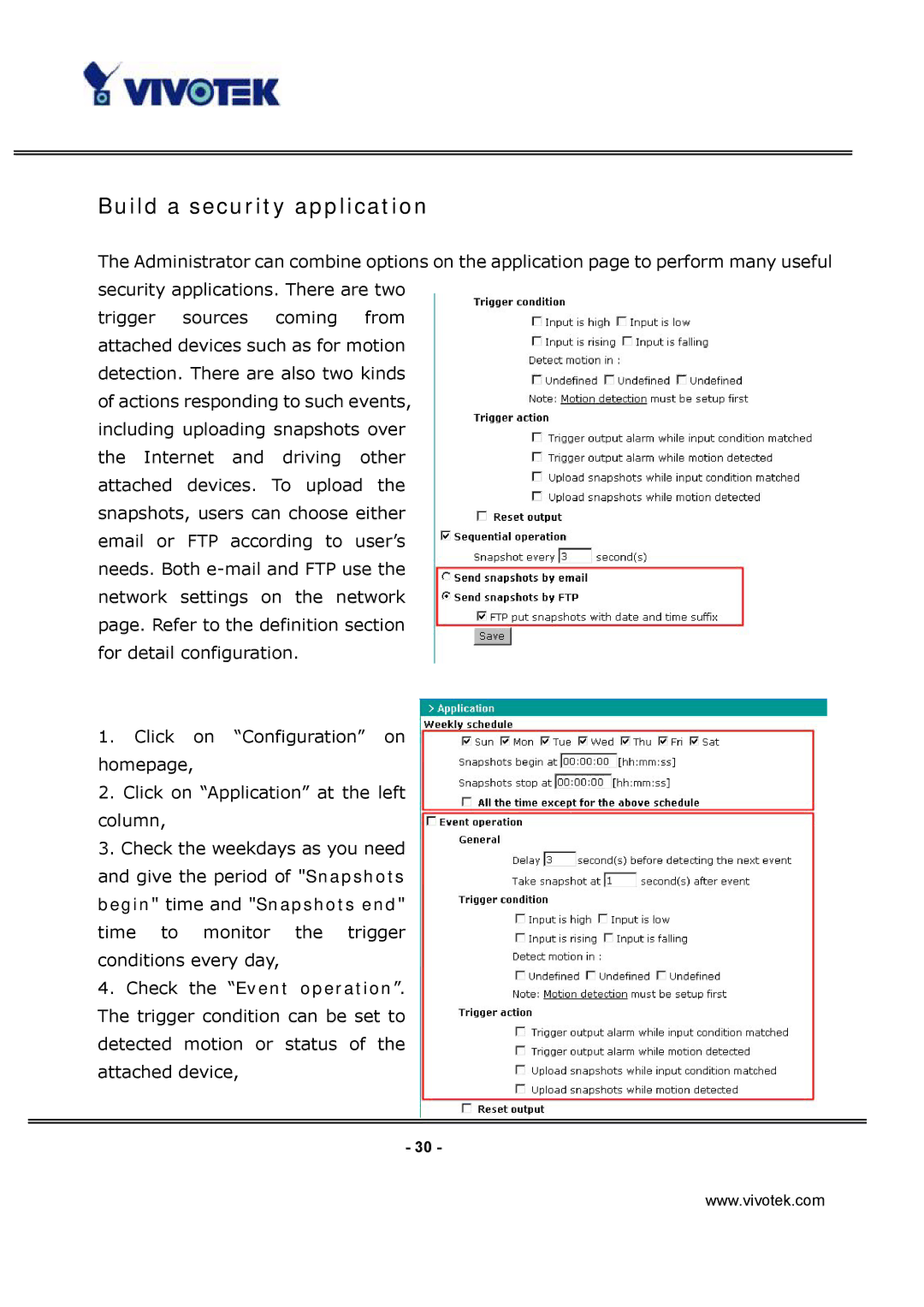
trigger sources coming from attached devices such as for motion detection. There are also two kinds of actions responding to such events, including uploading snapshots over the Internet and driving other attached devices. To upload the snapshots, users can choose either email or FTP according to user’s needs. Both
1.Click on “Configuration” on homepage,
2.Click on “Application” at the left column,
3.Check the weekdays as you need and give the period of "Snapshots begin" time and "Snapshots end" time to monitor the trigger conditions every day,
4.Check the “Event operation”. The trigger condition can be set to detected motion or status of the attached device,
-30 -
www.vivotek.com