SHDSL VPN Firewall Bridge/Router
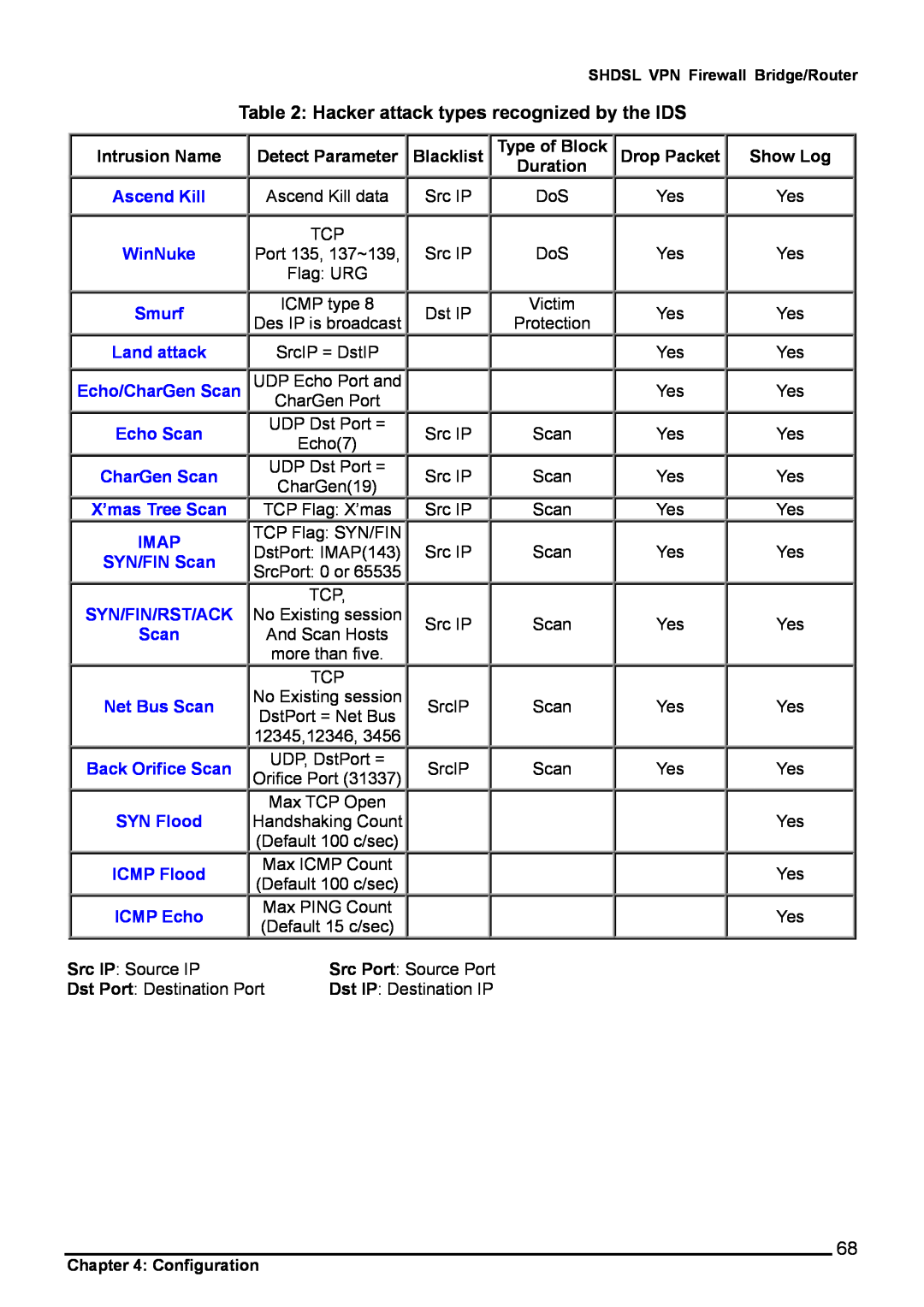
Table 2: Hacker attack types recognized by the IDS
Intrusion Name | Detect Parameter | |
|
| |
Ascend Kill | Ascend Kill data | |
|
| |
| TCP | |
WinNuke | Port 135, 137~139, | |
| Flag: URG | |
Smurf | ICMP type 8 | |
Des IP is broadcast | ||
| ||
Land attack | SrcIP = DstIP | |
Echo/CharGen Scan | UDP Echo Port and | |
| CharGen Port | |
Echo Scan | UDP Dst Port = | |
Echo(7) | ||
| ||
CharGen Scan | UDP Dst Port = | |
CharGen(19) | ||
|

 Blacklist
Blacklist 

Src IP
Src IP
Dst IP
Src IP
Src IP
Type of Block
Duration
DoS
DoS
Victim
Protection
Scan
Scan

 Drop Packet
Drop Packet 

Yes
Yes
Yes
Yes
Yes
Yes
Yes
Show Log
Yes
Yes
Yes
Yes
Yes
Yes
Yes
X’mas Tree Scan
IMAP
SYN/FIN Scan
SYN/FIN/RST/ACK
Scan
Net Bus Scan
Back Orifice Scan
SYN Flood
ICMP Flood
ICMP Echo
TCP Flag: X’mas
TCP Flag: SYN/FIN
DstPort: IMAP(143)
SrcPort: 0 or 65535
TCP,
No Existing session
And Scan Hosts more than five.
TCP
No Existing session DstPort = Net Bus 12345,12346, 3456
UDP, DstPort =
Orifice Port (31337)
Max TCP Open
Handshaking Count
(Default 100 c/sec)
Max ICMP Count (Default 100 c/sec)
Max PING Count (Default 15 c/sec)
Src IP
Src IP
Src IP
SrcIP
SrcIP
Scan
Scan
Scan
Scan
Scan
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Src IP: Source IP | Src Port: Source Port |
Dst Port: Destination Port | Dst IP: Destination IP |
68
Chapter 4: Configuration