CTSMX30055K9 specifications
Cisco Systems has long been recognized as a leader in networking and communication technologies, and the Cisco TelePresence MX300 (CTSMX30055K9) exemplifies the company’s commitment to fostering exceptional video collaboration solutions. The MX300 is particularly designed for medium-sized meeting rooms, making it an ideal choice for enterprises looking to enhance their videoconferencing capabilities.One of the standout features of the Cisco MX300 is its remarkable video experience. With support for up to 1080p high-definition video at 30 frames per second, users can enjoy crisp and clear visual quality during meetings. This resolution ensures that participants feel as though they are in the same room, regardless of their physical location. The MX300 also includes advanced video processing technology, which helps optimize picture quality even in varying bandwidth conditions.
In terms of audio, the MX300 is equipped with Cisco's intelligent audio technology. It utilizes multiple microphones and smart processing to ensure that all voices in the room are captured clearly, eliminating unwanted background noise. This results in a natural conversational experience, allowing for seamless interactions among participants.
Another significant characteristic of the MX300 is its user-friendly interface. The device comes with a simple remote control and touchscreen capabilities that make it easy for users to initiate calls, share content, and manage meetings. Integration with Cisco's Webex platform further enhances its usability, allowing users to join meetings with just one click.
The MX300 is known for its flexibility and scalability. It can be easily integrated into an existing IT infrastructure, supporting various endpoints and devices, which contributes to a more cohesive video collaboration experience. Additionally, it features interoperability with other video conferencing systems, ensuring that organizations can connect with partners and clients regardless of their technology stack.
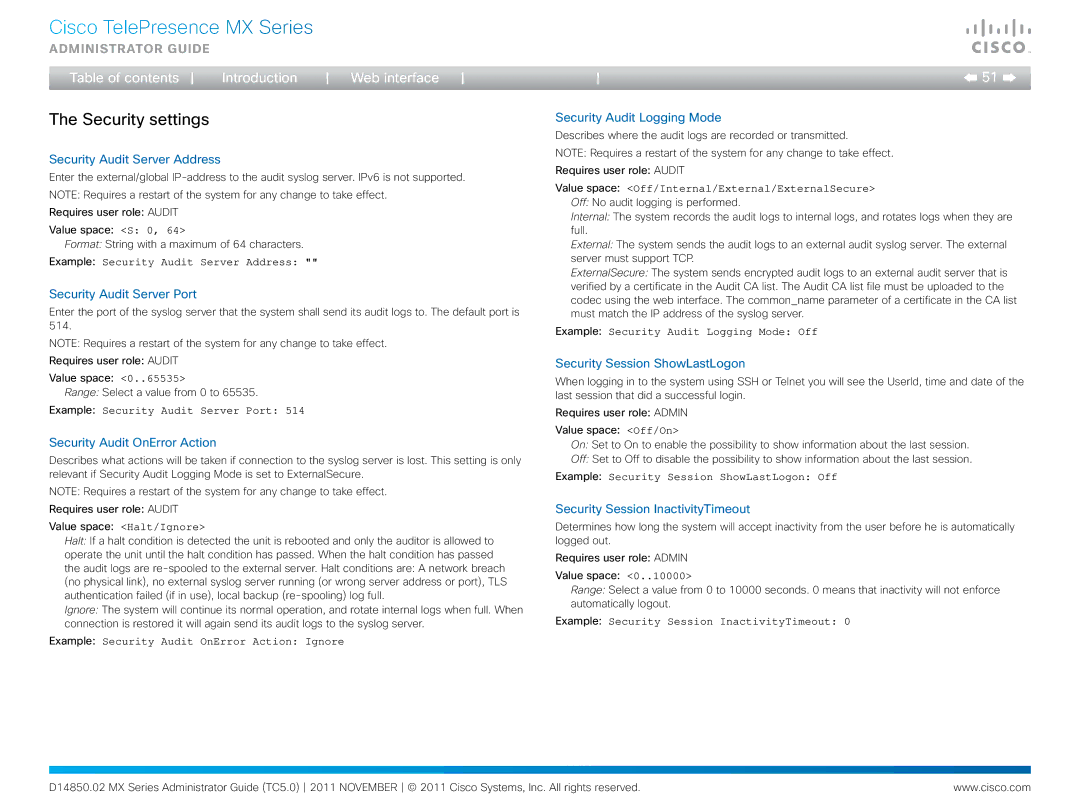
Security is another strong suit of the Cisco MX300. The device incorporates robust security protocols, including encryption and secure access controls, safeguarding sensitive information shared during meetings. This emphasis on security is critical for organizations seeking to maintain compliance and protect their data.
Overall, the Cisco TelePresence MX300 (CTSMX30055K9) is a powerful solution for medium-sized meeting rooms, offering high-definition video, intelligent audio processing, and a user-friendly interface. With its flexibility, scalability, and strong security features, the MX300 stands out as an ideal choice for organizations committed to effective communication and collaboration. By enhancing the quality of virtual meetings, Cisco's MX300 continues to play a vital role in transforming the workplace into an environment where ideas can be shared effortlessly, fostering innovation and productivity.