Chapter 1 About Cisco IP Solution Center
About MPLS VPNs
•Audit Existing Services: Checks and evaluates configuration of deployed service to see if the service is still in effect.
•Audit Routing Reports: Checks the VRF for the VPN on the PE. This report also checks if VPN connectivity is operational by evaluating reachability of the network devices in the VPN.
About MPLS VPNs
At its simplest, a virtual private network (VPN) is a collection of sites that share the same routing table. A VPN is also a network in which customer connectivity to multiple sites is deployed on a shared infrastructure with the same administrative policies as a private network.The path between two systems in a VPN, and the characteristics of that path, may also be determined (wholly or partially) by policy. Whether a system in a particular VPN is allowed to communicate with systems not in the same VPN is also a matter of policy.
In MPLS VPN, a VPN generally consists of a set of sites that are interconnected by means of an MPLS provider core network, but it is also possible to apply different policies to different systems that are located at the same site. Policies can also be applied to systems that dial in; the chosen policies would be based on the
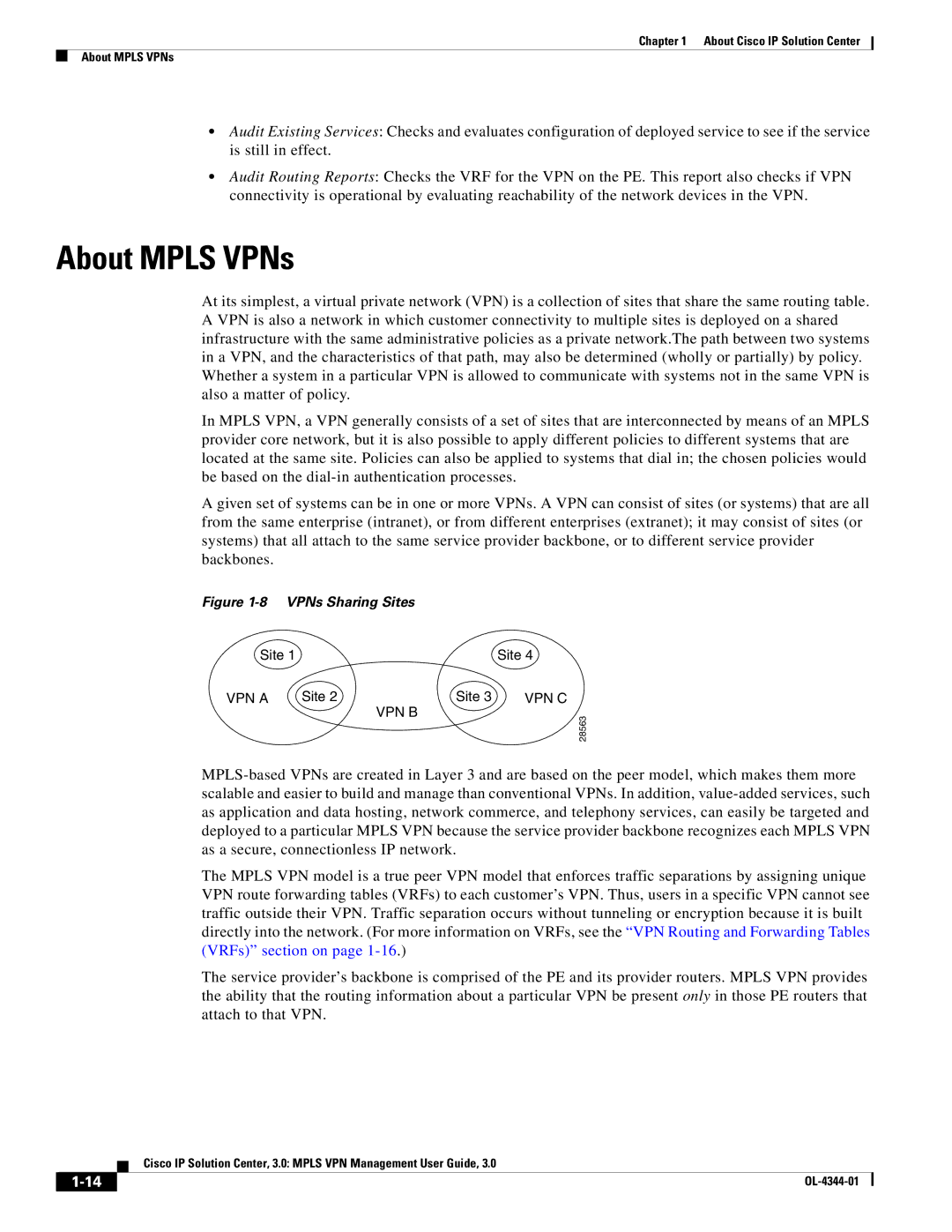
A given set of systems can be in one or more VPNs. A VPN can consist of sites (or systems) that are all from the same enterprise (intranet), or from different enterprises (extranet); it may consist of sites (or systems) that all attach to the same service provider backbone, or to different service provider backbones.
Figure 1-8 VPNs Sharing Sites
Site 1 |
|
| Site 4 |
VPN A | Site 2 | Site 3 | VPN C |
|
| VPN B | 28563 |
|
|
|
The MPLS VPN model is a true peer VPN model that enforces traffic separations by assigning unique VPN route forwarding tables (VRFs) to each customer’s VPN. Thus, users in a specific VPN cannot see traffic outside their VPN. Traffic separation occurs without tunneling or encryption because it is built directly into the network. (For more information on VRFs, see the “VPN Routing and Forwarding Tables (VRFs)” section on page
The service provider’s backbone is comprised of the PE and its provider routers. MPLS VPN provides the ability that the routing information about a particular VPN be present only in those PE routers that attach to that VPN.
Cisco IP Solution Center, 3.0: MPLS VPN Management User Guide, 3.0
| ||
|