Section 3 - Configuration
Firewall Settings
A firewall protects your network from the outside world. The
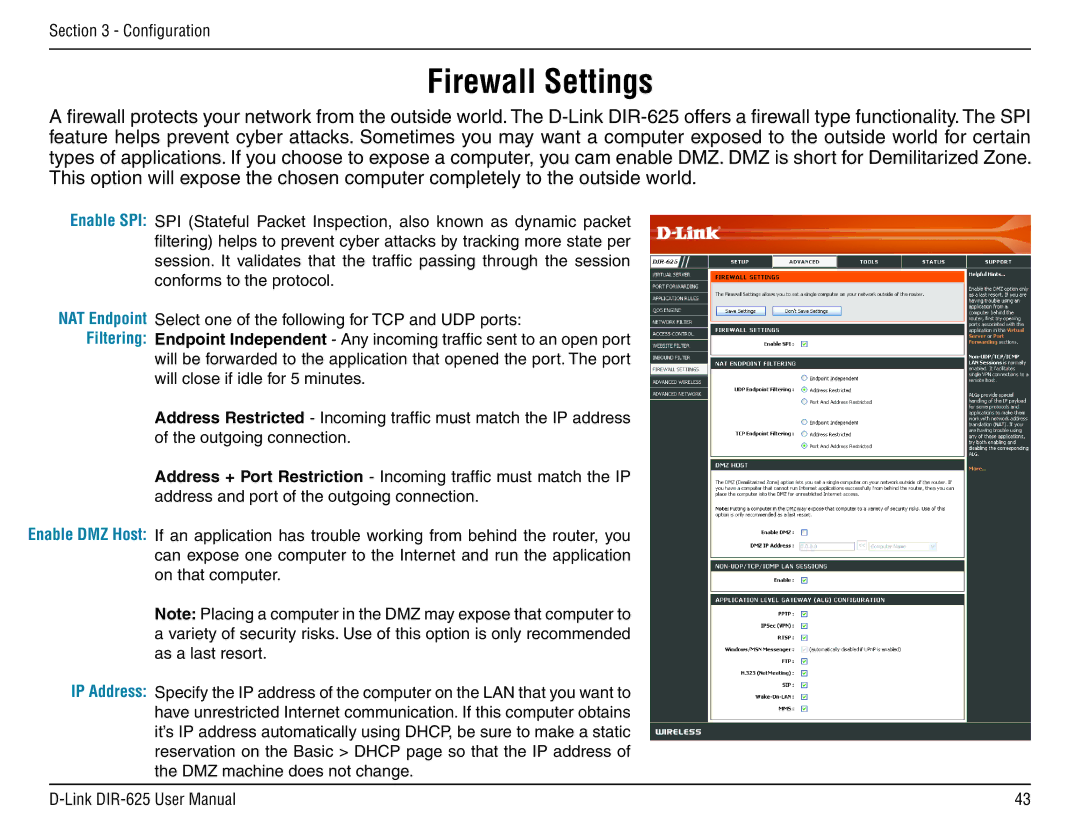
| Enable SPI: SPI (Stateful Packet Inspection, also known as dynamic packet |
| |
|
| filtering) helps to prevent cyber attacks by tracking more state per |
|
|
| session. It validates that the traffic passing through the session |
|
|
| conforms to the protocol. |
|
| NAT Endpoint | Select one of the following for TCP and UDP ports: |
|
| Filtering: Endpoint Independent - Any incoming traffic sent to an open port |
| |
|
| will be forwarded to the application that opened the port. The port |
|
|
| will close if idle for 5 minutes. |
|
|
| Address Restricted - Incoming traffic must match the IP address |
|
|
| of the outgoing connection. |
|
|
| Address + Port Restriction - Incoming traffic must match the IP |
|
|
| address and port of the outgoing connection. |
|
Enable DMZ Host: If an application has trouble working from behind the router, you |
| ||
|
| can expose one computer to the Internet and run the application |
|
|
| on that computer. |
|
|
| Note: Placing a computer in the DMZ may expose that computer to |
|
|
| a variety of security risks. Use of this option is only recommended |
|
|
| as a last resort. |
|
| IP Address: Specify the IP address of the computer on the LAN that you want to |
| |
|
| have unrestricted Internet communication. If this computer obtains |
|
|
| it’s IP address automatically using DHCP, be sure to make a static |
|
|
| reservation on the Basic > DHCP page so that the IP address of |
|
|
| the DMZ machine does not change. |
|
|
|
| |
| 43 | ||