RFIPSC Quick Start Guide
either saved it in a file or copied the contents of it to the Windows clipboard. In a file, the certificate may be in binary (X.509), PEM (Privacy Enhanced Mail) or HEX format. Pasted from the clipboard, the certificate must be in PEM encoded format.
Advanced button (D)
Opens a dialog box for configuring the socks and proxy settings.
Reference Number (E) (Key Identifier)
The key identifier is used only in connection with the Certificate Management Protocol (CMP). The key identifier is used along with the key to identify the user requesting a certificate.
Key (F)
This selection is used only in connection with the CMP protocol. The Key selected is a shared secret granted by the certification authority to be used in the certification request. This Key is used for verification of the user requesting a certificate.
Off-line Certification Request
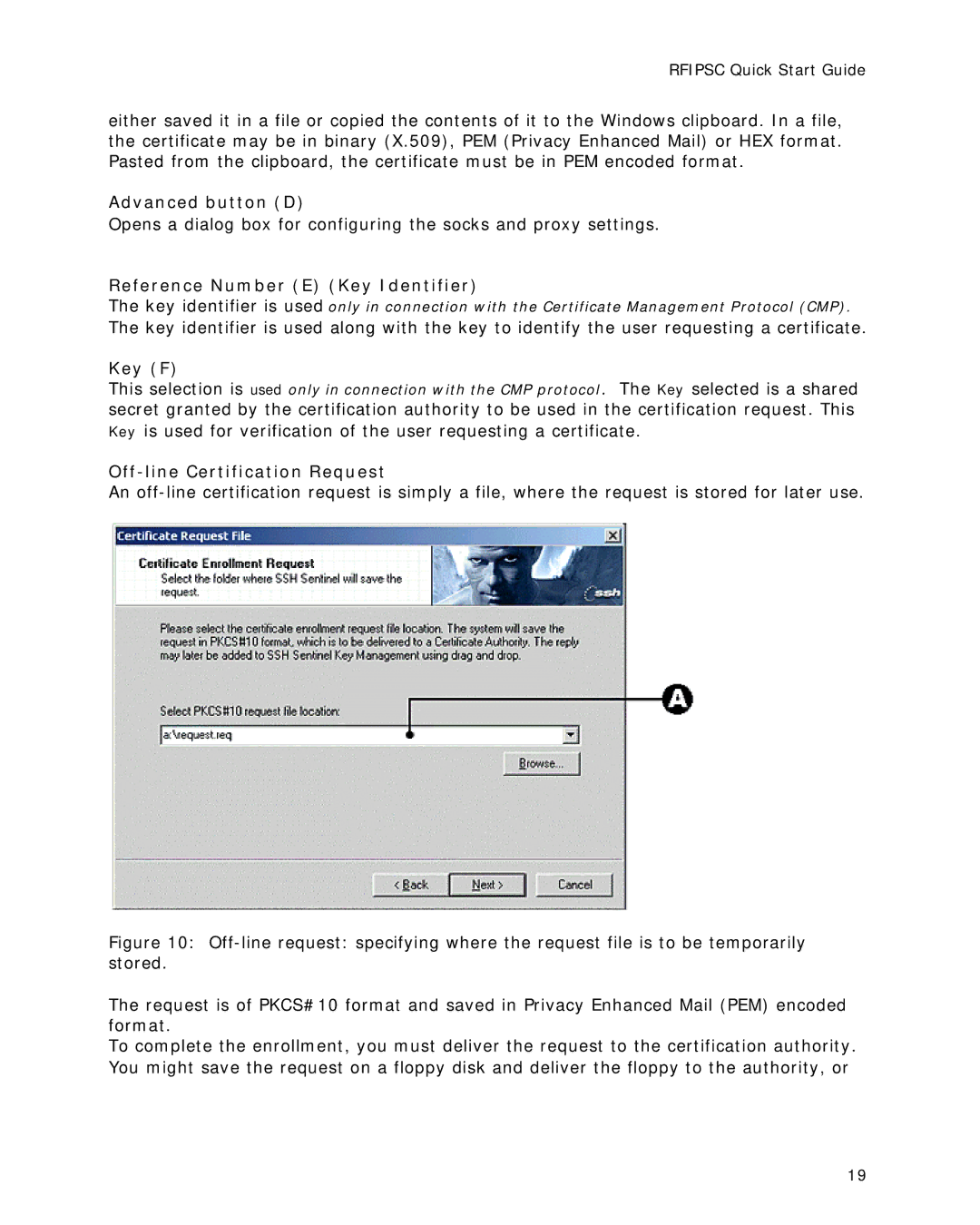
An
Figure 10: Off-line request: specifying where the request file is to be temporarily stored.
The request is of PKCS#10 format and saved in Privacy Enhanced Mail (PEM) encoded format.
To complete the enrollment, you must deliver the request to the certification authority. You might save the request on a floppy disk and deliver the floppy to the authority, or
19