Important Note: If encryption of any kind, at any level is applied to the Router, all devices on the network must comply with all security measures.
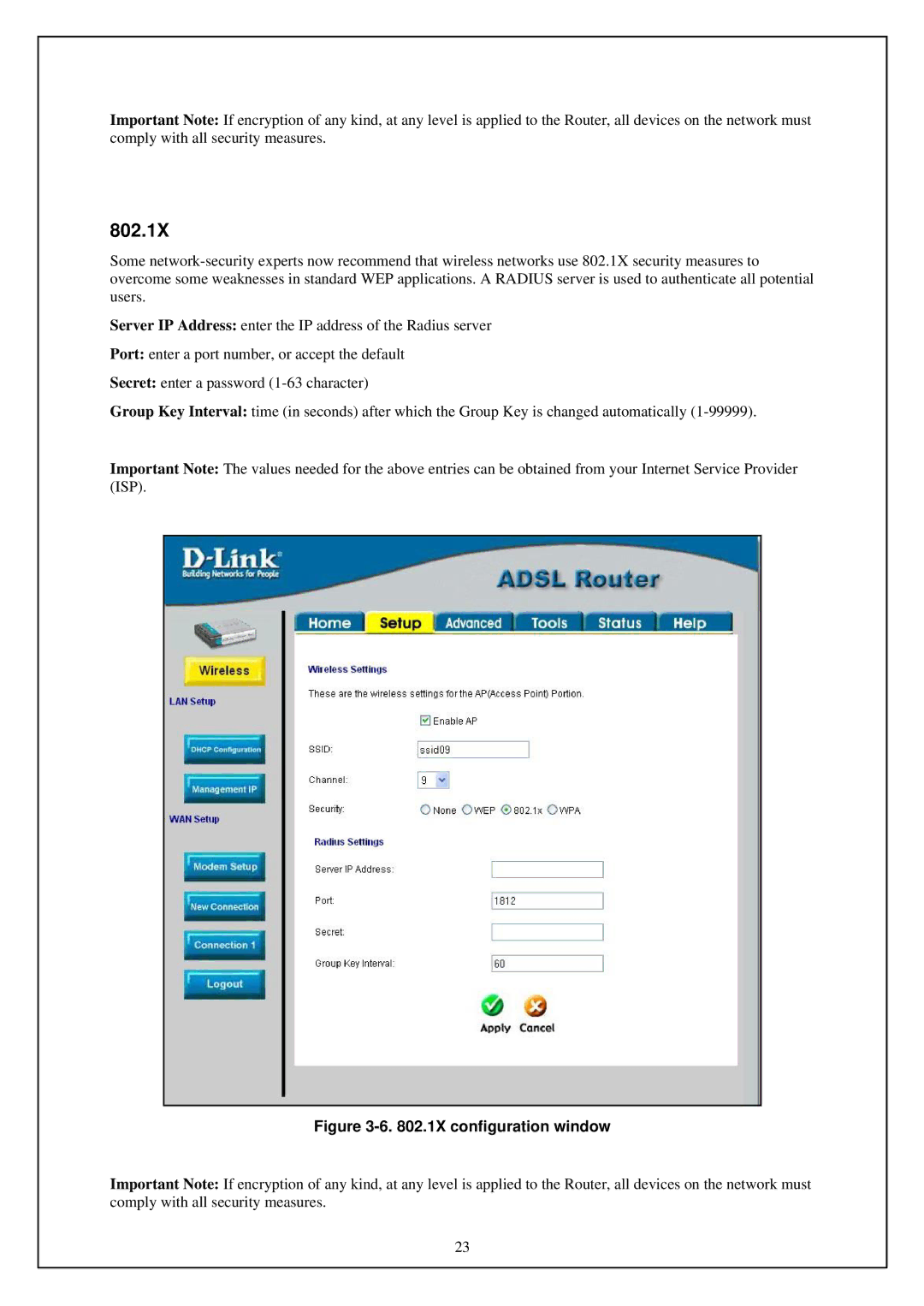
802.1X
Some
Server IP Address: enter the IP address of the Radius server
Port: enter a port number, or accept the default
Secret: enter a password
Group Key Interval: time (in seconds) after which the Group Key is changed automatically
Important Note: The values needed for the above entries can be obtained from your Internet Service Provider (ISP).
Figure 3-6. 802.1X configuration window
Important Note: If encryption of any kind, at any level is applied to the Router, all devices on the network must comply with all security measures.
23