•
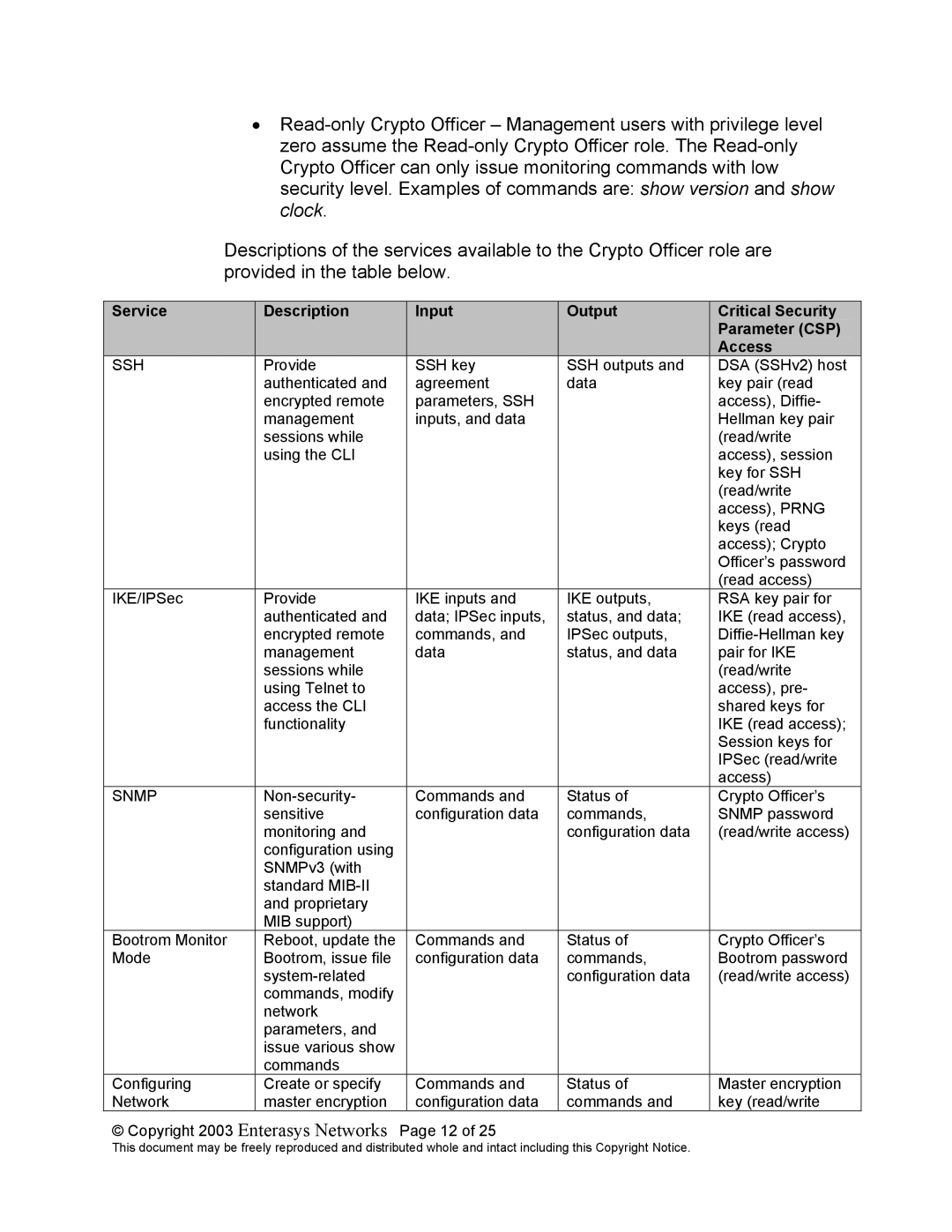
Descriptions of the services available to the Crypto Officer role are provided in the table below.
Service | Description | Input | Output | Critical Security |
|
|
|
| Parameter (CSP) |
|
|
|
| Access |
SSH | Provide | SSH key | SSH outputs and | DSA (SSHv2) host |
| authenticated and | agreement | data | key pair (read |
| encrypted remote | parameters, SSH |
| access), Diffie- |
| management | inputs, and data |
| Hellman key pair |
| sessions while |
|
| (read/write |
| using the CLI |
|
| access), session |
|
|
|
| key for SSH |
|
|
|
| (read/write |
|
|
|
| access), PRNG |
|
|
|
| keys (read |
|
|
|
| access); Crypto |
|
|
|
| Officer’s password |
|
|
|
| (read access) |
IKE/IPSec | Provide | IKE inputs and | IKE outputs, | RSA key pair for |
| authenticated and | data; IPSec inputs, | status, and data; | IKE (read access), |
| encrypted remote | commands, and | IPSec outputs, | |
| management | data | status, and data | pair for IKE |
| sessions while |
|
| (read/write |
| using Telnet to |
|
| access), pre- |
| access the CLI |
|
| shared keys for |
| functionality |
|
| IKE (read access); |
|
|
|
| Session keys for |
|
|
|
| IPSec (read/write |
|
|
|
| access) |
SNMP | Commands and | Status of | Crypto Officer’s | |
| sensitive | configuration data | commands, | SNMP password |
| monitoring and |
| configuration data | (read/write access) |
| configuration using |
|
|
|
| SNMPv3 (with |
|
|
|
| standard |
|
|
|
| and proprietary |
|
|
|
| MIB support) |
|
|
|
Bootrom Monitor | Reboot, update the | Commands and | Status of | Crypto Officer’s |
Mode | Bootrom, issue file | configuration data | commands, | Bootrom password |
|
| configuration data | (read/write access) | |
| commands, modify |
|
|
|
| network |
|
|
|
| parameters, and |
|
|
|
| issue various show |
|
|
|
| commands |
|
|
|
Configuring | Create or specify | Commands and | Status of | Master encryption |
Network | master encryption | configuration data | commands and | key (read/write |
© Copyright 2003 Enterasys Networks Page 12 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.