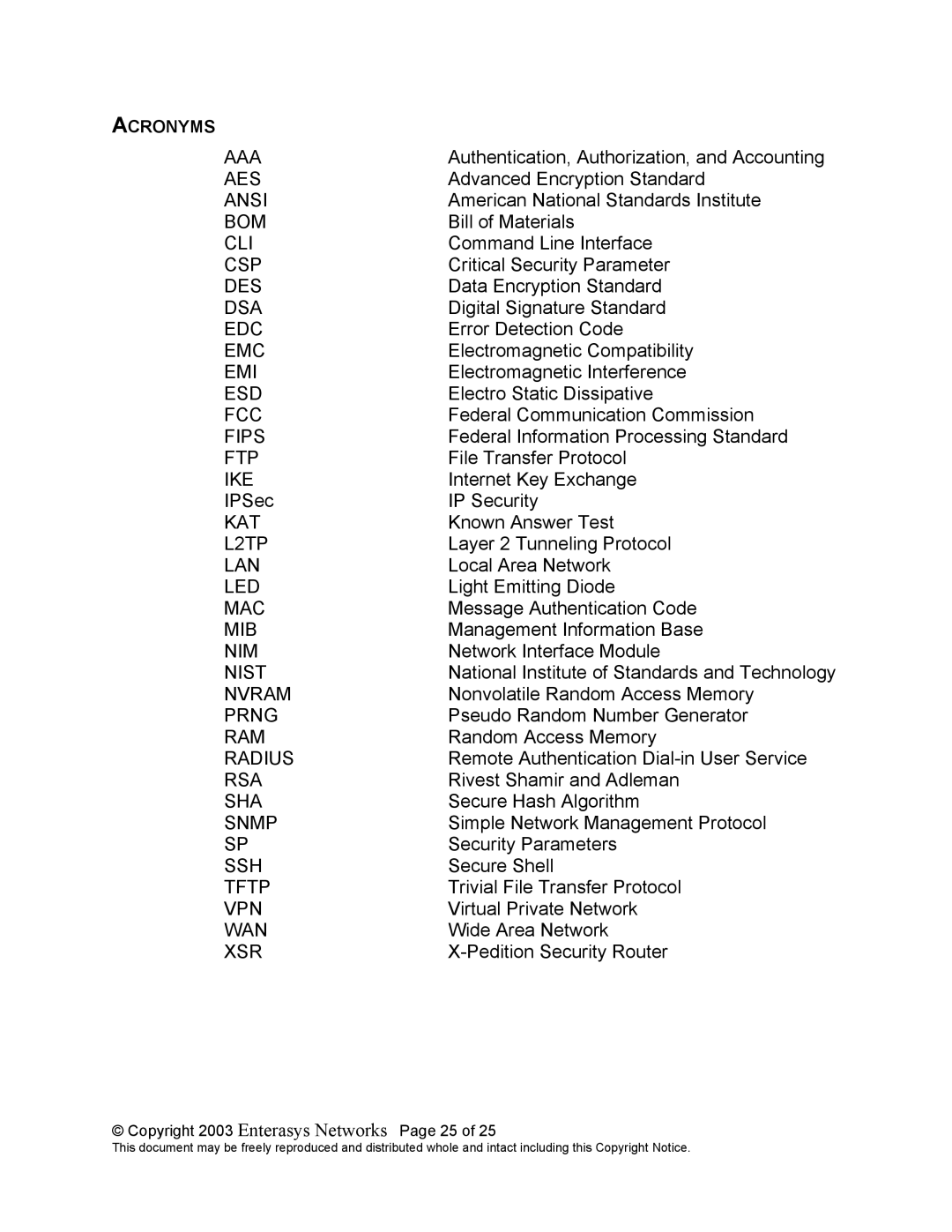
ACRONYMS
AAA | Authentication, Authorization, and Accounting |
AES | Advanced Encryption Standard |
ANSI | American National Standards Institute |
BOM | Bill of Materials |
CLI | Command Line Interface |
CSP | Critical Security Parameter |
DES | Data Encryption Standard |
DSA | Digital Signature Standard |
EDC | Error Detection Code |
EMC | Electromagnetic Compatibility |
EMI | Electromagnetic Interference |
ESD | Electro Static Dissipative |
FCC | Federal Communication Commission |
FIPS | Federal Information Processing Standard |
FTP | File Transfer Protocol |
IKE | Internet Key Exchange |
IPSec | IP Security |
KAT | Known Answer Test |
L2TP | Layer 2 Tunneling Protocol |
LAN | Local Area Network |
LED | Light Emitting Diode |
MAC | Message Authentication Code |
MIB | Management Information Base |
NIM | Network Interface Module |
NIST | National Institute of Standards and Technology |
NVRAM | Nonvolatile Random Access Memory |
PRNG | Pseudo Random Number Generator |
RAM | Random Access Memory |
RADIUS | Remote Authentication |
RSA | Rivest Shamir and Adleman |
SHA | Secure Hash Algorithm |
SNMP | Simple Network Management Protocol |
SP | Security Parameters |
SSH | Secure Shell |
TFTP | Trivial File Transfer Protocol |
VPN | Virtual Private Network |
WAN | Wide Area Network |
XSR |
|
© Copyright 2003 Enterasys Networks Page 25 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.