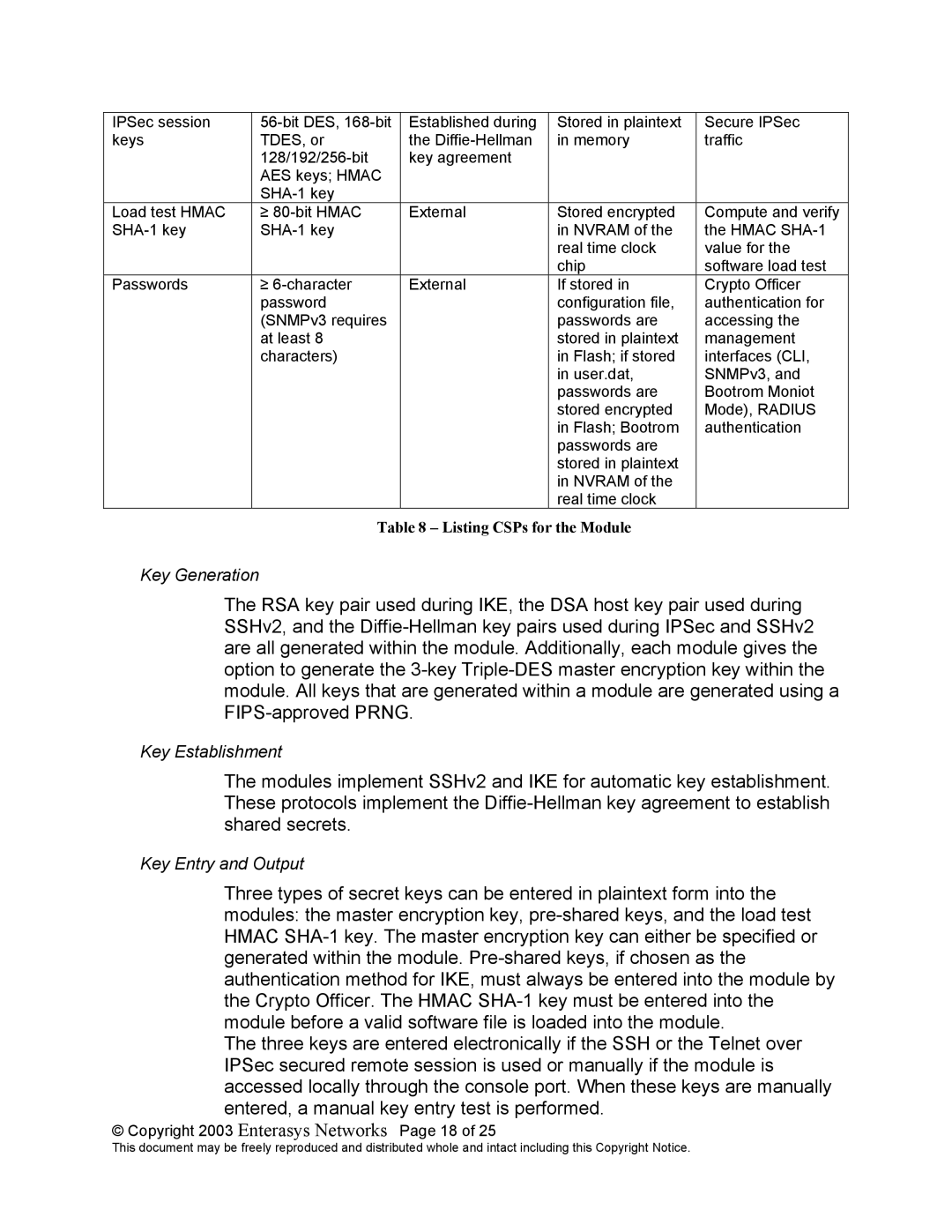
IPSec session | Established during | Stored in plaintext | Secure IPSec | |
keys | TDES, or | the | in memory | traffic |
| key agreement |
|
| |
| AES keys; HMAC |
|
|
|
|
|
|
| |
Load test HMAC | ≥ | External | Stored encrypted | Compute and verify |
| in NVRAM of the | the HMAC | ||
|
|
| real time clock | value for the |
|
|
| chip | software load test |
Passwords | ≥ | External | If stored in | Crypto Officer |
| password |
| configuration file, | authentication for |
| (SNMPv3 requires |
| passwords are | accessing the |
| at least 8 |
| stored in plaintext | management |
| characters) |
| in Flash; if stored | interfaces (CLI, |
|
|
| in user.dat, | SNMPv3, and |
|
|
| passwords are | Bootrom Moniot |
|
|
| stored encrypted | Mode), RADIUS |
|
|
| in Flash; Bootrom | authentication |
|
|
| passwords are |
|
|
|
| stored in plaintext |
|
|
|
| in NVRAM of the |
|
|
|
| real time clock |
|
| Table 8 – Listing CSPs for the Module |
| ||
Key Generation
The RSA key pair used during IKE, the DSA host key pair used during SSHv2, and the
Key Establishment
The modules implement SSHv2 and IKE for automatic key establishment. These protocols implement the
Key Entry and Output
Three types of secret keys can be entered in plaintext form into the modules: the master encryption key,
The three keys are entered electronically if the SSH or the Telnet over IPSec secured remote session is used or manually if the module is accessed locally through the console port. When these keys are manually entered, a manual key entry test is performed.
© Copyright 2003 Enterasys Networks Page 18 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.