|
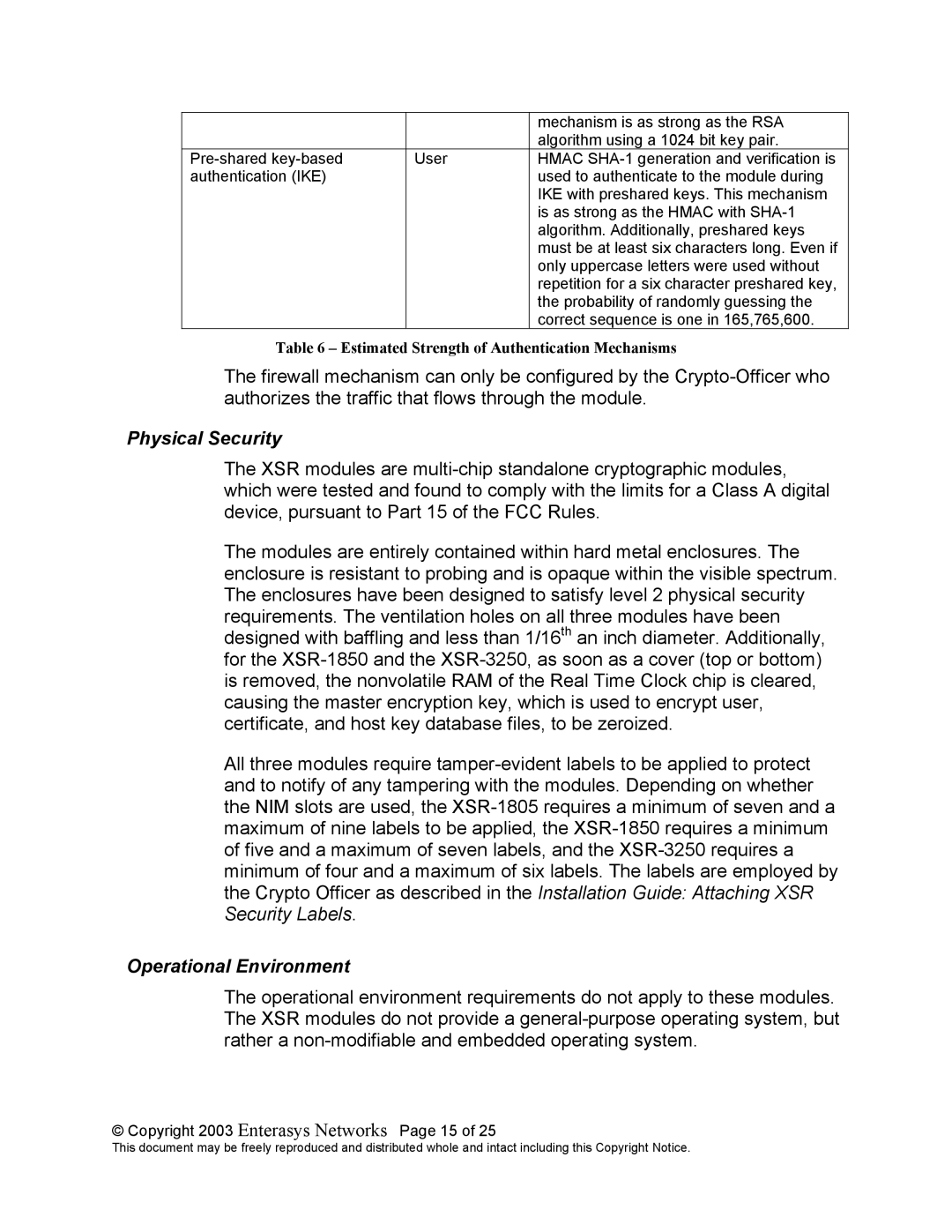
| mechanism is as strong as the RSA |
|
| algorithm using a 1024 bit key pair. |
User | HMAC | |
authentication (IKE) |
| used to authenticate to the module during |
|
| IKE with preshared keys. This mechanism |
|
| is as strong as the HMAC with |
|
| algorithm. Additionally, preshared keys |
|
| must be at least six characters long. Even if |
|
| only uppercase letters were used without |
|
| repetition for a six character preshared key, |
|
| the probability of randomly guessing the |
|
| correct sequence is one in 165,765,600. |
Table 6 – Estimated Strength of Authentication Mechanisms
The firewall mechanism can only be configured by the
Physical Security
The XSR modules are
The modules are entirely contained within hard metal enclosures. The enclosure is resistant to probing and is opaque within the visible spectrum. The enclosures have been designed to satisfy level 2 physical security requirements. The ventilation holes on all three modules have been designed with baffling and less than 1/16th an inch diameter. Additionally, for the
All three modules require
Operational Environment
The operational environment requirements do not apply to these modules. The XSR modules do not provide a
© Copyright 2003 Enterasys Networks Page 15 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.