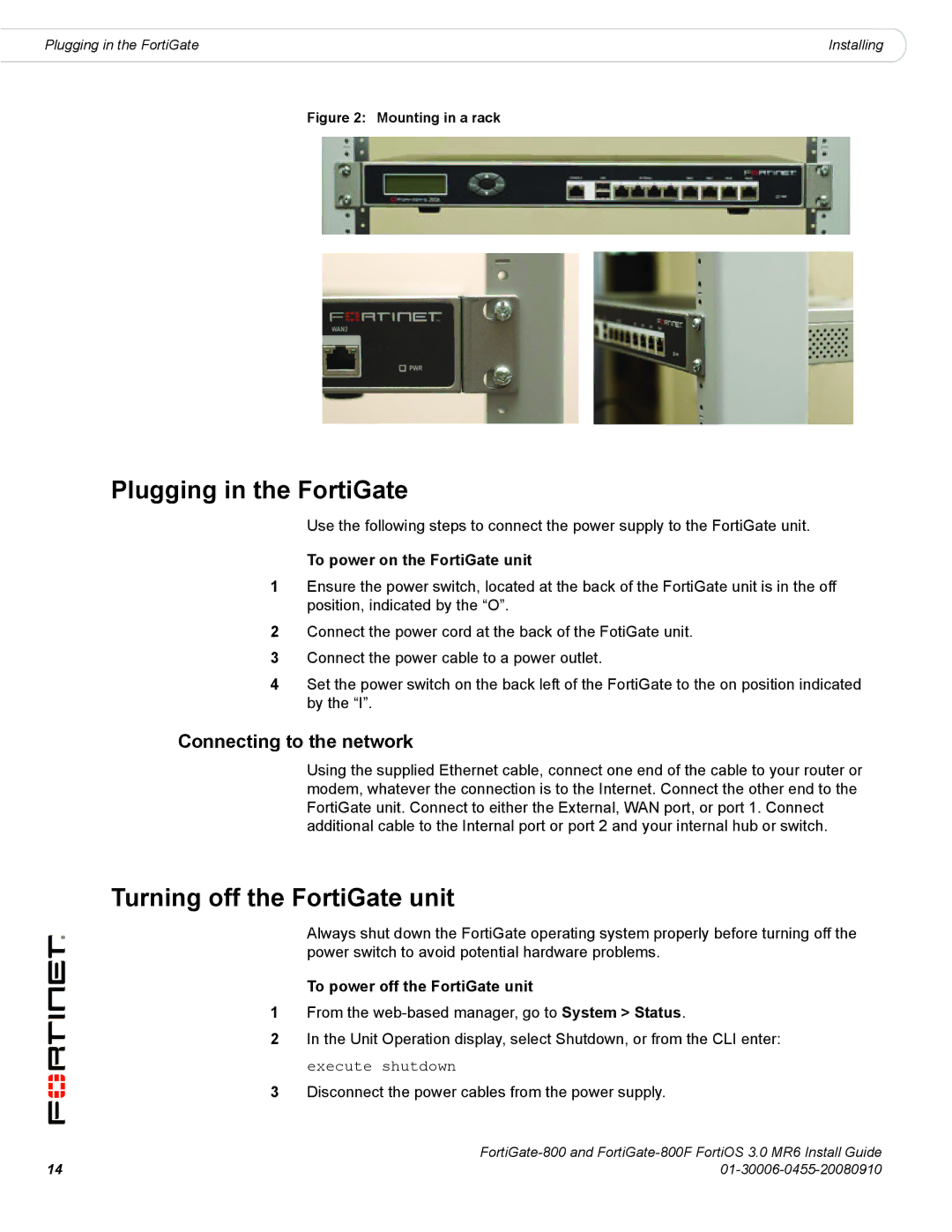
800/800F specifications
Fortinet has established itself as a leader in cybersecurity solutions, and the FortiGate 800/800F series is a testament to this reputation. These next-generation firewalls are designed to deliver high-performance security for enterprise-level networks, providing a robust defense against a multitude of cyber threats.One of the standout features of the FortiGate 800/800F is its advanced security processing unit (SPU) architecture, which ensures unparalleled threat detection and prevention capabilities. The inclusion of purpose-built chips allows for deep packet inspection at high speeds without hindering network performance. This architecture enables organizations to maintain high throughput while applying comprehensive security policies.
The FortiGate 800/800F series supports a wide array of security features, including intrusion prevention system (IPS), web filtering, and antivirus capabilities. These functionalities work together to monitor and protect against a range of cyber threats, from malware to sophisticated DDoS attacks. Additionally, the firewalls are equipped with FortiSandbox integration, providing automated malware analysis and ensuring that zero-day threats are effectively identified and neutralized in real-time.
In terms of networking capabilities, the FortiGate firewalls support advanced routing protocols, enabling seamless integration into existing network infrastructures. The series also includes support for VPN functionalities, which are crucial for secure remote access. With features like SSL inspection and secure SD-WAN, businesses can leverage flexible connectivity options while ensuring that sensitive data remains protected.
The FortiOS operating system enhances the FortiGate 800/800F series with centralized management capabilities, allowing administrators to configure and monitor security policies with ease. The intuitive user interface simplifies complex tasks, aiding in the rapid deployment and scalability of security measures across large networks.
High availability and redundancy features are also integral to the FortiGate 800/800F design. The series supports active-active and active-passive configurations, ensuring continuous protection and minimizing downtime during maintenance or unexpected failures.
In summary, the FortiGate 800/800F series stands out for its powerful performance, advanced security features, and robust networking capabilities. Organizations seeking to bolster their cybersecurity posture will find these firewalls to be invaluable tools in safeguarding their digital environments and ensuring business continuity in an increasingly complex threat landscape.