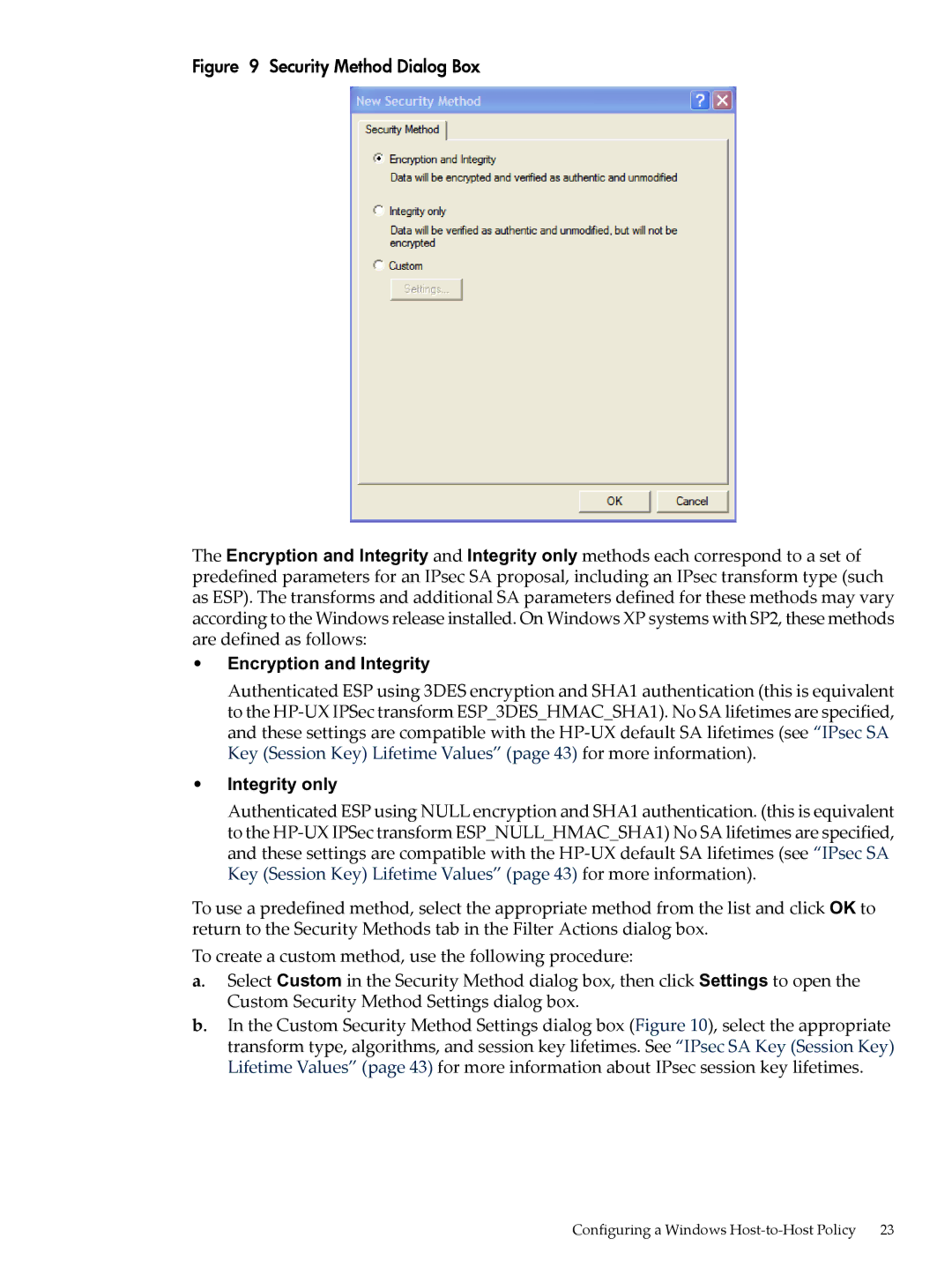
UX IPSec Software specifications
HP-UX IPSec Software is an integral component of the HP-UX operating system, providing robust and secure communication capabilities for enterprise environments. As organizations increasingly rely on secure networking solutions, HP-UX IPSec stands out with its comprehensive set of features and technologies designed to safeguard sensitive data.One of the core characteristics of HP-UX IPSec Software is its implementation of the Internet Protocol Security (IPSec) framework. This technology secures Internet Protocol (IP) communications through authentication and encryption, ensuring the integrity and confidentiality of data transmissions. By leveraging IPSec, HP-UX provides a secure method for connecting remote users and secure sites over untrusted networks, such as the internet.
A notable feature of the HP-UX IPSec Software is its support for both transport and tunnel modes. The transport mode encrypts only the payload of the IP packet, whereas the tunnel mode encapsulates the entire IP packet within a new packet, allowing for secure communications between entire networks. This flexibility enables organizations to tailor their security strategies based on specific use cases and requirements.
HP-UX IPSec also emphasizes interoperability and compliance with industry standards. The software supports various encryption algorithms and authentication methods, including those defined by the Internet Engineering Task Force (IETF). This commitment to open standards ensures that HP-UX can seamlessly integrate with a diverse range of networking infrastructures and security solutions.
In addition to its security features, HP-UX IPSec Software offers administration tools that simplify the configuration and management of IPSec policies. The software includes a user-friendly command-line interface, allowing system administrators to specify security associations and policies efficiently. Moreover, comprehensive logging and monitoring capabilities help organizations keep track of their security posture and detect potential vulnerabilities.
Another essential characteristic of HP-UX IPSec Software is its scalability. Designed to accommodate the needs of both small and large enterprises, it can handle increased loads and adapt to changing security demands without compromising performance.
In conclusion, HP-UX IPSec Software stands as a vital solution for organizations seeking to protect their data transmissions over IP networks. With its core technologies, such as transport and tunnel modes, adherence to industry standards, user-friendly administration tools, and scalability, it provides a formidable layer of security in an increasingly interconnected world. This makes it a preferred choice for enterprises aiming to enhance their network security frameworks.