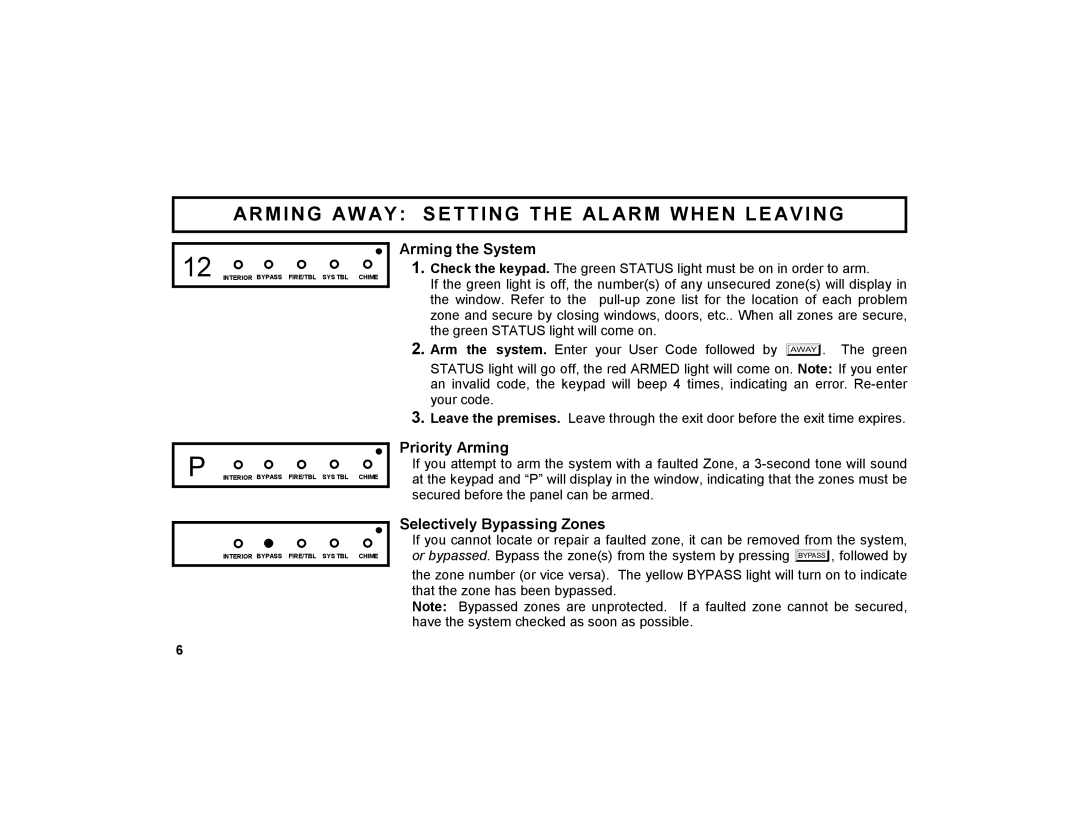
GEM-DXK3 specifications
Napco Security Technologies has long been a prominent player in the security industry, and its GEM-DXK3 series exemplifies the company's commitment to innovation and user-friendly design. This security control panel is tailored primarily for residential and small business applications, providing a versatile solution to meet the growing demands for safety and surveillance.One of the standout features of the GEM-DXK3 is its remarkable flexibility in compatibility. The panel supports a wide range of security sensors, including door/window contacts, motion detectors, and glass break detectors. This adaptability allows users to customize their security systems according to specific needs, ensuring comprehensive coverage throughout their property.
The GEM-DXK3 is equipped with advanced technology that enhances its performance and reliability. It uses the latest digital and analog signal processing, which ensures efficient operation and faster response times. This capability minimizes false alarms and provides more accurate alerts when a security breach occurs.
Moreover, the GEM-DXK3 is designed with user convenience in mind. It features an intuitive keypad interface that simplifies programming and operation. Users can easily navigate through settings and adjust their security preferences without hassle. Additionally, an optional LCD touchscreen is available, offering a modern approach to control and monitoring, further enhancing user experience.
Communication is key in security systems, and the GEM-DXK3 excels in this area. It supports multiple communication methods, including landline, internet, and cellular, ensuring that alerts can be sent to users and monitoring stations without interruption. This multi-channel approach provides an extra layer of reliability and security, as users are less likely to miss critical notifications.
The GEM-DXK3 also integrates seamlessly with Napco's mobile app, which allows users to monitor and control their security systems remotely. This functionality is especially beneficial for users who want to keep an eye on their properties while away, providing peace of mind and added convenience.
With its combination of flexibility, advanced technology, user-friendly design, and robust communication capabilities, Napco Security Technologies' GEM-DXK3 stands out as a comprehensive security solution. Whether for home or small business use, this control panel addresses the needs of modern security applications effectively.