REV1.0.1 1910010852
TL-ER6020 Gigabit Dual-WAN VPN Router
COPYRIGHT & TRADEMARKS
FCC STATEMENT
CE Mark Warning
Chapter 1 About this Guide
CONTENTS
Network Requirements
Chapter 4 Application
Hardware Specifications
Glossary
Chapter 5 CLI
The following items should be found in your package
Package Contents
One TL-ER6020 Router One Power Cord One Console Cable
Two mounting brackets and other fittings Installation Guide
1.2 Conventions
Symbol
Chapter 1 About this Guide
1.1 Intended Readers
Provides the possible solutions to the problems that may occur during
Lists the hardware specifications of this Router
Specifications
Appendix B FAQ
2.1 Overview of the Router
Powerful Data Processing Capability
Powerful Firewall
Chapter 2 Introduction
Hardware
2.2 Features
Dual-WAN Ports
Easy-to-use
Security
2.3 Appearance
2.3.1 Front Panel
Traffic Control
Indication
Reset button
LEDs
Status
Kensington Security Slot
Power Socket
2.3.2 Rear Panel
Grounding Terminal
3.1.2 System Mode
Chapter 3 Configuration
3.1 Network
3.1.1 Status
Figure 3-3 Network Topology - Non-NAT Mode
Figure 3-2 Network Topology - NAT Mode
NAT Mode
1 Static IP
3.1.3 WAN
Non-NAT Mode
Classic Mode
Static IP
Specify the bandwidth for receiving packets on the port
2 Dynamic IP
Upstream Bandwidth
Downstream
Dynamic IP
3 PPPoE
Dynamic IP Status
Figure 3-8 WAN - PPPoE
Enter the Account Name provided by your ISP. If you are not clear
PPPoE Settings
on. The connection can be re-established automatically when it
576-1492. The default MTU is 1480. It is recommended to keep the
Dynamic IP is selected, the obtained subnet address of WAN port is
Here allows you to configure the secondary connection. Dynamic IP
PPPoE Status
4 L2TP
correct and your network is connected well. Consult your ISP if
Figure 3-9 WAN - L2TP
L2TP Settings
Internet connection by the Connect or Disconnect button. It
L2TP Status
PPTP Settings
5 PPTP
Figure 3-10 WAN - PPTP
Account Name
PPTP Status Status
6 BigPond
Primary DNS Secondary DNS Upstream Bandwidth Downstream Bandwidth
BigPond Settings
BigPond Status
LAN
3.1.4 LAN
3.1.4.1 LAN
3.1.4.2 DHCP
DHCP Settings
3.1.4.4 DHCP Reservation
3.1.4.3 DHCP Client
3.1.5 DMZ
DHCP Reservation
List of Reserved Address
3.1.5.1 DMZ
DMZ
3.1.6 MAC Address
MAC Address
Set the MAC Address for LAN port
Set the MAC Address for WAN port
Set the MAC Address for DMZ port
3.1.7.1 Statistics
3.1.7 Switch
Statistics
3.1.7.2 Port Mirror
General
Port Mirror
Mirroring Port
Application Example
3.1.7.3 Rate Control
Rate Control
3.1.7.4 Port Config
3.1.7.5 Port Status
Port Config
3.2 User Group
3.1.7.6 Port VLAN
Port VLAN
List of Group
Group Config
3.2.1 Group
3.2.2 User
List of User
User Config
View Config
3.2.3 View
3.3.1.1 NAT Setup
3.3 Advanced
3.3.1 NAT
One-to-One NAT
3.3.1.2 One-to-One NAT
NAPT
NAT-DMZ
3.3.1.3 Multi-Nets NAT
List of Rules
Multi-Nets NAT
Application Example Network Requirements
list of Rules
Configuration procedure
3.3.1.4 Virtual Server
Protocol
Virtual Server
Port Triggering
3.3.1.5 Port Triggering
List of Rules
3.3.2 Traffic Control
3.3.1.6 ALG
ALG
3.3.2.1 Setup
Default Limit
General
Interface Bandwidth
3.3.2.2 Bandwidth Control
data flow might pass. Individual WAN port cannot be selected if
Bandwidth Control Rule
3.3.3.1 Session Limit
3.3.3 Session Limit
Session Limit
3.3.4.1 Configuration
3.3.4 Load Balance
3.3.3.2 Session List
3.3.4.2 Policy Routing
3.3.4.3 Link Backup
You can select Timing or Failover Mode
Status :
3.3.4.4 Protocol
Timing
Failover
List of Protocol
3.3.5 Routing
3.3.5.1 Static Route
Protocol
Static Route
3.3.5.2 RIP
Choose the menu Advanced→Routing→RIP to load the following page
List of RIP
3.3.5.3 Route Table
3.4 Firewall
3.4.1 Anti ARP Spoofing
3.4.1.1 IP-MAC Binding
IP-MAC Binding
3.4.1.2 ARP Scanning
3.4.1.3 ARP List
3.4.2 Attack Defense
Figure 3-49 Attack Defense
Packet Anomaly
3.4.3 MAC Filtering
MAC Filtering
Enable Attack
3.4.4 Access Control
3.4.4.1 URL Filtering
URL Filtering Rule
Select the mode for URL Filtering. “Keyword’’ indicates that all the
Configuration Procedure
3.4.4.3 Access Rules
Access Rules
3.4.4.2 Web Filtering
Select the Source IP Range for the entries, including the following
group on3.2.1 Group
Select the service for the entry. Only the service belonging to the
other service types can still pass through the Router. You can add
Priority
3.4.4.4 Service
List of Service
Service
3.4.5 App Control
3.4.5.1 Control Rules
Control Rules
3.4.5.2 Database
3.5.1 IKE
3.5 VPN
IKE Policy
3.5.1.1 IKE Policy
SA Lifetime Specify ISAKMP SA Lifetime in IKE negotiation
3.5.1.2 IKE Proposal
List of IKE Policy
IKE Proposal
List of IKE Proposal
3.5.2 IPsec
can be entered
3.5.2.1 IPsec Policy
IPsec Policy
Policy Name
Gateway of the remote peer should be set to the IP address of
IKE Mode
policy on VPN→IKE→IKE Policy page
which PCs on the remote network are covered by this policy. Its
de-encrypted, the key in Phase2 is easy to be de-encrypted, in
Manual Mode
Phase2. As it is independent of the key created in Phase1, this
de-encrypted. Without PFS, the key in Phase2 is created based
List of IPsec Policy IPsec
3.5.2.2 IPsec Proposal
IPsec Proposal
List of IPsec Proposal
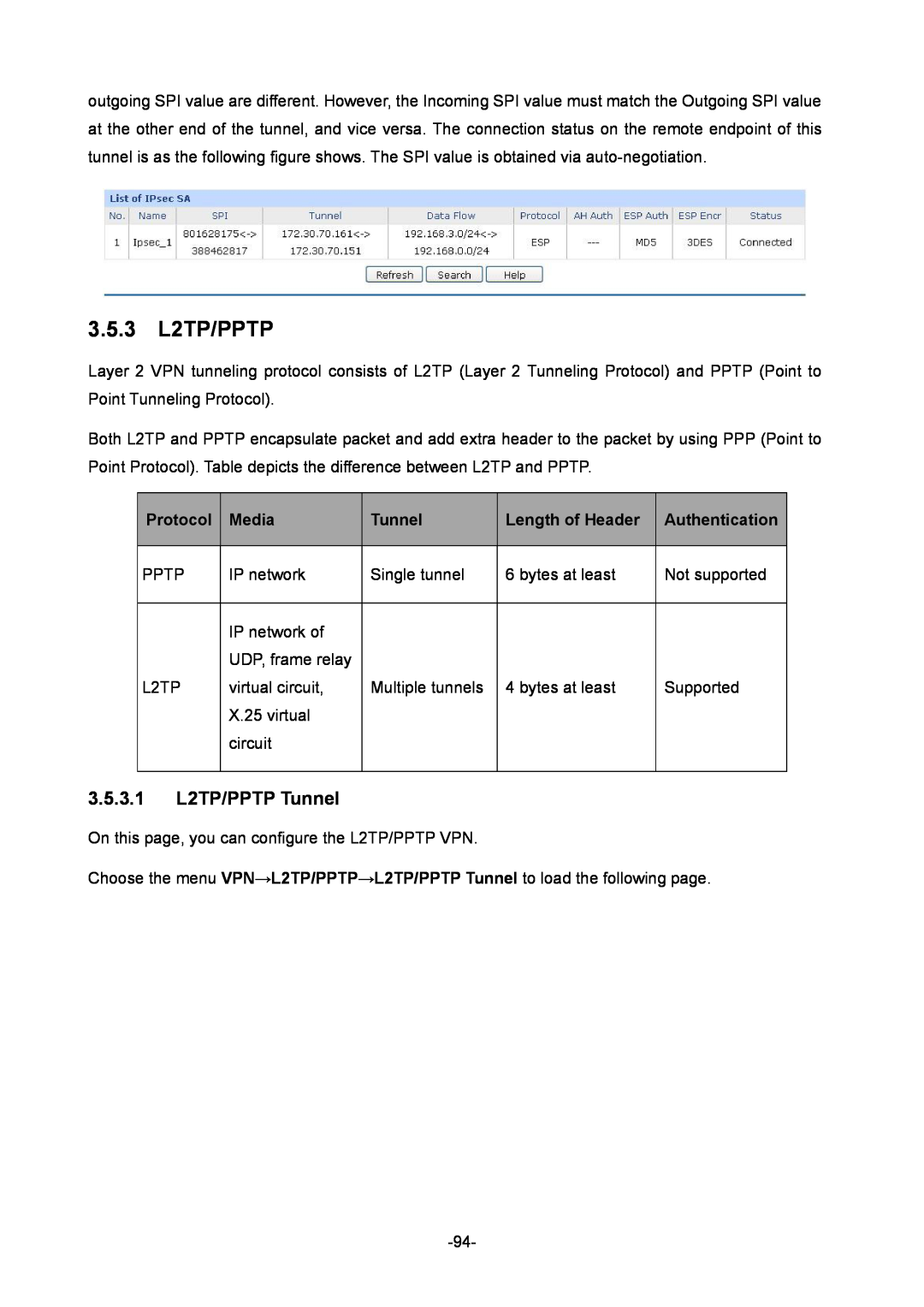
3.5.2.3 IPsec SA
Protocol
Authentication
3.5.3 L2TP/PPTP
3.5.3.1 L2TP/PPTP Tunnel
L2TP/PPTP Tunnel
Select the IP Pool Name to specify the address range for the servers
Enter the account name of L2TP/PPTP tunnel. It should be configured
List of IP Pool
List of Configurations
3.5.3.2 IP Address Pool
IP Address Pool
3.6.1.1 General
3.6 Services
3.6.1 PPPoE Server
3.5.3.3 List of L2TP/PPTP Tunnel
Figure 3-66 General The following items are displayed on this screen
3.6.1.2 IP Address Pool
3.6.1.3 Account
Account
is 48. If Enable Advanced Account Features is not selected, the
3.6.1.4 Exceptional IP
List of Account
3.6.2 E-Bulletin
3.6.1.5 List of Account
Exceptional IP
Specify the interval to release the bulletin
E-Bulletin
Interval
Title
List of E-Bulletin
3.6.3 Dynamic DNS
Dyndns DDNS
3.6.3.1 DynDNS
3.6.3.2 No-IP
List of DynDNS Account
No-IP DDNS
List of No-IP Account
3.6.3.3 PeanutHull
PeanutHull DDNS
3.6.3.4 Comexe
List of PeanutHull Account
Comexe DDNS
List of Comexe Account
3.6.4 UPnP
Administrator
3.7 Maintenance
3.7.1 Admin Setup
3.7.1.1 Administrator
Re-enter the new password for confirmation
3.7.1.2 Login Parameter
3.7.1.3 Remote Management
Remote Management
List of Subnet
3.7.2.1 Factory Defaults
3.7.2 Management
3.7.2.2 Export and Import
Import
3.7.2.3 Reboot
Configuration Version
Export
3.7.3 License
3.7.2.4 Firmware Upgrade
3.7.4 Statistics
3.7.4.1 Interface Traffic Statistics
Interface Traffic Statistics
Advanced WAN Information
3.7.4.2 IP Traffic Statistics
IP Traffic Statistics
3.7.5 Diagnostics
3.7.5.1 Diagnostics
Traffic Statistics
Tracert
Ping
3.7.5.2 Online Detection
List of WAN status
Displays whether the Online Detection is enabled
Config
3.7.6 Time
Current Time
List of Logs
3.7.7 Logs
The system is unusable
Level
Error conditions
Severity
4.1 Network Requirements
Chapter 4 Application
4.3.1 Internet Setting
4.2 Network Topology 4.3 Configurations
4.3.1.3 Link Backup
4.3.1.1 System Mode
4.3.1.2 Internet Connection
4.3.2.1 IPsec VPN
4.3.2 VPN Setting
1 IKE Setting
Settings
AuthenticationMD5 Encryption3DES
IKE Policy
2 IPsec Setting
IPsec Proposal
proposalIPsec1
proposalIPsec1 you just created
IPsec Policy
IP Address Pool
4.3.2.2 PPTP VPN Setting
L2TP/PPTPEnable ProtocolPPTP ModeServer UsernamePPTP Passwordabcdefg
L2TP/PPTP Tunnel
User
4.3.3 Network Management
4.3.3.1 User Group
Group
View
4.3.3.2 App Control
4.3.3.3 Bandwidth Control
1 Enable Bandwidth Control
2 Interface Bandwidth
3 Bandwidth Control Rule
Keep the default value
4.3.3.4 Session Limit
4.3.4 Network Security
4.3.4.1 LAN ARP Defense
1 Scan and import the entries to ARP List
2 Set IP-MAC Binding Entry Manually
4.3.4.2 WAN ARP Defense
3 Set Attack Defense
00-11-22-33-44-aa
4.3.4.3 Attack Defense
4.3.4.4 Traffic Monitoring
1 Port Mirror
2 Statistics
Figure 4-23 IP Traffic Statistics
Chapter 5 CLI
5.1 Configuration
Figure 5-3 Select the port to connect
Figure 5-2 Connection Description
Figure 5-5 Connection Properties Settings 148
Figure 5-4 Port Settings
5.2 Interface Mode
admin
Accessing Path
Logout or Access the next mode
enable
IP mac bind configuration
enable
Show command history
IP configuration
TP-LINK ip get lan Lan Ip Lan Mask
5.4 Command Introduction
5.4.2 ip-mac
5.4.1 ip
TP-LINK # sys export config
TP-LINK # sys reboot This command will reboot system, Continue?Y/N
TP-LINK # sys restore
This command will restore system, Continue?Y/N
TP-LINK sys show CPU Used Rate 1% TP-LINK # sys update
Password admin File name config.bin
Try to get the configuration file config.bin
Get configuration file config bin succeed, file size is 7104 bytes
TP-LINK # user get Username admin Password admin
TP-LINK user get Username admin Password admin
TP-LINK user set password Enter old password
Enter new password Confirm new password
1. history 2. sys show 3. history
View the history command
5.4.6 exit
TP-LINK history
Ports
Appendix A Hardware Specifications
Power
Standards
Appendix B FAQ
4. Make sure that the NAT DMZ service is disabled
data authentication, and anti-replay services. ESP encapsulates
Appendix C Glossary
Glossary
AH(Authentication Header)
for services such as IPSec that require keys. Before any IPSec
Description
enterprise
Telnet is used for remote terminal connection, enabling users to