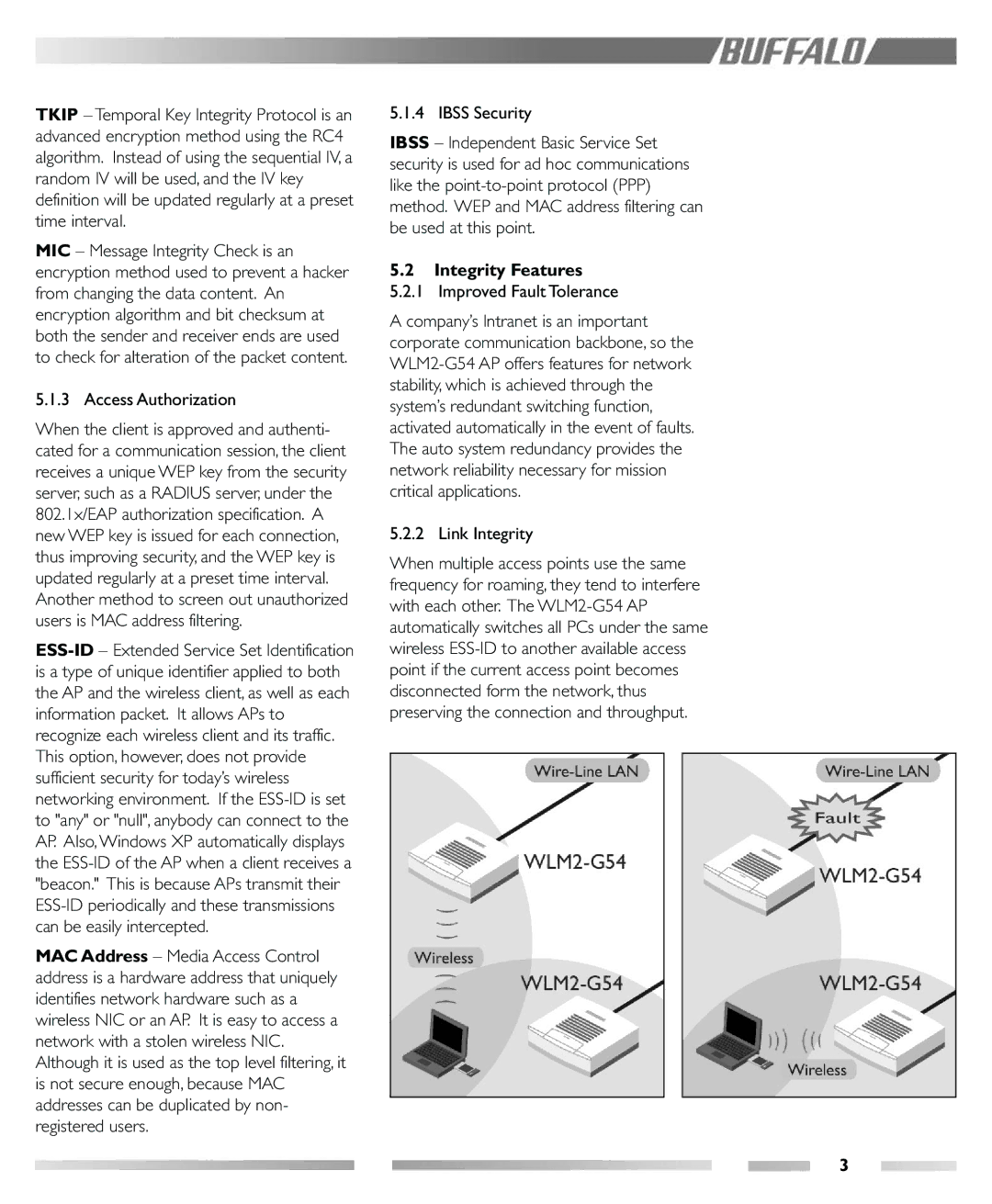
WLM2-G54 specifications
Buffalo Technology is known for its high-quality networking products, and one of their standout offerings is the WLM2-G54 wireless LAN router. This device caters to both home and small office users, prioritizing reliability and performance in wireless networking.The Buffalo WLM2-G54 operates on the IEEE 802.11g standard, providing impressive wireless speeds of up to 54 Mbps. This makes it ideal for activities such as web browsing, streaming videos, and online gaming. Its backward compatibility with older 802.11b devices ensures that users can seamlessly connect their legacy equipment without needing extensive upgrades.
One of the most notable characteristics of the WLM2-G54 is its robust security features. It supports various encryption methods, including WEP, WPA, and WPA2, allowing users to establish secure connections and protect their sensitive data from unauthorized access. The inclusion of a built-in firewall adds another layer of defense, safeguarding the network from external threats.
In terms of physical design, the WLM2-G54 is compact and user-friendly. It can easily fit into small spaces, making it a convenient addition to any home or office setup. The router includes multiple LAN ports for wired connections, ensuring that users can connect additional devices such as desktops, gaming consoles, and printers with ease.
The WLM2-G54 also incorporates advanced technologies to enhance performance. One such feature is Buffalo's "Client Mode," which allows the router to connect to existing networks and extend coverage. This flexibility is beneficial for users who need to bridge long distances or eliminate dead zones in larger spaces.
Another significant characteristic of the WLM2-G54 is its easy setup process. The device typically features a user-friendly web interface, enabling users to configure their network settings without requiring extensive technical knowledge. Additionally, Buffalo often provides firmware updates to improve performance and security, ensuring that users always have access to the latest enhancements.
Overall, Buffalo Technology’s WLM2-G54 wireless LAN router is a versatile, reliable choice for those looking to establish or expand their wireless networking capabilities. With its combination of speed, security, and user-friendly features, it stands out as an excellent option for both home and small office environments. Its ability to integrate with existing network infrastructures further solidifies its place as a valuable asset in modern networking solutions.