User Manual
D-Link DGS-3100 SERIES GIGABIT STACKABLE MANAGED SWITCH
V2.20
Precaución
FCC Warning
CE Mark Warning
Warnung
Table of Contents
Defining SNMP Host Table
Configuring Port Security
System Overview Viewing the Device Device Management Methods
Preface
DGS-3100 Series Gigabit Stackable Managed Switch User Manual
Safety Cautions General Precautions for Rack-Mountable Products
Figure 1 DGS-3100 Series 48 Port Front Panel
System Overview
Viewing the Device
DGS-3100 Series Front Panel
SNMP-Based Management
Device Management Methods
Command Line Console
Web Based Management Interface
NOTE A NOTE indicates important information that helps you make better use of your device
Safety Cautions
User Guide Overview
Notes, Notices, and Cautions
The product has been exposed to water
The power cable, extension cable, or plug is damaged
Unplug the power cable before removing the power supply
An object has fallen into the product
General Precautions for Rack-Mountable Products
Protecting Against Electrostatic Discharge
Battery Handling Reminder
View
Using the Web-Based User Interface
GETTING STARTED
Understanding the D-Link Embedded Web Interface
Information View
Figure 1-1. Device Information Page
1. Tree View
2. Device
1. Click Device Locator. The Device Locator Page opens
Using the Tool Menu
Displaying the Stack Status
Locating Devices
Figure 1-3 Config Backup and Restore Page
Backing up and Restoring Configuration Files
Field Http TFTP
1. Click Reset. The Factory Reset Page opens
Resetting the Device
Figure 1-4 Factory Reset Page
1. Click Firmware Download. The Firmware Download Page opens
Downloading the Firmware
Figure 1-5 Firmware Download Page
Field HTTP Download TFTP Download
2. Define the Select Unit to Reboot field
Rebooting the System
1. Click System Reboot. The System Reboot Page opens
Figure 1-6 System Reboot Page
Description
Using the Web System Components
Component
Name
CONFIGURING BASIC CONFIGURATION
Firmware Version Hardware Version System Time System Up Time
Viewing Device Information
Figure 2-1 Device Information Page
Field Device Type System Contact System Name System Location
BPDU Forwarding IGMP Snooping Broadcast Storm Control 802.1X Status
Field Boot Version MAC Address IP Address Subnet Mask Default Gateway
Login Timeout minutes Time Source 802.1D Spanning Tree DHCP Client
Safeguard Engine SNMP Trap SSL GVRP Setting Jumbo Frames
Figure 2-2 System Information Page
Defining System Information
System Contact System Name System Location Login Timeout minutes
3. Define the System Location and Login Timeout minutes fields
Field
Defining IP Addresses
1. Click Configuration IP Address. The IP Address Page opens
Figure 2-3 IP Address Page
Allocating Unit IDs
Managing Stacking
Managing Stacking Modes
Advanced Stacking
Defining a Stacking Back Up Master
Master Enabled Stacking Members
Assigning Unit IDs
Defining a Stacking Master
Discovering the Stacking Master
Stack Startup Process
Electing a Stacking Master
Allocating Unit IDs/Resolving Unit ID Conflicts
Unit and Stacking Port Configuration
Managing a New Manually Ordered Stack
Building Stacks - Quick Start
Stack Resiliency
Managing a Self-Ordered Stack
Adding Stacking Members to an Existing Manually Ordered Stack
Stack Management Examples
Replacing Failed Stacking-Members in a Running Stack
Building New Manually Ordered Stacks
Replacing a Failed Stack Master
Dividing Stacks
Page
Stacking Cable Failure
Merging Stacks
Inserting Excess Stacking Members
When switches are added to a running stack, the Unit ID Allocation and Duplicate ID Conflict Resolution process detects an error if too many switches are present in the stack, and no changes are to stacking members that originally belonged to the group managed by the newly elected master. The original switches retain their ID assignments and configurations. The stacking members that originally belonged to the group managed by the Stack Master that lost the Master Election process are shut down
Figure 2-4 Stacking Settings Page
Configuring Stacking
Field Stacking Master Current Stack ID New Stack ID after reset
Field Unit From Port To Port State Speed
Configuring Port Properties
Defining Ports
Figure 2-5 Port Setting Page
Field Flow Control Learning
From Port
Viewing Port Properties
Figure 2-6 Port Description Page
Unit
Static ARP Settings
ARP Settings
1. Click Configuration ARP Settings. The ARP Settings Page opens
Figure 2-7 ARP Settings Page
Figure 2-8 User Accounts Page
Configuring User Accounts
1. Click Configuration User Accounts. The User Accounts Page opens
Field User Name New Password Access Right Confirm New Password
1. Select an entry
2. Click . The user account is deleted, and the device is updated
To edit the User Accounts Page 1. Select a name on the User List
2. Click 3. Define the value
Severity
Managing System Logs
Figure 2-9 System Log Host Page
Index
Time level T1 T2 T3 T4
Configuring SNTP
Stratum Stratum Stratum Stratum
Example
Current Time
Figure 2-10 Time Settings Page
Field Time Setting Time in HH MM SS
Time Source
Configuring Daylight Savings Time
Figure 2-11 TimeZone Settings Page
Field From Which Week of the Month From Day of Week From Month
DST Repeating Settings Sections
Field Daylight Savings Time State
Daylight Saving Time Offset in Minutes Time Zone Offsetfrom GMT
Field FromMonth FromDay FromTime ToMonth ToDay ToTime
DST Annual Settings Section
Parameters Authentication Privacy Key Management
Configuring SNMP
2. Define the View Name, Subtree OID and View Type fields
Defining SNMP Views
Figure 2-12 SNMP View Table Page
Field View Name Subtree OID View Type
Community/View TestReadView PWriteView PrivateView
Defining SNMP Groups
Figure 2-13 SNMP Group Table Page
Field Group Name Read View Name Write View Name
Field Notify View Name Security Model Security Level
Field User Name Group Name SNMP V3 Encryption
Defining SNMP Users
Auth-Protocol by Password Password Confirm Password
Figure 2-14 SNMP User Table Page
Confirm Key
Auth-Protocol by Key
2. Define the User Name, Group Name, and SNMP V3 Encryption fields
Figure 2-15 SNMP Community Table Page
Defining SNMP Communities
Access Rights
2. Define the Community Name, and View Name, Access Right fields
To define the SNMP Host Table Page
Defining SNMP Host Table
Figure 2-16 SNMP Host Table Page
SNMP Version
Host IP Address
Community String / SNMPv3 User Name
Field Engine ID Use Default
Defining SNMP Engine ID
Figure 2-17 SNMP Engine ID Page
Figure 2-18 SNMP Configuration Trap Page
Enabling SNMP Traps
Field SNMP Traps SNMP Authentication Traps
Figure 2-19 DHCP Auto Configuration Page
DHCP Auto Configuration
Field DHCP Auto Configuration
Figure 2-20 Firmware Information Page
Dual Image Services
Firmware Information
Field Unit Image Version Update Time
Image
Config Firmware Image
Figure 2-21 Config Firmware Image Page
Defines the image file used for reboot. The possible values are
CONFIGURING L2 FEATURES
Field Jumbo Frame
Enabling Jumbo Frames
1. Click L2 Features Jumbo Frame. The Jumbo Frame Page opens
Figure 3-1. Jumbo Frame Page
Notes about VLANs on the DGS-3100 Series
Configuring VLANs
Understanding IEEE 802.1p Priority
VLAN Description
Figure 3-2. IEEE 802.1Q Packet Forwarding
Term Untagging Ingress port Egress port
Figure 3-3. IEEE 802.1Q Tag
802.1Q VLAN Tags
Figure 3-4. Adding an IEEE 802.1Q Tag
Tagging and Untagging
Port VLAN ID
Ingress Filtering
Switch Ports
Default VLANs
VLAN and Trunk Groups
VLAN Status
Field VID VLAN Name Untag VLAN Ports Tag VLAN Ports
Defining VLAN Properties
1. Click L2 Features 802.1Q VLAN. The VLAN Configuration Page opens
Figure 3-5. VLAN Configuration Page
Figure 3-6. Add/Edit VLAN Information Page
1. Click L2 Features GVRP Settings. The GVRP Setting Page opens
Configuring GVRP
Figure 3-7. GVRP Setting Page
Acceptable Frame Type
Field GRVP Global Setting Unit From Port To Port PVID GVRP Ingress
4. Define the PVID, GVRP, Ingress, and Acceptable Frame Type fields
Field Unit Group ID Type Ports
Defining Trunking
1. Click L2 Features Trunking. The Trunking Configuration Page opens
Figure 3-8. Trunking Configuration Page
Notes about Trunking on the DGS-3100 Series
Forwarding Ports
Traffic Segmentation
Figure 3-9. Traffic Segmentation Page
Source Ports
4. Define the Port-Priority and LACP Timeout fields
Configuring LACP
Figure 3-10. LACP Port Settings Page
Timeout
Figure 3-11. IGMP Snooping Page
Defining IGMP Snooping
1. Click L2 Features IGMP Snooping. The IGMP Snooping Page opens
Leave Timer
2. Click . The Static Router Ports Settings Page opens
Host Timeout
Router Timeout
Static Router Port Setting Edit button
Ports
Static Router Ports
Dynamic Router Ports
Field Status Unit Target Port Source Port
Configuring Port Mirroring
1. Click L2 Features Port Mirroring. The Port Mirroring Page opens
Figure 3-13. Port Mirroring Page
2. Define the Status, Unit, and Target fields
4. Define the Unit, Tx, and Rx. fields under Source Port Setting
Field None
Defines that port mirroring is not applied to the ports
Version Classic STP Rapid STP Multiple STP
Configuring Spanning Tree
STP Version
Defining Spanning Tree Global Parameters
Figure 3-14. STP Bridge Global Settings Page
STP Status
Bridge Forward Delay
Bridge Priority 0
Bridge Max Age 6
Bridge Hello Time 1
Figure 3-15. STP Port Settings Page
Defining STP Port Settings
Field Unit From Port To Port Cost 0=Auto
Field Edge Forwarding BPDU P2P State
Revision Level
Defining Multiple Spanning Tree Configuration Identification
Figure 3-16. MST Configuration Identification Page
Configuration Name
Figure 3-17. MSTI Config Information Page
Defining MSTP Port Information
Field Unit Port Instance ID Internal Path Cost Priority Status
4. Define the Internal Path Cost and Priority fields
Field Role
Field Aging Time VID MAC Address Unit Port
Defining Forwarding and Filtering
Defining Unicast Forwarding
Figure 3-18. Unicast Forwarding Page
Egress
Defining Multicast Forwarding
Figure 3-19. Multicast Forwarding Page
Multicast MAC Address
3. Select either all, or individual ports
4. Click To restore the default settings 1. Click
The default settings are restored
The entry is deleted, and the device is updated
Configuring 1p
CONFIGURING QUALITY OF SERVICE
Figure 4-1. Mapping QoS on the Switch
Understanding QoS
No Limit
Defining Bandwidth Settings
1. Click QoS Bandwidth Control. The Bandwidth Control Page opens
Figure 4-2. Bandwidth Control Page
Broadcast Storm Broadcast and Multicast Storm
Configuring Storm Control
Figure 4-3. Traffic Control Settings Page
Field Unit From Port To Port Storm Control Type State Threshold 3500
Figure 4-4. 802.1P Default Priority Page
Mapping Ports to Packet Priorities
2. Define the Unit, From Port, To Port, Prioirity fields
Figure 4-5. 802.1P User Priority Page
Mapping Priority to Classes Queues
Field Priority Class ID
Field Class ID Mechanism Weight
Configuring QoS Scheduling Mechanism
Figure 4-6. QoS Scheduling Mechanism Page
Figure 4-7. Multi-Layer CoS Setting Page
Defining Multi-Layer CoS Settings
SECURITY FEATURES
Field Safeguard Engine
Configuring Safeguard Engine
1. Click Security Safeguard Engine. The Safeguard Engine Page opens
Figure 5-8. Safeguard Engine Page
Figure 5-9.Trusted Host Page
Configuring Trust Host
Field IP1 Access to Switch IP2 Access to Switch IP3 Access to Switch
1. Click Security Trusted Host. The Trusted Host Page opens
Figure 5-10. Port Security Page
Configuring Port Security
Field Unit From Port To Port Admin State Max Address0-64 Port
1. Click Security Port Security. The Port Security Page opens
Figure 5-11 Guest VLAN Page
Configuring Guest VLANs
Field Max Learning Addr
1. Click Security Guest Vlan. The Guest VLAN Page opens
Component Authenticators Supplicants/Clients Authentication Server
Configuring Port Authentication
State Controlled Access Uncontrolled Access
ServerTimeout 1-65535 sec
1. Click Security 802.1X Setting. The 802.1X Setting Page opens
Figure 5-12. 802.1X Setting Page
SuppTimeout 1-65535 sec
Mode
Control
ReAuthEnabled
1. Click Security 802.1X Setting. The 802.1X Setting Page opens
SuppTimeout 1-65535 sec
ServerTimeout 1-65535 sec
Unit
Field
Description
Control
Page
DGS-3100 Series Gigabit Stackable Managed Switch User Manual
DGS-3100 Series Gigabit Stackable Managed Switch User Manual
Figure 5-13. Authentic RADIUS Server Page
Defining RADIUS Settings
Field Succession RADIUS Server Authentic Port Accounting Port Key
1. Click Security SSL. The SSL Configuration Settings Page opens
Configuring Secure Socket Layer Security
Field SSL Status Ciphersuite Status
Figure 5-14. SSL Configuration Settings Page
Figure 5 -15. SSH Configuration Page
Configuring Secure Shell Security
Field SSH Server Status Port
Defining SSH Algorithm Settings
Data Integrity Algorithm
Figure 5-16. SSH Algorithm Settings Page
Public key
Public Key Algorithm
Figure 5-17. Application Authentication Settings Page
Defining Application Authentication Settings
Field Application Login Method List Enable Method List
Protocol
Configuring Authentication Server Hosts
Figure 5-18. Authentication Server Host Page
Timeout 1-30secs
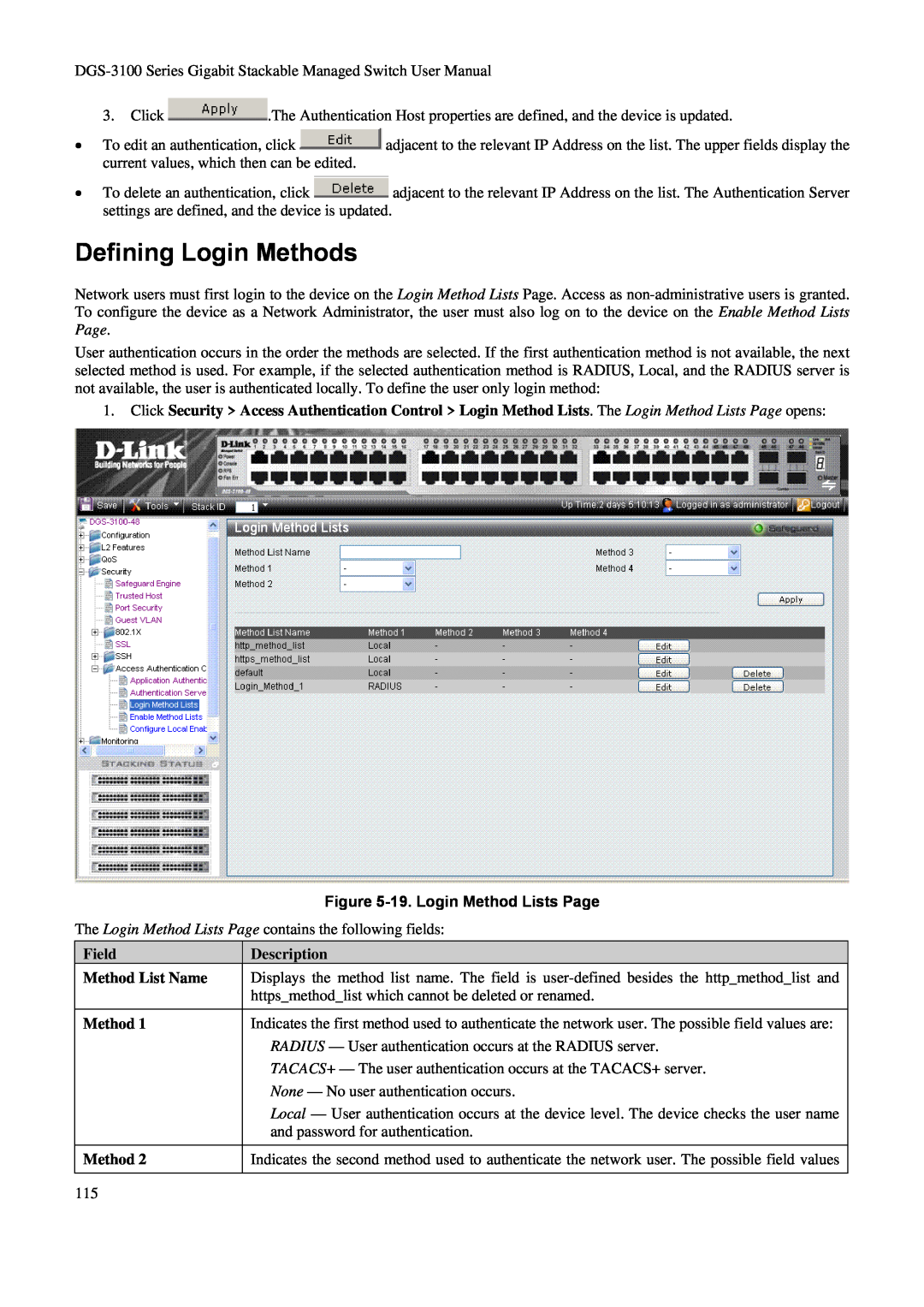
Figure 5-19. Login Method Lists Page
Defining Login Methods
Field Method List Name Method Method
Description are
Field Method Method
Figure 5-20. Enable Method Lists Page
Defining Enable Methods
Field Method List Name Method
Field Method Method Method
Provide the current network Enable password
Configuring Local Enable Password
Figure 5-21. Configure Local Enable Password Page
Old Local Enable Password
MONITORING THE DEVICE
Field Master ID Backup ID Box ID Runtime version H/W version
Viewing Stacking Information
Figure 6-1 Stacking Information Page
Field Utilization Time Interval Record Number Show/Hide
Viewing CPU Utilization
1. Click Monitoring CPU Utilization. The CPU Utilization Page opens
Figure 6-2. CPU Utilization Page
Figure 6-3. Port Utilization Page
Viewing Port Utilization
Field Unit Port Utilization Time Interval Record Number Show/Hide
Field Unit Port Packet Size Analysis - Selected Port Number
Viewing Packet Size Information
1. Click Monitoring Packet Size. The Packet Size Page opens
Figure 6-4. Packet Size Page
Field Unit Port Bytes Packets Time Interval Record Number Show/Hide
Viewing Received Packet Statistics
1. Click Monitoring Packets ReceivedRX. The ReceivedRX Page opens
Figure 6-5. ReceivedRX Page
Field Unit Port Unicast Multicast Broadcast Time Interval
Viewing UMBcast Packet Statistics
1. Click Monitoring Packets UMBcastRX. The UMBcastRX Page opens
Figure 6-6. UMBcastRX Page
Figure 6-7. TransmittedTX Page
Viewing Transmitted Packet Statistics
Field Unit Port Bytes Packets Time Interval
Field Record Number Show/Hide
Accepts Rejects
Viewing RADIUS Authenticated Session Statistics
Figure 6-8. RADIUS Authentication Page
Field Time Interval Server UDP Port Timeouts Requests Challenges
Figure 6-9 Browse ARP Table Page
Viewing ARP Table
Field VLAN Name IP Address Total Entries MAC Address Type
Figure 6-10 Browse Router Port Page
Viewing Router Ports
Field VID Unit Port
Figure 6-11 Browse Session Table Page
Viewing Session Table
Field ID From User Privilege Name
Figure 6-12 IGMP Snooping Group Page
Viewing IGMP Group Information
Field VID VLAN Name VLAN Name Multicast Group MAC Address Port
Figure 6-13 MAC Address Table Page
Defining Dynamic and Static MAC Addresses
Field Unit Port VLAN Name MAC Address VID Type
To clear dynamic entries, click
2. Select the Stacking member in the Unit field
3. Define the Port, VLAN Name, and MAC Address fields 4. Click
To view all entries, click To clear static entries, click
Field ID Time Log Description Severity
Viewing System Log
1. Click Monitoring System Log. The System Log Page opens
Figure 6-14 System Log Page
MANAGING POWER OVER ETHERNET DEVICES
PoE Enable
Defining PoE System Information
1. Click PoE PoE Port Setting. The PoE Port Setting Page opens
Figure 7-1 PoE Port Setting Page
Off - Indicates that the power supply unit is not functioning
Indicates the power consumption is 7W
Indicates the power consumption is 15.4W
Normal - Indicates that the power supply unit is functioning
System Power Threshold
Displaying and Editing PoE System Information
1. Click PoE PoE System Setting. The PoE System Setting Page opens
Figure 7-2 PoE System Setting Page
DEFINING ACCESS PROFILE LISTS
From
ACL Configuration Wizard
Figure 8-1 ACL Configuration Wizard Page
Service Type
UDP Source Port - Matches the packet to the UDP Source Port
TCP Source Port - Matches the packet to the TCP Source Port
TCP Destination Port - Matches the packet to the TCP Destination Port
UDPAll - Specifies a UDP Packets filtering
Adding ACL Profiles
Defining Access Profile Lists
1. Click ACL Access Profile List. The ACL Profile List Page opens
Displays the access rule
L2 ACL
Figure 8-3 Add ACL Profile Page
L3 ACL
Figure 8-5 ACL Profile L2 ACL Tagged MAC Address Page
Defining Level 2 ACL
Figure 8-4 ACL Profile L2 ACL Tagged Page
To define L2 MAC Address ACL profile
Figure 8-6 ACL Profile L2 ACL Tagged VLAN Page
Source MAC Mask
Destination MAC Mask
To define L2 802.1Q VLAN ACL profile
Figure 8-7 ACL Profile L2 ACL Tagged Ether Type Page
To define L2 Ether Type ACL profile
Figure 8-8 ACL Profile L2 ACL Untagged Page
Defining Level 3 ACL
Figure 8-9 Add ACL Profile L3 Page
Figure 8-11 ACL Profile L3 ACL ICMP IPv4 Address Page
To define L3 IPv4 DSCP ACL profile
Figure 8-10 ACL Profile L3 ACL ICMP IPv4 DSCP Page
To define L3 IPv4 Address ACL profile
ICMP Code
To define L3 ICMP ACL profile
Figure 8-12 ACL Profile L3 ACL ICMP Page
ICMP Type
Figure 8-13 ACL Profile L3 IGMP Page
To define L3 IGMP ACL profile
Figure 8-14 ACL Profile L3 IGMP Selected Page
To define L3 TCP Port ACL profile
Figure 8-15 ACL Profile L3 TCP Page
Figure 8-16 ACL Profile L3 TCP Port Page
Figure 8-17 ACL Profile L3 TCP Flag Page
To define L3 TCP Flag ACL Profile
Figure 8-18 ACL Profile L3 UDP Page
If L3 ACL UDP is selected, the page updates as follows
Figure 8-19 ACL Profile L3 UDP Port Page
Description
Filter
Defining Access Rules Lists
Click ACL Access Profile List The Access Profile List Page opens
Figure 8-20 Access Profile List Page
Source ID
1. Click . The Add Access Rule Page opens
Figure 8-21 Add Access Rule Page IP based ACL
Access ID
2. Define the Rule Detail fields
3. Click . The rule is changed, and the device is updated
Profile ID list box
Finding ACL Rules
1. Click ACL ACL Finder The ACL Finder Page opens
Figure 8-22 ACL Finder Page
Ether Type
Figure 8-23 Rule Detail Page
Source MAC
Destination MAC
Notes about ‘IP’ and ‘MAC’ Based ACLs in the DGS-3100 Series
Notes about ACLs capacity in the DGS-3100 Series
Limited Lifetime Warranty for the product is defined as follows
Reorient or relocate the receiving antenna
Product Registration
Warranty Period
LIMITED WARRANTY
Product Type
What Is Not Covered
What You Must Do For Warranty Service
is not contemplated in the documentation for the product, or if the model or serial number has been altered, tampered with, defaced or removed
Trademarks
FCC Warning
Copyright Statement
Tech Support for customers within Canada
TECHNICAL SUPPORT
Technical Support
Tech Support for customers within the United States
D-Link UK & Ireland Technical Support over the Telephone
For Customers within The United Kingdom & Ireland
For Customers within Canada
D-Link UK & Ireland Technical Support over the Internet
Technische Unterstützung
Link
Assistance technique
Support technique destiné aux clients établis en France
Support technique destiné aux clients établis au Canada
Asistencia Técnica de D-Link por teléfono
Asistencia Técnica
Asistencia Técnica de D-Link a través de Internet
Gli ultimi aggiornamenti e la documentazione sono
Supporto tecnico
Supporto tecnico per i clienti residenti in Italia
D-Link Mediterraneo S.r.L
Tech Support for customers within Luxemburg
Technical Support
Tech Support for customers within the Netherlands
Tech Support for customers within Belgium
Pomoc techniczna
D-Link poskytuje svým zákazníkům bezplatnou technickou podporu
Technická podpora
Aktualizované verze software a uživatelských příruček najdete na
webové stránce firmy D-Link
D-Link Magyarország
Technikai Támogatás
Du kan finne programvare oppdateringer og bruker
Teknisk Support
Teknisk Support
D-Link Teknisk telefon Support
Hverdager kl. 0800
D-Link teknisk support på Internettet
D-Link teknisk support over telefonen
Tlf. 7026
Arkisin klo. 9 - 21 numerosta
Teknistä tukea asiakkaille Suomessa
D-Link tarjoaa teknistä tukea asiakkailleen
Tuotteen takuun voimassaoloajan Tekninen tuki palvelee seuraavasti
D-Link tillhandahåller teknisk support till kunder i Sverige
Teknisk Support för kunder i Sverige
På vår hemsida kan du hitta mer information om mjukvaru
uppdateringar och annan användarinformation
Assistência Técnica
Suporte Técnico
Suporte Técnico para clientes no Portugal
Você pode encontrar atualizações de software e documentação de
Τηλ 210 86 11 Φαξ 210 86 53 Δευτέρα-Παρασκευή
Τεχνική Υποστήριξη
Για πελάτες εντός του Ελλαδικού χώρου
Τηλεφωνική υποστήριξη D-Link
Indonesia, Malaysia, Singapore and Thailand
Tech Support for customers in
Australia
India
e-mail amostafa@dlink-me.com
Technical Support
Tech Support for customers in
http//support.dlink-me.com
D-Link предоставляет бесплатную поддержку для клиентов
Техническая поддержка
Обновления программного обеспечения и документация
доступны на Интернет-сайте D-Link
Asistencia Técnica
São Paulo +11-2185-9301 Segunda à sexta Das 8h30 às 18h30
Suporte Técnico
Suporte Técnico para clientes no Brasil
Telefone
0800-002-615
D-Link 友訊科技 台灣分公司 技術支援資訊
電子郵件:dssqaservice@dlink.com.tw
D-Link 免付費技術諮詢專線
diperoleh pada situs web D-Link
Dukungan Teknis
Dukungan Teknis untuk pelanggan
Update perangkat lunak dan dokumentasi pengguna dapat
技术支持中心电话:8008296688 技术支持中心传真:02885176948
技术支持
您可以在 D-Link 的官方網站找到產品的軟件升級和使用手冊
办公地址:北京市东城区北三环东路 36 号 环球贸易中心 B 座 26F 02-05 室 邮编
International Offices
Product Serial No
Product installed in type of computer
Registration Card All Countries and Regions Excluding USA
Product Model