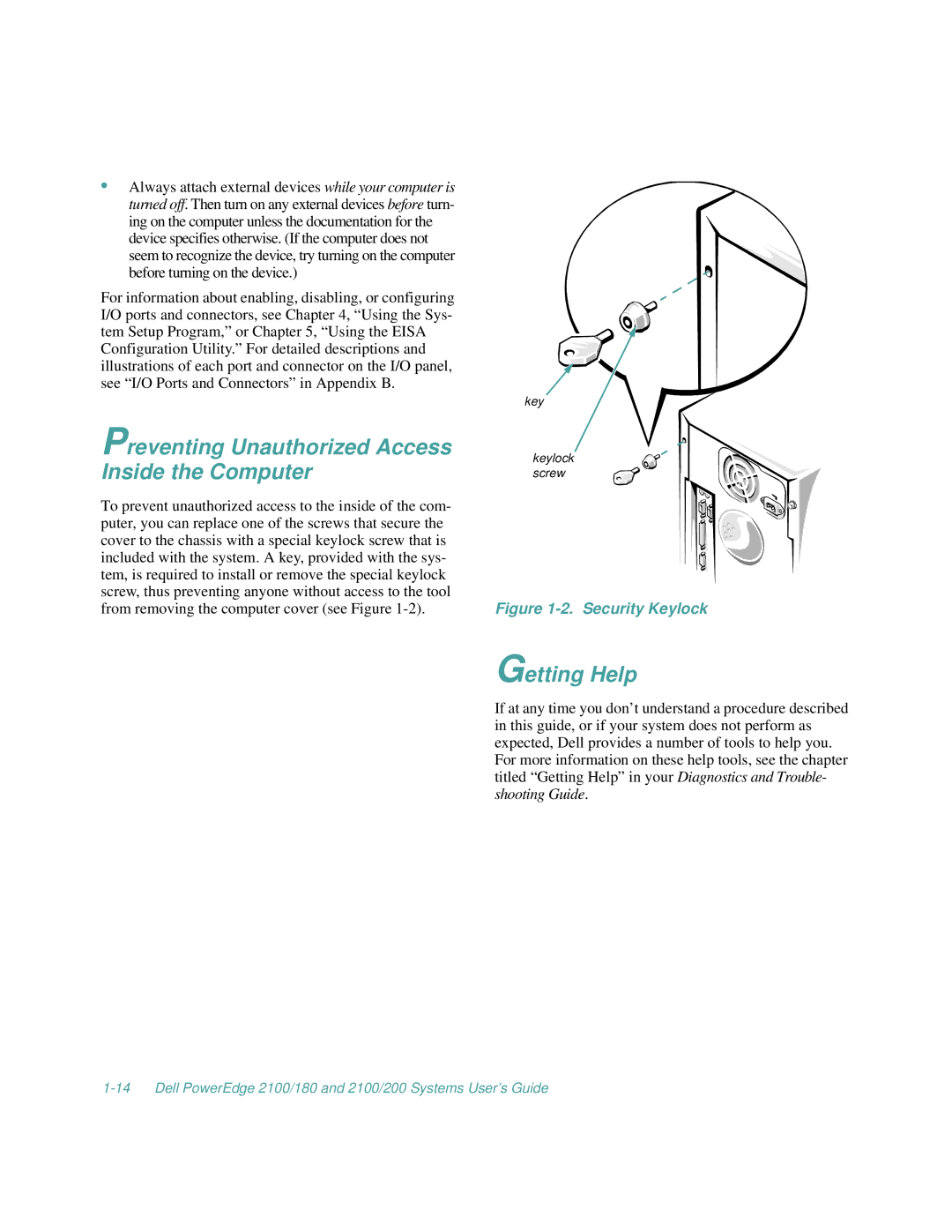
2100/180, 2100/200 specifications
The Dell 2100/200 and Dell 2100/180 are innovative offerings from Dell that cater to the demands of a variety of users, ranging from small businesses to larger enterprises. Both models are designed to deliver high performance and reliability, making them indispensable tools in the modern computing environment.The Dell 2100/200 features an impressive Intel processor that ensures fast and efficient performance, making it suitable for multitasking and handling complex applications. Coupled with a generous RAM configuration, this model can easily manage demanding workloads, resulting in smoother performance and faster processing times. In contrast, the Dell 2100/180, while slightly less powerful, still maintains robust performance levels that are well-suited for general productivity tasks and everyday use.
Both models come equipped with ample storage options, featuring hard disk drives that provide significant space for data and application storage. Users can choose between traditional HDDs and solid-state drives (SSDs), allowing them to prioritize speed and performance based on their specific needs. The flexibility in storage options ensures that users can customize their systems according to their requirements, enhancing the overall user experience.
Connectivity is another area where the Dell 2100 series excels. Both models come with a range of ports including USB, HDMI, and Ethernet, allowing for seamless connectivity with various peripherals and networks. This versatility makes the machines ideal for environments where multiple devices need to be connected simultaneously, whether for presentations, data transfer, or internet access.
In terms of energy efficiency, both the Dell 2100/200 and Dell 2100/180 incorporate advanced cooling technologies that minimize energy consumption while maximizing performance. This not only helps reduce operational costs but also contributes to a more sustainable computing environment.
The design of these models is another distinguishing feature. With a compact form factor, they fit easily into office spaces while maintaining a professional appearance. Their durable build quality ensures longevity, making them a worthwhile investment for businesses.
Overall, the Dell 2100/200 and Dell 2100/180 serve as powerful and reliable machines that combine advanced technologies and user-centric designs. Whether for business or personal use, these models provide a solid foundation for effective computing, ensuring that users can achieve their goals efficiently and effectively.