which contains the issuer’s public key, into the trusted root certification authority certificate store of the host computer. Intermediate or subordinate certification authorities are trusted only if they have a valid certification path from a trusted root certification authority.
Server Name: Enter the authentication server name.
Server name must match exactly: When selected, the server name must exactly match the server name found on the certificate.
Domain name must end in specified name: When this is selected, the server name field identifies a domain. The certificate must use a server name belonging to this domain or one of its
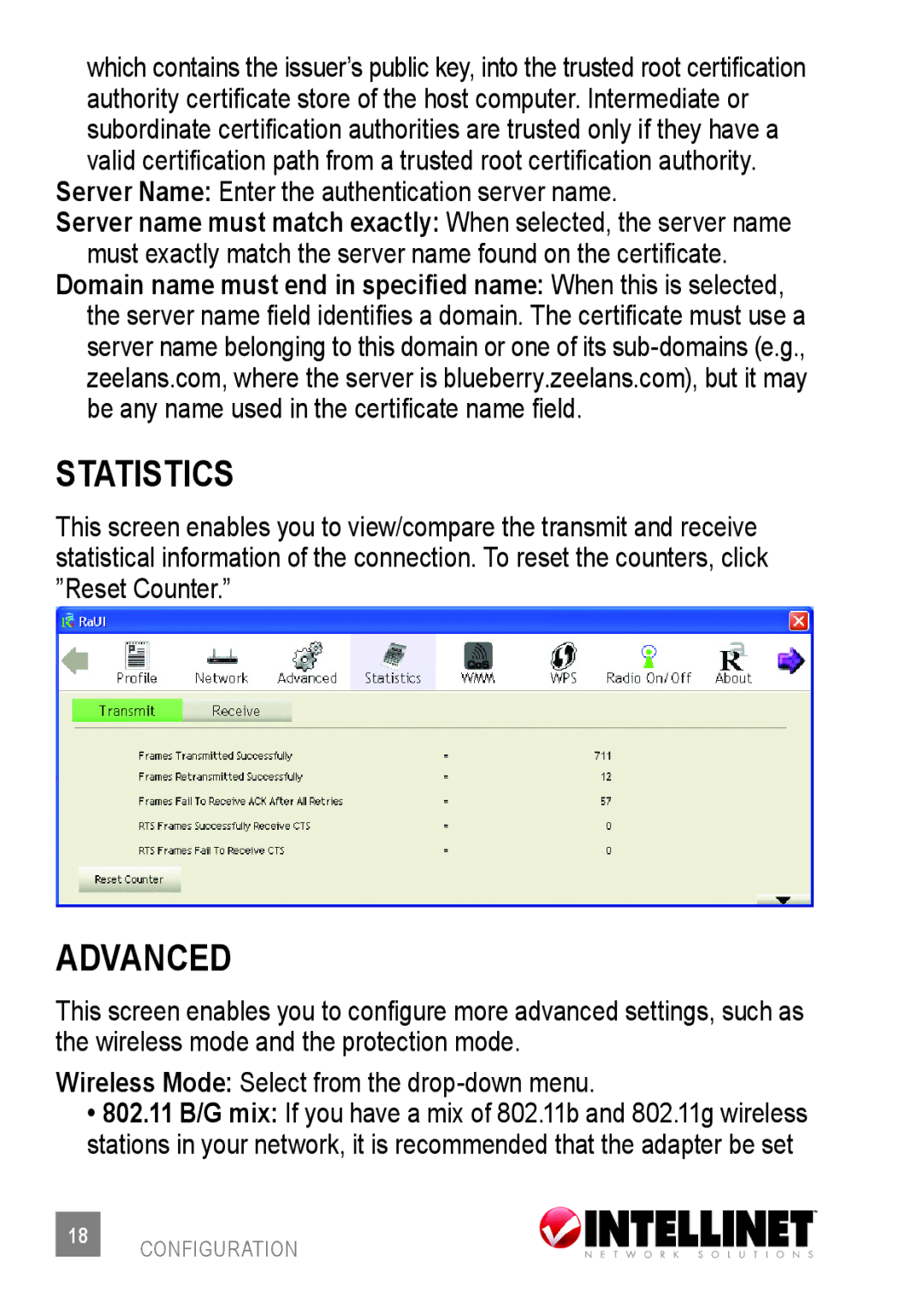
statistics
This screen enables you to view/compare the transmit and receive statistical information of the connection. To reset the counters, click ”Reset Counter.”
Advanced
This screen enables you to configure more advanced settings, such as the wireless mode and the protection mode.
Wireless Mode: Select from the drop-down menu.
•802.11 B/G mix: If you have a mix of 802.11b and 802.11g wireless stations in your network, it is recommended that the adapter be set