P320W Support Notes
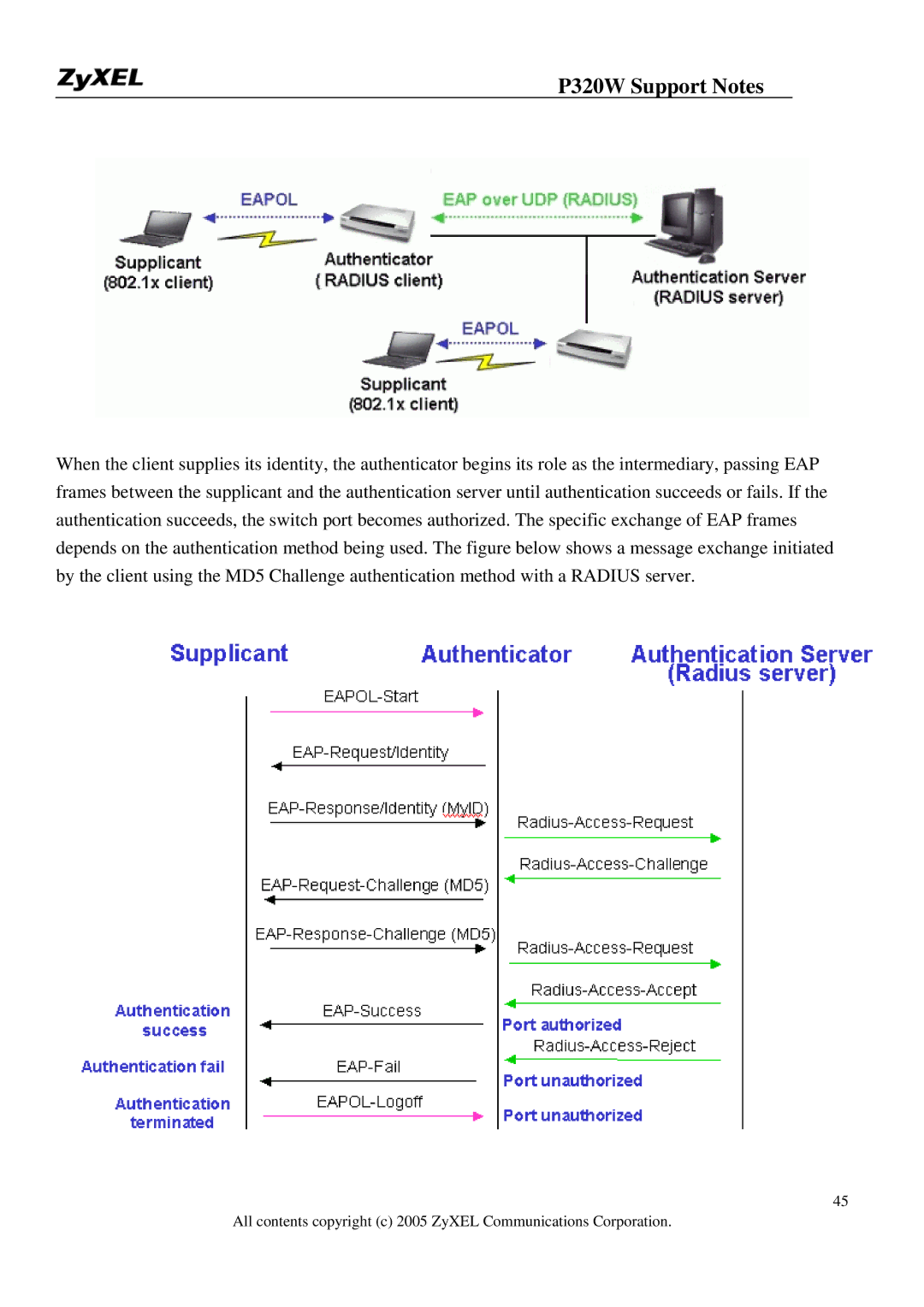
When the client supplies its identity, the authenticator begins its role as the intermediary, passing EAP frames between the supplicant and the authentication server until authentication succeeds or fails. If the authentication succeeds, the switch port becomes authorized. The specific exchange of EAP frames depends on the authentication method being used. The figure below shows a message exchange initiated by the client using the MD5 Challenge authentication method with a RADIUS server.
45
All contents copyright (c) 2005 ZyXEL Communications Corporation.