|
|
|
|
|
|
| Features in |
|
|
| 12 | ||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
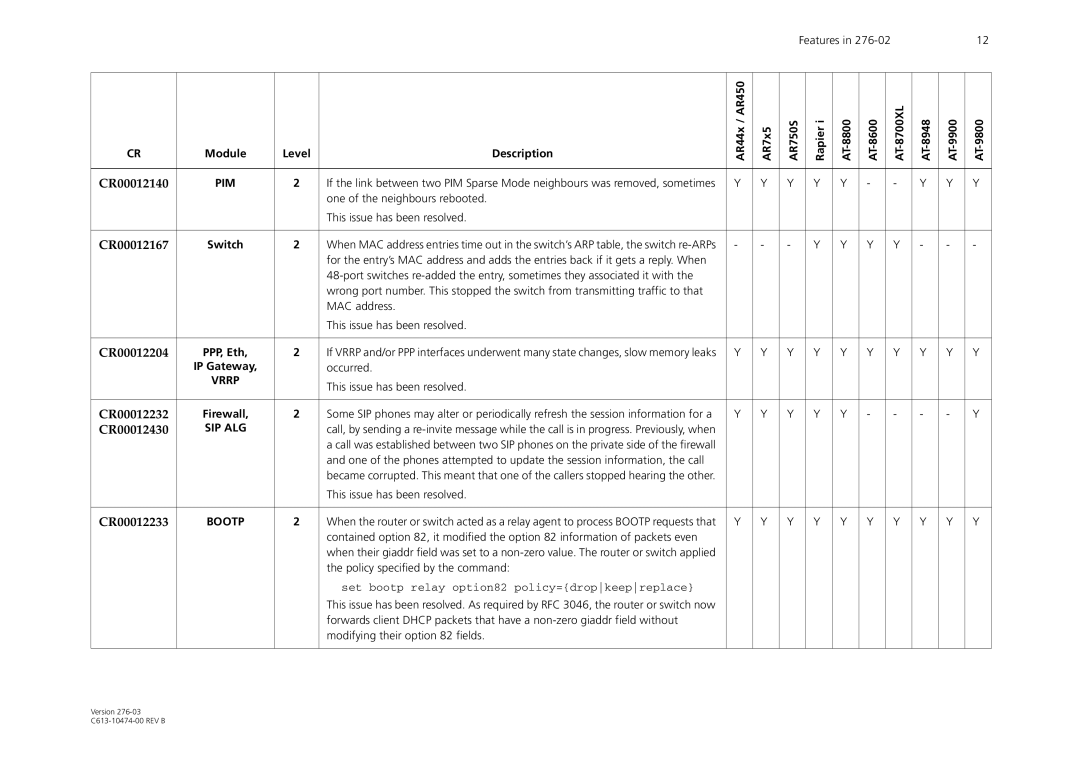
CR | Module | Level | Description | AR44x / AR450 | AR7x5 | AR750S | Rapier i | ||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00012140 | PIM | 2 | If the link between two PIM Sparse Mode neighbours was removed, sometimes | Y | Y | Y | Y | Y | - | - | Y | Y | Y |
|
|
| one of the neighbours rebooted. |
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00012167 | Switch | 2 | When MAC address entries time out in the switch’s ARP table, the switch | - | - | - | Y | Y | Y | Y | - | - | - |
|
|
| for the entry’s MAC address and adds the entries back if it gets a reply. When |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
| wrong port number. This stopped the switch from transmitting traffic to that |
|
|
|
|
|
|
|
|
|
|
|
|
| MAC address. |
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00012204 | PPP, Eth, | 2 | If VRRP and/or PPP interfaces underwent many state changes, slow memory leaks | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| IP Gateway, |
| occurred. |
|
|
|
|
|
|
|
|
|
|
| VRRP |
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00012232 | Firewall, | 2 | Some SIP phones may alter or periodically refresh the session information for a | Y | Y | Y | Y | Y | - | - | - | - | Y |
CR00012430 | SIP ALG |
| call, by sending a |
|
|
|
|
|
|
|
|
|
|
|
|
| a call was established between two SIP phones on the private side of the firewall |
|
|
|
|
|
|
|
|
|
|
|
|
| and one of the phones attempted to update the session information, the call |
|
|
|
|
|
|
|
|
|
|
|
|
| became corrupted. This meant that one of the callers stopped hearing the other. |
|
|
|
|
|
|
|
|
|
|
|
|
| This issue has been resolved. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CR00012233 | BOOTP | 2 | When the router or switch acted as a relay agent to process BOOTP requests that | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
|
|
| contained option 82, it modified the option 82 information of packets even |
|
|
|
|
|
|
|
|
|
|
|
|
| when their giaddr field was set to a |
|
|
|
|
|
|
|
|
|
|
|
|
| the policy specified by the command: |
|
|
|
|
|
|
|
|
|
|
set bootp relay option82 policy={dropkeepreplace}
This issue has been resolved. As required by RFC 3046, the router or switch now forwards client DHCP packets that have a
Version