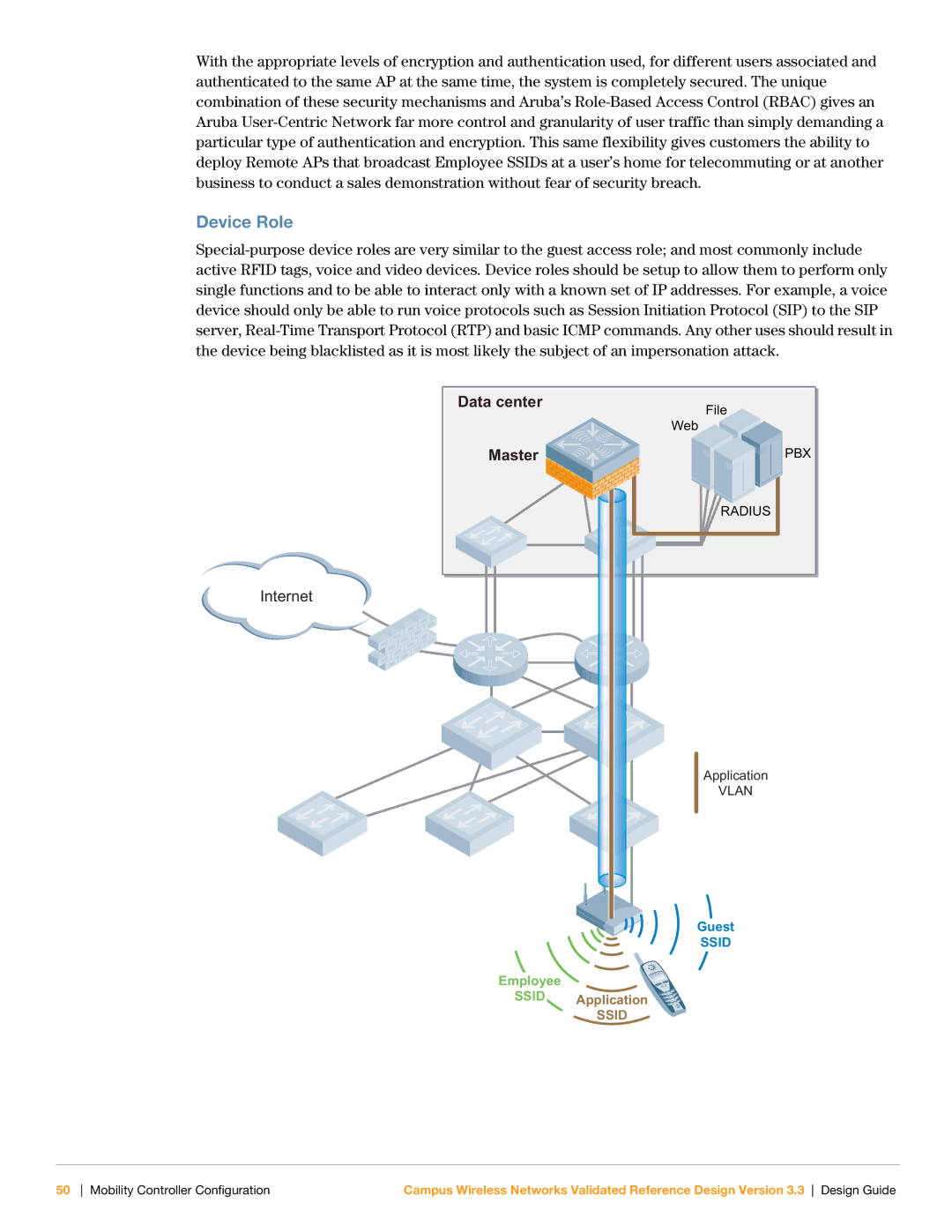
With the appropriate levels of encryption and authentication used, for different users associated and authenticated to the same AP at the same time, the system is completely secured. The unique combination of these security mechanisms and Aruba’s Role-Based Access Control (RBAC) gives an Aruba User-Centric Network far more control and granularity of user traffic than simply demanding a particular type of authentication and encryption. This same flexibility gives customers the ability to deploy Remote APs that broadcast Employee SSIDs at a user’s home for telecommuting or at another business to conduct a sales demonstration without fear of security breach.
Device Role
Special-purpose device roles are very similar to the guest access role; and most commonly include active RFID tags, voice and video devices. Device roles should be setup to allow them to perform only single functions and to be able to interact only with a known set of IP addresses. For example, a voice device should only be able to run voice protocols such as Session Initiation Protocol (SIP) to the SIP server, Real-Time Transport Protocol (RTP) and basic ICMP commands. Any other uses should result in the device being blacklisted as it is most likely the subject of an impersonation attack.
Data center | File |
|
| Web |
Master | PBX |
| RADIUS |
Internet
Application
VLAN
Guest
SSID
Employee | |
SSID | Application |
| SSID |
50 Mobility Controller Configuration | Campus Wireless Networks Validated Reference Design Version 3.3 Design Guide |