Chapter 2
Aruba’s User-Centric
Network Architecture
This chapter provides an overview of a centralized wireless LAN architecture, followed by a high level technical overview of the Aruba User-Centric Network components and network design.
This overview describes the technology, architecture, services, and applications that make up an Aruba User-Centric Network to help you make the right design choices, and select the appropriate solution components.
Understanding Centralized Wireless LAN Networks
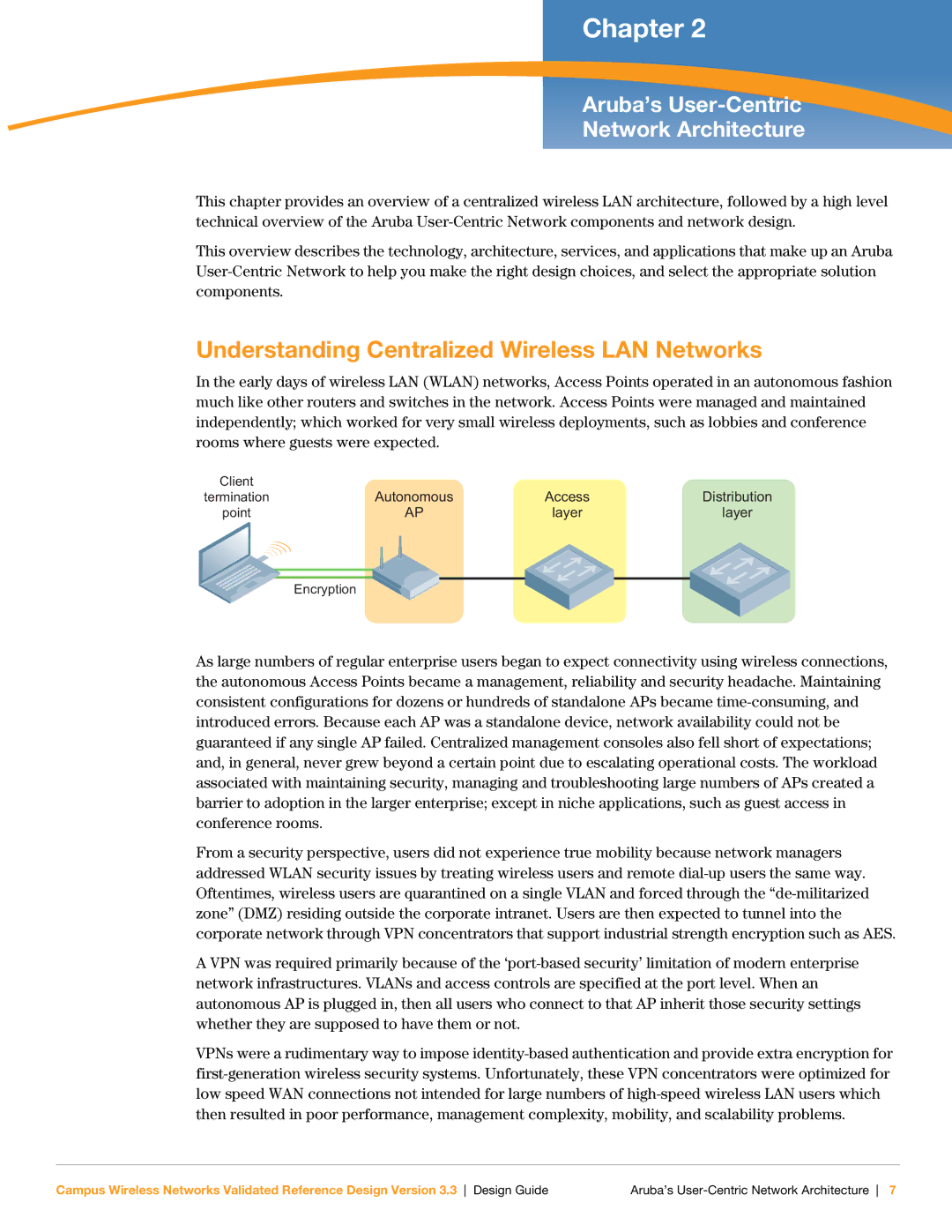
In the early days of wireless LAN (WLAN) networks, Access Points operated in an autonomous fashion much like other routers and switches in the network. Access Points were managed and maintained independently; which worked for very small wireless deployments, such as lobbies and conference rooms where guests were expected.
Client | Autonomous | Access | Distribution |
termination |
point | AP | layer | layer |
Encryption
As large numbers of regular enterprise users began to expect connectivity using wireless connections, the autonomous Access Points became a management, reliability and security headache. Maintaining consistent configurations for dozens or hundreds of standalone APs became time-consuming, and introduced errors. Because each AP was a standalone device, network availability could not be guaranteed if any single AP failed. Centralized management consoles also fell short of expectations; and, in general, never grew beyond a certain point due to escalating operational costs. The workload associated with maintaining security, managing and troubleshooting large numbers of APs created a barrier to adoption in the larger enterprise; except in niche applications, such as guest access in conference rooms.
From a security perspective, users did not experience true mobility because network managers addressed WLAN security issues by treating wireless users and remote dial-up users the same way. Oftentimes, wireless users are quarantined on a single VLAN and forced through the “de-militarized zone” (DMZ) residing outside the corporate intranet. Users are then expected to tunnel into the corporate network through VPN concentrators that support industrial strength encryption such as AES.
A VPN was required primarily because of the ‘port-based security’ limitation of modern enterprise network infrastructures. VLANs and access controls are specified at the port level. When an autonomous AP is plugged in, then all users who connect to that AP inherit those security settings whether they are supposed to have them or not.
VPNs were a rudimentary way to impose identity-based authentication and provide extra encryption for first-generation wireless security systems. Unfortunately, these VPN concentrators were optimized for low speed WAN connections not intended for large numbers of high-speed wireless LAN users which then resulted in poor performance, management complexity, mobility, and scalability problems.