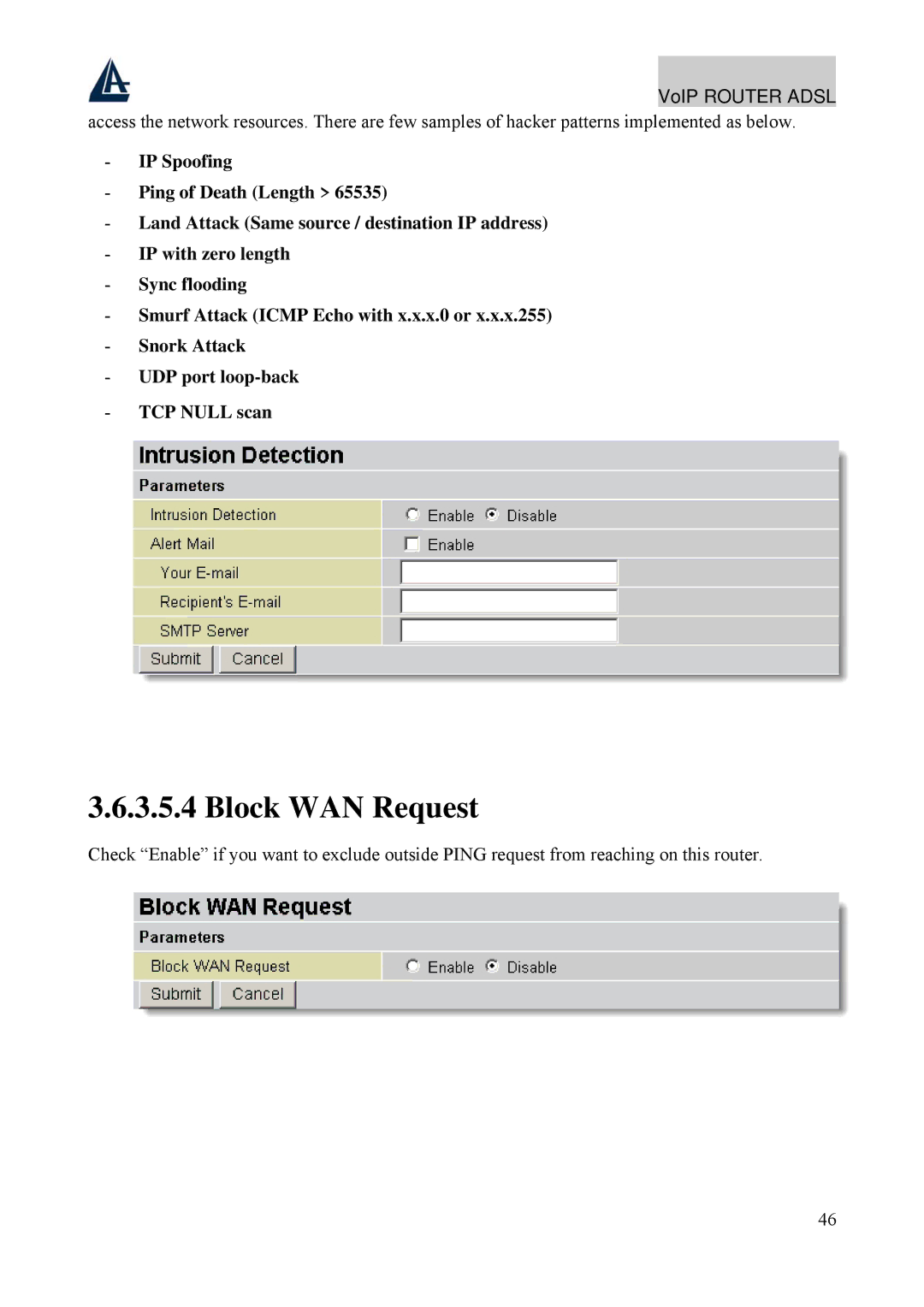
![]() VoIP ROUTER ADSL access the network resources. There are few samples of hacker patterns implemented as below.
VoIP ROUTER ADSL access the network resources. There are few samples of hacker patterns implemented as below.
-IP Spoofing
-Ping of Death (Length > 65535)
-Land Attack (Same source / destination IP address)
-IP with zero length
-Sync flooding
-Smurf Attack (ICMP Echo with x.x.x.0 or x.x.x.255)
-Snork Attack
-UDP port
-TCP NULL scan
3.6.3.5.4 Block WAN Request
Check “Enable” if you want to exclude outside PING request from reaching on this router.
46