Brocade ICX
Brocade Communications Systems, Incorporated
Contents
Brocade ICX 6650 Security Configuration Guide
Chapter
Brocade ICX 6650 Security Configuration Guide
Types of ACL-based rate limiting
ACL-based rate limiting overview
Ietf RFC support
Chapter 802.1X Port Security
MAC-based Vlan overview
MAC-based Vlan feature structure
MAC port security overview
Local and global resources used for MAC port security
Supported Radius attributes
How multi-device port authentication works
Radius authentication
Authentication-failure actions
Avoiding being a victim in a Smurf attack
Smurf attacks
Avoiding being an intermediary in a Smurf attack
Configuration notes and feature limitations for DAI
Configuration notes for port-based fixed rate limiting
Configuring a port-based fixed rate limiting policy
Displaying the port-based fixed rate limiting configuration
Viewing rate limits set on BUM traffic
Configuration notes and feature limitations
Configuring rate limiting for BUM traffic
Broadcast, unknown Unicast, and Multicast rate limiting
Page
Brocade ICX 6650 slot and port numbering
Audience
Supported hardware and software
Dhcp on
How this document is organized
Text formatting
Command syntax conventions
Document conventions
Corporation Referenced Trademarks and Products
Related publications
Other industry resources
Additional information
Getting technical help
Brocade resources
Document feedback
Feature Brocade ICX
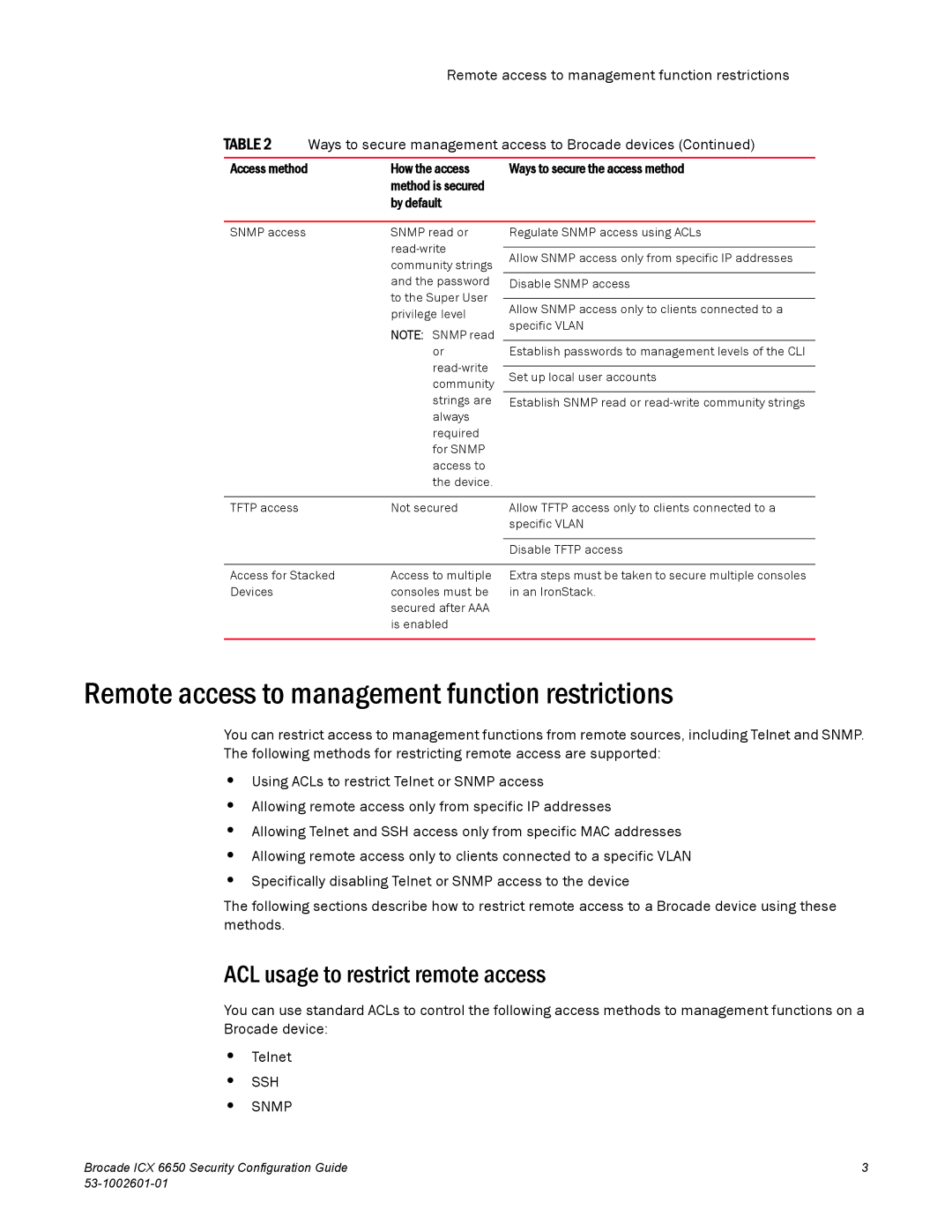
Securing access methods
Method is secured
ACL usage to restrict remote access
Remote access to management function restrictions
Syntax ssh access-group num
Using an ACL to restrict Telnet access
Using an ACL to restrict SSH access
Syntax telnet access-group num
Syntax snmp-server community string ro rw num
Using ACLs to restrict Snmp access
Defining the console idle time
Restricting SSH access to a specific IP address
Remote access restrictions
Restricting Telnet access to a specific IP address
Restricting SSH connection
Restricting access to the device based on IP or MAC address
Restricting Snmp access to a specific IP address
Restricting Telnet connection
Restricting Http and Https connection
Changing the login timeout period for Telnet sessions
Defining the Telnet idle time
Syntax no telnet login-retries number
Restricting Telnet access to a specific Vlan
Syntax no snmp-server enable vlan vlan-id
Restricting Snmp access to a specific Vlan
Restricting Tftp access to a specific Vlan
Syntax no telnet server enable vlan vlan-id
Syntax crypto key generate zeroize
Allowing SSHv2 access to the Brocade device
Syntax no default-gateway ip-addr metric
Device management security
Disabling Snmp access
Disabling specific access methods
Allowing Snmp access to the Brocade device
Disabling Telnet access
Syntax no enable telnet password string
Passwords used to secure access
Setting a Telnet password
Syntax no tftp disable
Syntax no telnet server suppress-reject-message
Setting passwords for management privilege levels
Passwords used to secure access
Augmenting management privilege levels
Syntax enable read-only-password text
After the console prompt reappears, assign a new password
Recovering from a lost password
Specifying a minimum password length
Enter boot system flash primary at the prompt
Number-of-characterscan be from
Enhancements to username and password
Syntax enable password-min-length number-of-characters
Local user accounts
Syntax no enable strict-password-enforcement
Enabling enhanced user password combination requirements
Syntax no enable user password-masking
Enabling user password masking
Enabling user password aging
Syntax username name password Enter
Syntax no enable user password-history 1
Configuring password history
Enhanced login lockout
Syntax no enable user password-aging
Requirement to accept the message of the day
Local user account configuration
Setting passwords to expire
Syntax username name enable
Local user accounts with unencrypted passwords
Local user accounts with no passwords
Syntax show users
Creating a password option
Local accounts with encrypted passwords
Using the username user-stringcreate-password command
How TACACS+ differs from Tacacs
Changing a local user password
Syntax no username user-stringpassword password-string
Tacacs and TACACS+ security
TACACS/TACACS+ authentication, authorization, and accounting
Kill console Syntax kill console all unit
TACACS+ authentication
Tacacs authentication
TACACS+ accounting
TACACS+ authorization
User action Applicable AAA operations
AAA security for commands pasted into the running-config
AAA operations for TACACS/TACACS+
Configuring TACACS+
TACACS/TACACS+ configuration considerations
Configuring Tacacs
Identifying the TACACS/TACACS+ servers
Enabling Tacacs
Specifying different servers for individual AAA functions
Setting optional Tacacs and TACACS+ parameters
Setting the timeout parameter
Setting the TACACS+ key
Setting the retransmission limit
Method parameter Description
Syntax no aaa authentication enable implicit-user
Entering privileged Exec mode after a Telnet or SSH login
Syntax aaa authentication login privilege-mode
Configuring an Attribute-Value pair on the TACACS+ server
Configuring TACACS+ authorization
Configuring Exec authorization
Syntax aaa authorization exec default tacacs+ none
Foundry-privlvl =
AAA support for console commands
Configuring command authorization
Syntax no enable aaa console
TACACS+ accounting configuration
Configuring TACACS+ accounting for Telnet/SSH Shell access
Configuring TACACS+ accounting for CLI commands
Configuring TACACS+ accounting for system events
Radius security
Radius authentication, authorization, and accounting
Radius authentication
Output of the show aaa command for TACACS/TACACS+
Radius accounting
Radius authorization
AAA operations for Radius
AAA operations for Radius
Radius security AAA operations for Radius
Radius configuration considerations
Brocade-specific attributes on the Radius server
Configuring Radius
Attribute ID Data type Description
Port Configuration level Allows
Attribute name Attribute ID Data type Description
Enabling Snmp to configure Radius
Identifying the Radius server to the Brocade device
Radius server per port
Radius server per port configuration notes
Radius configuration example and command syntax
Following shows an example configuration
Host ip-addris an IPv4 address
Radius server-to-ports configuration notes
Radius server to individual ports mapping
Syntax use-radius-server ip-addr
Syntax radius-server retransmit number
Setting the Radius key
Radius parameters
Syntax radius-server key 0 1 string
Syntax radius-server host ipv6 ipv6-host address
Setting authentication-method lists for Radius
Setting Radius over IPv6
Syntax radius-server timeout number
Setting passwords for management privilege levels on
Syntax aaa authorization exec default radius none
Radius authorization
Command authorization and accounting for console commands
Radius accounting
Configuring Radius accounting for Telnet/SSH Shell access
Configuring Radius accounting for CLI commands
Configuring Radius accounting for system events
Displaying Radius configuration information
Output of the show aaa command for Radius
Authentication-method lists
Authentication-method lists
Examples of authentication-method lists
Example
Command Syntax
Following is the command syntax for the preceding examples
TCP Flags edge port security
User account configuration on
TCP Flags edge port security
Using TCP Flags in combination with other ACL features
TCP Flags edge port security
SSH version 2 overview
SSH2 and SCP
Key exchange methods are diffie-hellman-group1-sha1
SSH2 supported features
SSH2 unsupported features
Tested SSH2 clients
Configure DSA or RSA challenge-response authentication
SSH2 authentication types
Configuring SSH2
SSH2 authentication types
Generating and deleting an RSA key pair
Setting the CPU priority for key generation
Generating and deleting a DSA key pair
Syntax crypto key zeroize
Configuring DSA or RSA challenge-response authentication
Deleting DSA and RSA key pairs
Providing the public key to clients
Begin SSH2 Public KEY
Importing authorized public keys into the Brocade device
Syntax clear public-key
Enabling DSA or RSA challenge-response authentication
Syntax ip ssh key-authentication yes no
Optional SSH parameters
Syntax ip ssh password-authentication no yes
Setting the number of SSH authentication retries
Deactivating user authentication
Syntax ip ssh authentication-retries number
Configuring the maximum idle time for SSH sessions
Enabling empty password logins
Setting the SSH port number
Setting the SSH login timeout value
Displaying SSH connection information
Filtering SSH access using ACLs
Terminating an active SSH connection
Displaying SSH information
SSH connection information
Displaying SSH configuration information
Syntax show ip ssh config
Displaying SSH information
Displaying additional SSH connection information
Displaying SSH information SSH configuration information
Secure copy with SSH2
Secure copy configuration notes
Example file transfers using SCP
Copying a file to the running configuration
Copying a software image file from flash memory
Copying a file to the startup configuration
To overwrite the running configuration file
Copying a software image file to flash memory
Importing a DSA or RSA public key
Importing a digital certificate using SCP
Importing an RSA private key
Enabling SSH2 client
Configuring SSH2 client public key authentication
SSH2 client
Exporting client public keys
Using SSH2 client
Generating and deleting a client DSA key pair
Generating and deleting a client RSA key pair
Displaying SSH2 client information
Rule-Based IP ACLs
Supported ACL features on outbound traffic
ACL overview
ACL overview Supported ACL features on outbound traffic
ACL overview Virtual routing interfaces
Types of IP ACLs
ACL IDs and entries
Numbered and named ACLs
Hardware aging of Layer 4 CAM entries
Default ACL action
How hardware-based ACLs work
How fragmented packets are processed
ACL configuration considerations
Standard numbered ACL syntax
Configuring standard numbered ACLs
Configuration example for standard numbered ACLs
Standard named ACL configuration
Standard named ACL syntax
Syntax no ip access-list standard ACL-nameACL-num
Brocade ICX 6650 Security Configuration Guide 53-1002601-01
Extended numbered ACL configuration
Extended numbered ACL configuration
Configuration example for standard named ACLs
Extended numbered ACL syntax
Num
Brocade ICX 6650 Security Configuration Guide 53-1002601-01
Brocade ICX 6650 Security Configuration Guide
Here is another example of an extended ACL
Configuration examples for extended numbered ACLs
Extended named ACL configuration
Extended named ACL configuration
Extended named ACL syntax
Num
Brocade ICX 6650 Security Configuration Guide 53-1002601-01
Page
Syntax ip preserve-ACL-user-input-format
Syntax enable egress-acl-on-cpu-traffic
Applying egress ACLs to Control CPU traffic
Preserving user input for ACL TCP/UDP port numbers
Adding a comment to an entry in a numbered ACL
ACL comment text management
Viewing comments in an ACL
Show running-config Show access-list Show ip access-list
Adding a comment to an entry in a named ACL
Deleting a comment from an ACL entry
Syntax show running-config
ACL logging
Configuration notes for ACL logging
ACL logging
Example ACL logging configuration
Configuration tasks for ACL logging
Syntax ACL-logging
Syntax logging-enable
Displaying ACL Log Entries
Syntax show log
Syntax no ip access-group frag deny
Enter the no form of the command to disable this feature
Configuration notes for ACL filtering
Syntax no enable ACL-per-port-per-vlan
Syntax per-vlan Vlan ID Syntax no ip access-group ACL ID
ACLs to filter ARP packets
Syntax no ip access-group ACL ID in ethernet port to port
ACLs to filter ARP packets
Configuration considerations for filtering ARP packets
Configuring ACLs for ARP filtering
Syntax no ip use-ACL-on-arp access-list-number
Syntax show ACL-on-arp ethernet port loopback num ve num
Filtering on IP precedence and ToS values
Displaying ACL filters for ARP
Clearing the filter count
TCP flags edge port security
QoS options for IP ACLs
Syntax ...dscp-marking dscp-value
Configuration notes for QoS options on Brocade ICX
Using an IP ACL to mark Dscp values Dscp marking
For IP
Combined ACL for 802.1p marking
QoS options for IP ACLs
Syntax ...dscp-matching 0
Using an ACL to change the forwarding queue
ACL-based rate limiting
Dscp matching
Enabling and viewing hardware usage statistics for an ACL
ACLs to control multicast features
ACL statistics
Policy Based Routing
Troubleshooting ACLs
Syntax show access-list ACL-numACL-nameall
Displaying ACL information
Configuring a PBR policy
Configuration considerations for policy-based routing
Configuring the ACLs
Syntax noroute-map map-namepermit deny num
Configuring the route map
Enabling PBR
Policy Based Routing
Configuration examples for PBR
Setting the next hop
Basic example of PBR
Setting the output interface to the null interface
Trunk formation with PBR policy
IPv6 ACL overview
Feature
IPv6 protocol names and numbers
IPv6 ACL configuration notes
IPv6 ACL traffic filtering criteria
Example IPv6 configurations
Configuring an IPv6 ACL
Here is another example
Configuring an IPv6 ACL
Show ipv6 access-listcommand displays the following
Default and implicit IPv6 ACL action
Ipv6-operator dscp
Syntax no ipv6 access-list ACL-name
Creating an IPv6 ACL
Syntax for creating an IPv6 ACL
For UDP
For Icmp
For TCP
Ipv6-source-prefix /prefix-length
IPv6 ACL arguments Description
IPv6 ACL arguments Description
Creating an IPv6 ACL Syntax descriptions
802.1p-priority-matching number
Icmp message configurations
Applying an IPv6 ACL to an interface
Syntax ipv6 enable
Syntax .ipv6 traffic-filter ipv6-ACL-namein
Adding a comment to an IPv6 ACL entry
Syntax for applying an IPv6 ACL
Applying an IPv6 ACL to a trunk group
Displaying IPv6 ACLs
Deleting a comment from an IPv6 ACL entry
Support for ACL logging
Displaying IPv6 ACLs
Syntax show ipv6 access-list
Syntax show ipv6 access-list access-list-name
Types of ACL-based rate limiting
ACL-based rate limiting overview
ACL statistics
Traffic policies overview
Traffic policy structure
Configuration notes for traffic policies
Configuring fixed rate limiting
Configuring adaptive rate limiting
Configuring adaptive rate limiting
Parameter Definition
ACL based adaptive rate limiting parameters
Page
Dropping packets
Handling packets that exceed the rate limit
Permitting packets at low priority
Enabling and using ACL statistics
Enabling ACL statistics
Enabling and using ACL statistics
Viewing ACL and rate limit counters
Enabling ACL statistics with rate limiting traffic policies
General Counters
Clearing ACL and rate limit counters
ACL and rate limit counting statistics
Parameter Description
ParameterDescription
Viewing traffic policies
Syntax show traffic-policy TPD-name
Ietf RFC support
802.1X Port Security
How 802.1X port security works
Device roles in an 802.1X configuration
How 802.1X port security works
Controlled and uncontrolled ports
Communication between the devices
PAE
Message exchange during authentication
Refer to EAP pass-through support on
Setting the IP MTU size
Syntax no ip mtu num
Authenticating multiple hosts connected to the same port
Configuration notes for setting the IP MTU size
EAP pass-through support
Multiple hosts connected to a single 802.1X-enabled port
How 802.1X multiple-host authentication works
Configuration notes for 802.1x multiple-host authentication
802.1X port security and sFlow
Configure the device interaction with Clients
802.1X port security configuration
802.1X port security configuration
Configure the device role as the Authenticator
Supported Radius attributes
Configuring an authentication method list for
Setting Radius parameters
Syntax no aaa authentication dot1x default method-list
Syntax no dot1x auth-timeout-action success
Specifying the Radius timeout action
Permit user access to the network after a Radius timeout
Deny user access to the network after a Radius timeout
Dynamic Vlan assignment for 802.1X port configuration
Re-authenticate a user
Syntax no dot1x re-auth-timeout- success seconds
Type Value
Dynamic multiple Vlan assignment for 802.1X ports
Syntax save-dynamicvlan-to-config
Saving dynamic Vlan assignments to the running-config file
802.1X port security configuration
Disabling strict security mode globally
Disabled strict security mode
Syntax no global-filter-strict-security
Syntax no dot1x disable-filter-strict-security
ACL or MAC address filter configured on the Brocade device
Dynamically applying existing ACLs or MAC address filters
Value Description
Configuring per-user IP ACLs or MAC address filters
Enabling 802.1X port security
Setting the port control
Syntax no timeout re-authperiod seconds
Configuring periodic re-authentication
Syntax no re-authentication
Syntax dot1x re-authenticate ethernet port
Re-authenticating a port manually
Setting the quiet period
Setting the wait interval for EAP frame retransmissions
Syntax auth-max value
Setting the maximum number of EAP frame retransmissions
Syntax no timeout tx-period seconds
Value is a number from 1-10. The default is
Syntax maxreq value
Syntax supptimeout seconds
Syntax servertimeout seconds
Initializing 802.1X on a port
Syntax no auth-fail-action restricted-vlan
Allowing access to multiple hosts
Configuring 802.1X multiple-host authentication
Specifying the authentication-failure action
Syntax no mac-session-aging no-aging permitted-mac-only
This command enables aging of permitted sessions
Syntax no auth-fail-max-attempts attempts
Disabling aging for dot1x-mac-sessions
Syntax clear dot1x mac-session mac-address
Specifying the aging time for blocked clients
Syntax no mac-age-time seconds
Moving native Vlan mac-sesions to restrict Vlan
MAC address filters for EAP frames
802.1X accounting configuration
Configuring Vlan access for non-EAP-capable clients
Syntax timeout restrict-fwd-period num
Enabling 802.1X accounting
To enable 802.1X accounting, enter the following command
Syntax aaa accounting dot1x default start-stop radius none
802.1X accounting attributes for Radius
Syntax show dot1x
Displaying 802.1X configuration information
Output from the show dot1x command
Displaying 802.1X information
Syntax show dot1x config ethernet port
Forceunauth
Field Statistics
Displaying 802.1X statistics
Displaying 802.1X information
Syntax show dot1x statistics ethernet port
Syntax clear dot1x statistics ethernet port
Clearing 802.1X statistics
Displaying dynamically assigned Vlan information
Syntax clear dot1x statistics all
Syntax show dot1x ip-ACL
Displaying user-defined MAC address filters and IP ACLs
Syntax show dot1x mac-address-filter
Syntax show dot1x ip-ACL all ethernet port
Displaying the status of strict security mode
Syntax show dot1x mac-address-filter all ethernet port
Global-filter-strict-security Enable
Displaying 802.1X multiple-host authentication information
Mac Session max-age Seconds
Displaying 802.1X multiple-host configuration information
Pvid
Syntax show dot1x mac-session
Syntax show dot1x mac-session brief
Output from the show dot1x mac-session brief command
Sample 802.1X configurations
Sample 802.1X configurations
Point-to-point configuration
Same point-to-point 802.1x configuration
Sample 802.1x configuration using a hub
Hub configuration
802.1X authentication with dynamic Vlan assignment
Auth-fail-vlanid
Page
MAC Port Security
Local and global resources used for MAC port security
MAC port security overview
Syntax port security Syntax no enable
MAC port security configuration
Enabling the MAC port security feature
Syntax no age minutes
Setting the port security age timer
MAC port security configuration
On a tagged interface
Specifying secure MAC addresses
On an untagged interface
Syntax violation restrict age
Dropping packets from a violating address
Syntax violation restrict
Disabling the port for a specified amount of time
Clearing port security statistics
Clearing restricted MAC addresses
Clearing violation statistics
Displaying the secure MAC addresses
Displaying port security settings
Displaying port security information
Syntax show port security statistics port
Output from the show port security mac command
Output from the show port security statistics port command
Displaying port security statistics
Syntax show port security ethernet port restricted-macs
Displaying restricted MAC addresses on a port
Syntax show port security statistics module
Static and dynamic hosts
MAC-based Vlan overview
MAC-based Vlan and port up or down events
MAC-based Vlan feature structure
Source MAC address authentication
Policy-based classification and forwarding
Description CLI level
Dynamic MAC-based Vlan CLI commands
Dynamic MAC-based Vlan
Dynamic MAC-based Vlan
CLI command Description CLI level
Dynamic MAC-based Vlan configuration example
Dynamic MAC-based Vlan CLI commands for MAC-based VLANs
Following example shows a MAC-based Vlan configuration
MAC-based Vlan configuration
MAC-based Vlan configuration
Attribute ID Data type Optional or Description Mandatory
Using MAC-based VLANs and 802.1X security on the same port
Aging process for MAC-based Vlan works as described below
Aging for MAC-based Vlan
For permitted hosts
For blocked hosts
Globally disabling aging
Disabling aging for MAC-based Vlan sessions
For MAC-based dynamic activation
To change the length of the software aging period
Disabling the aging on interfaces
Configuring the maximum MAC addresses per port
Configuring a MAC-based Vlan for a static host
Syntax no mac-authentication disable-aging
Syntax mac-vlan-permit ethernet stack-unit/slotnum/portnum
Configuring MAC-based Vlan for a dynamic host
Configuring dynamic MAC-based Vlan
Displaying the MAC-VLAN table
Configuring MAC-based VLANs using Snmp
Enter the following command to display the MAC-VLAN table
Displaying information about MAC-based VLANs
Syntax show table-mac-vlan mac-address
Displaying the MAC-VLAN table for a specific MAC address
Displaying allowed MAC addresses
Displaying information about MAC-based VLANs
Syntax show table-mac-vlan denied-mac
Displaying denied MAC addresses
Displaying detailed MAC-VLAN data
Default
Displaying MAC-VLAN information for a specific interface
Vlan
Displaying MAC addresses in a MAC-based Vlan
Clearing MAC-VLAN information
Clearing MAC-VLAN information
Sample MAC-based Vlan application
Displaying MAC-based Vlan logging
Sample MAC-based Vlan application
Sample MAC-based Vlan configuration
0000.0075.3f73 1/1/1
Sample MAC-based Vlan application
How multi-device port authentication works
Multi-Device Port Authentication
Supported Radius attributes
Radius authentication
Authentication-failure actions
Support for dynamic ARP inspection with dynamic ACLs
Support for dynamic Vlan assignment
Support for dynamic ACLs
Support for source guard protection
Support for Dhcp snooping with dynamic ACLs
Configuring Brocade-specific attributes on Radius server
Multi-device port authentication configuration
Syntax no mac-authentication enable
Enabling multi-device port authentication
Globally enabling multi-device port authentication
Enabling multi-device port authentication on an interface
Syntax no mac-authentication auth-fail-vlan-id vlan-id
Specifying the authentication-failure action
Multi-device port authentication configuration
Defining MAC address filters
Generating traps for multi-device port authentication
Configuring dynamic Vlan assignment
Syntax no mac-authentication no-override-restrict-vlan
Syntax no mac-authentication enable-dynamic-vlan
Vlan-namestring
Syntax mac-authentication disable-ingress-filtering
Configuration notes and limitations
Syntax no mac-authentication save-dynamicvlan-to-config
Dynamically applying IP ACLs to authenticated MAC addresses
Page
ACLs configured on the Brocade device
Enabling denial of service attack protection
Configuring the Radius server to support dynamic IP ACLs
Enabling source guard protection
Syntax no mac-authentication dos-protection mac-limit number
Syntax clear auth-mac-table
Clearing authenticated MAC addresses
Syntax no mac-authentication source-guard-protection enable
Enter the no form of the command to disable SG protection
Syntax clear auth-mac-table ethernet port
Disabling aging for authenticated MAC addresses
Syntax mac-authentication clear-mac-session mac-address
Globally disabling aging of MAC addresses
Disabling the aging of MAC addresses on interfaces
Syntax no mac-authentication hw-deny-age num
Specifying the aging time for blocked MAC addresses
Specifying the Radius timeout action
Permit user access to the network after a Radius timeout
Syntax no mac-authentication auth-timeout-action success
Syntax no mac-authentication auth-timeout-action failure
Multi-device port authentication password override
Deny user access to the network after a Radius timeout
Syntax no mac-authentication password-override password
Displaying multi-device port authentication information
Limiting the number of authenticated MAC addresses
Displaying authenticated MAC address information
Syntax show auth-mac-address configuration
Output from the show authenticated-mac-address command
Syntax show auth-mac-address mac-addressip-addrport
Syntax show auth-mac-addresses authorized-mac
Displaying the authenticated MAC addresses
Syntax show auth-mac-address ethernet port
Displaying the non-authenticated MAC addresses
Syntax show auth-mac-addresses unauthorized-mac
Explains the information in the output
Syntax show auth-mac-address detail ethernet port
YES
Output from the show auth-mac-addresses detailed command
Pvid
Example port authentication configurations
Interface ethernet 1 dual-modemac-authentication enable
Example port authentication configurations
Port e1/1/1 Dual Mode
Example port authentication configurations
Radius Server User 0000.008e.86ac IP Phone Profile
No Profile for MAC 0000.007f.2e0a PC User 1 Profile
Syntax no mac-authentication auth-fail-dot1x-override
How a Smurf attack floods a victim with Icmp replies
Smurf attacks
Syntax no ip directed-broadcast
Avoiding being an intermediary in a Smurf attack
Avoiding being a victim in a Smurf attack
TCP SYN attacks
TCP SYN attacks
TCP security enhancement
Protecting against a blind injection attack
Syntax clear statistics dos-attack
Syntax show statistics dos-attack
Port-based rate limiting
Rate Limiting and Rate Shaping
Rate limiting in hardware
How port-based fixed rate limiting works
Syntax no rate-limit input fixed average-rate
Configuration notes for port-based fixed rate limiting
Configuring a port-based fixed rate limiting policy
Displaying the port-based fixed rate limiting configuration
Rate shaping
Configuration notes for rate shaping
Configuring outbound rate shaping for a port
Rate shaping
CPU rate-limiting
Configuring outbound rate shaping for a specific priority
Configuring outbound rate shaping for a trunk port
Displaying rate shaping configurations
ARP
Packet type Rate limit
ARP poisoning
Dynamic ARP inspection
ARP entries
Dynamic ARP Inspection
281
Syntax no arp ip-addrmac-addrinspection
Dynamic ARP inspection configuration
Configuring an inspection ARP entry
Enabling DAI on a Vlan
Enabling trust on a port
Dhcp snooping
Displaying ARP inspection status and ports
Displaying the ARP table
Dhcp binding database
How Dhcp snooping works
Page
Syntax no ip dhcp snooping vlan vlan-number
Syntax no dhcp snooping client-learning disable
Enabling Dhcp snooping on a Vlan
Disabling the learning of Dhcp clients on a port
Displaying Dhcp binding entry and status
Clearing the Dhcp binding database
Displaying Dhcp snooping status and ports
Displaying the Dhcp snooping binding database
Dhcp relay agent information
Dhcp snooping configuration example
Dhcp relay agent information
Dhcp option 82 sub-options
Configuration notes for Dhcp option
Sub-option 6 Subscriber ID
Sub-option 1 Circuit ID
Sub-option 2 Remote ID
Syntax no dhcp snooping relay information
Dhcp option 82 configuration
Syntax ip dhcp relay information policy policy-type
Changing the forwarding policy
Enabling and disabling subscriber ID processing
Viewing the circuit ID, remote ID, and forwarding policy
Viewing the ports on which Dhcp option 82 is disabled
Output for the ip dhcp relay information command
Viewing information about Dhcp option 82 processing
Syntax show interfaces ethernet port
IP source guard
Viewing the status of Dhcp option 82 and the subscriber ID
Page
For ip-addr, enter a valid IP address
No source-guard enable
Defining static IP source bindings
Displaying learned IP addresses
Syntax no source-guard enable
Enabling IP source guard per-port-per-VLAN
Enabling IP source guard on a VE
IP source guard
Broadcast, unknown Unicast, and Multicast rate limiting
Configuration notes and feature limitations
Configuring rate limiting for BUM traffic
Viewing rate limits set on BUM traffic
Syntax show rate-limit broadcast
Syntax show run interface
Broadcast, unknown Unicast, and Multicast rate limiting
Index
ARP
Radius
Page
Page
MAC-VLAN
Page
SSH
Vlan
Ip access-group,110 mac-vlan-permit,220 source-guard enable