Chapter 4 Configuring the ISA and ISM
Creating Crypto Maps
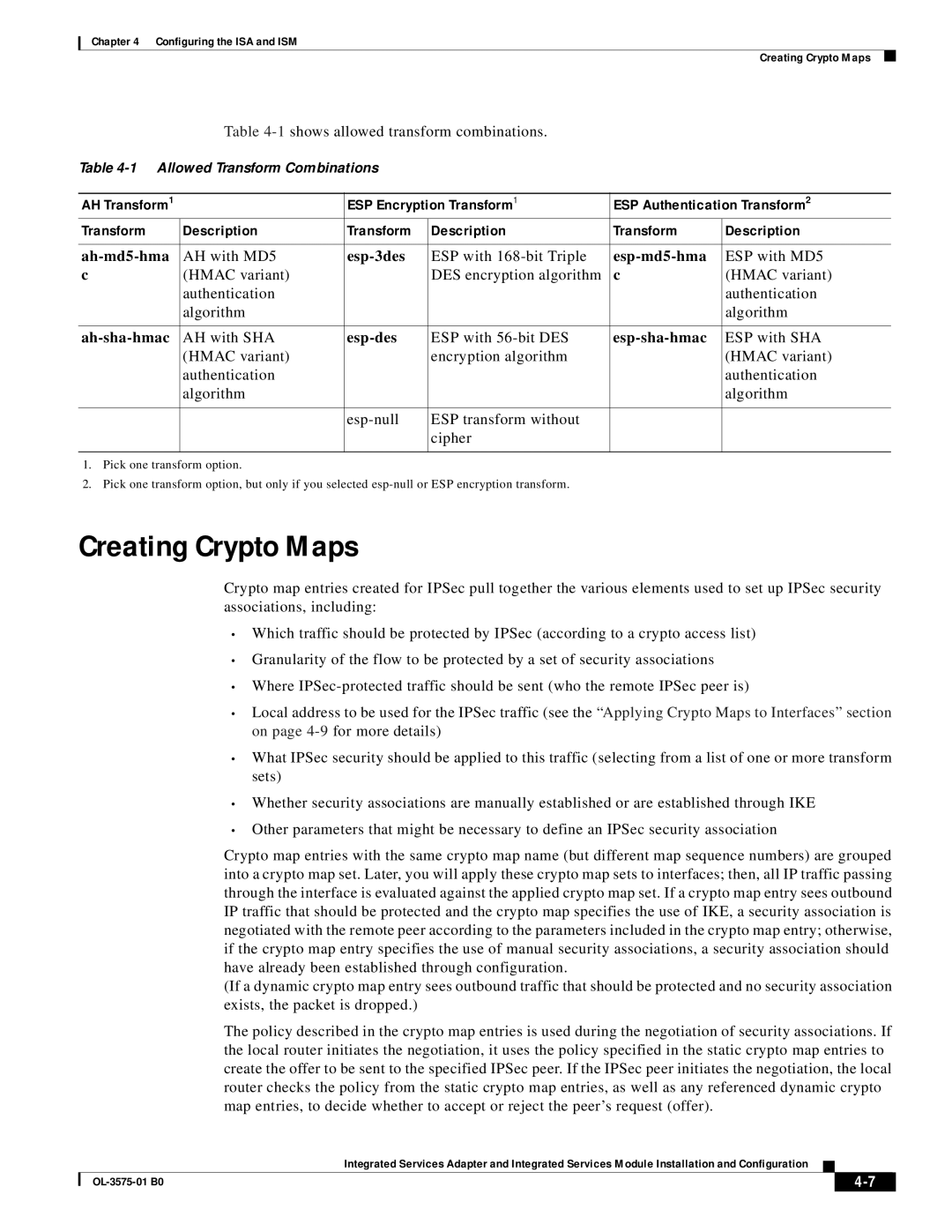
Table
Table
AH Transform1 |
| ESP Encryption Transform1 | ESP Authentication Transform2 | ||
Transform | Description | Transform | Description | Transform | Description |
|
|
|
|
|
|
AH with MD5 | ESP with | ESP with MD5 | |||
c | (HMAC variant) |
| DES encryption algorithm | c | (HMAC variant) |
| authentication |
|
|
| authentication |
| algorithm |
|
|
| algorithm |
|
|
|
|
|
|
AH with SHA | ESP with |
| ESP with SHA | ||
| (HMAC variant) |
| encryption algorithm |
| (HMAC variant) |
| authentication |
|
|
| authentication |
| algorithm |
|
|
| algorithm |
|
|
|
|
|
|
|
| ESP transform without |
|
| |
|
|
| cipher |
|
|
|
|
|
|
|
|
1.Pick one transform option.
2.Pick one transform option, but only if you selected
Creating Crypto Maps
Crypto map entries created for IPSec pull together the various elements used to set up IPSec security associations, including:
•Which traffic should be protected by IPSec (according to a crypto access list)
•Granularity of the flow to be protected by a set of security associations
•Where
•Local address to be used for the IPSec traffic (see the “Applying Crypto Maps to Interfaces” section on page
•What IPSec security should be applied to this traffic (selecting from a list of one or more transform sets)
•Whether security associations are manually established or are established through IKE
•Other parameters that might be necessary to define an IPSec security association
Crypto map entries with the same crypto map name (but different map sequence numbers) are grouped into a crypto map set. Later, you will apply these crypto map sets to interfaces; then, all IP traffic passing through the interface is evaluated against the applied crypto map set. If a crypto map entry sees outbound IP traffic that should be protected and the crypto map specifies the use of IKE, a security association is negotiated with the remote peer according to the parameters included in the crypto map entry; otherwise, if the crypto map entry specifies the use of manual security associations, a security association should have already been established through configuration.
(If a dynamic crypto map entry sees outbound traffic that should be protected and no security association exists, the packet is dropped.)
The policy described in the crypto map entries is used during the negotiation of security associations. If the local router initiates the negotiation, it uses the policy specified in the static crypto map entries to create the offer to be sent to the specified IPSec peer. If the IPSec peer initiates the negotiation, the local router checks the policy from the static crypto map entries, as well as any referenced dynamic crypto map entries, to decide whether to accept or reject the peer’s request (offer).
Integrated Services Adapter and Integrated Services Module Installation and Configuration
|
| ||
|
|