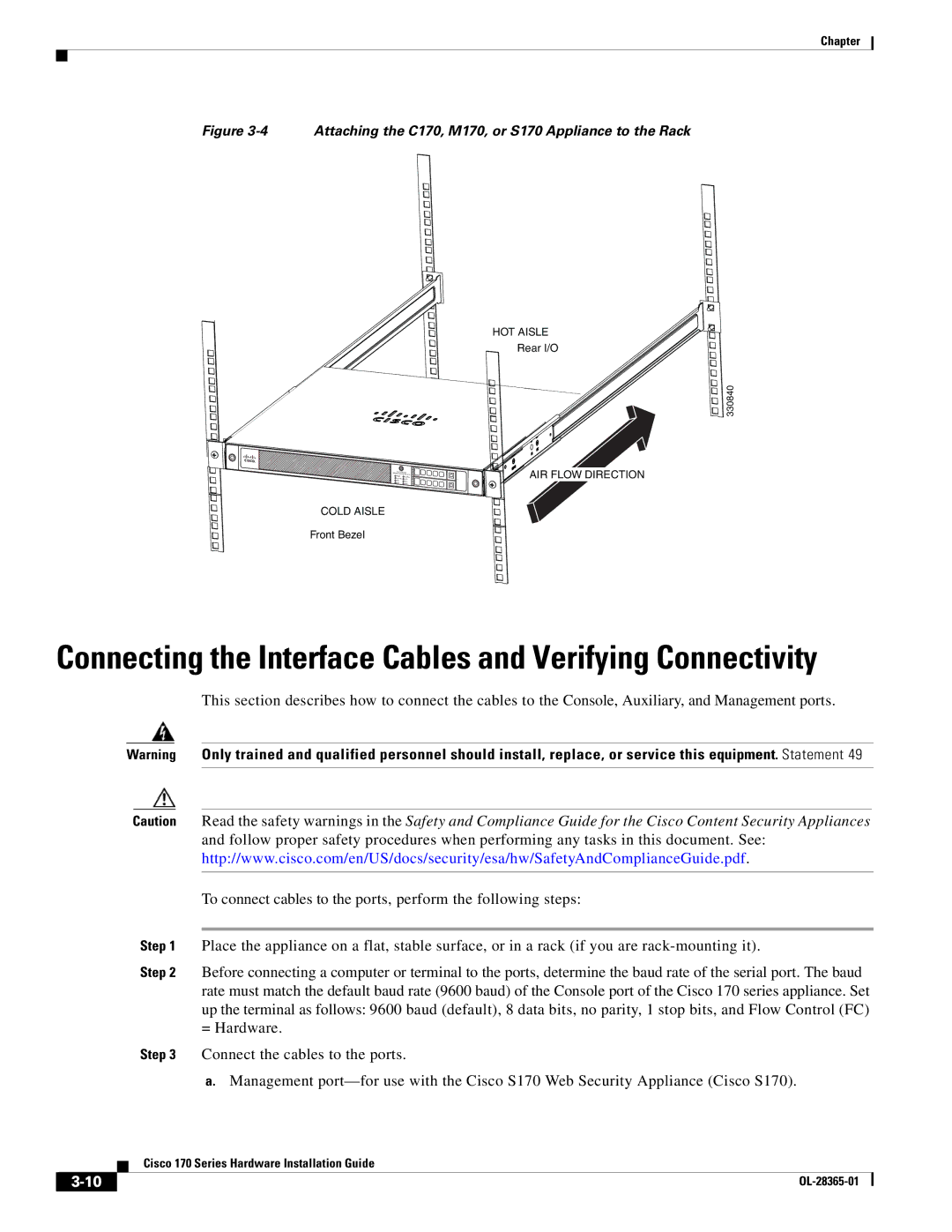
WSAS170K9, WSA S170 specifications
Cisco Systems WSA S170, also known as WSAS170K9, is a next-generation web security appliance designed to safeguard organizations from web-based threats while ensuring secure and policy-compliant internet access. This device brings advanced features, robust technologies, and vital characteristics to help organizations protect their digital assets.One of the key features of the WSA S170 is its real-time threat intelligence capabilities. Cisco's cloud-based security ecosystem provides continuous updates on emerging threats, ensuring that the appliance can effectively block malicious sites and protect users from phishing attacks. This proactive approach significantly enhances the organization's security posture.
The WSA S170 also excels in its content filtering capabilities. It allows IT administrators to set and enforce web access policies, ensuring that employees access only appropriate content. With customizable policies, organizations can minimize distractions, boost productivity, and comply with regulatory requirements.
Another essential aspect of the WSAS170K9 is its advanced malware protection. The appliance integrates with Cisco’s advanced threat protection tools to detect and remediate malware before it can inflict damage. This multi-layered defense strategy is crucial for maintaining a secure network environment.
Performance-wise, the Cisco WSA S170 is built to handle high traffic loads efficiently. With advanced caching technology, it reduces latency and improves bandwidth utilization, ensuring that users experience fast and uninterrupted internet access. This performance capability is critical for organizations that rely on web-based applications for their day-to-day operations.
In terms of ease of management, the WSAS170K9 features a web-based graphical user interface that simplifies configuration and monitoring. This intuitive interface enables IT teams to quickly analyze data, generate reports, and respond to security incidents efficiently.
Scalability is another significant characteristic of the Cisco WSA S170. As organizations grow, they can easily scale their web security solutions without a complete overhaul by integrating additional Cisco security products. This flexibility allows businesses to adapt to changing needs without compromising security.
In conclusion, the Cisco Systems WSA S170 (WSAS170K9) is a powerful web security appliance offering advanced features, real-time threat intelligence, effective content filtering, robust malware protection, high performance, user-friendly management, and scalability. These characteristics make it a vital tool for any organization looking to enhance its web security and ensure a safe browsing experience for its users.