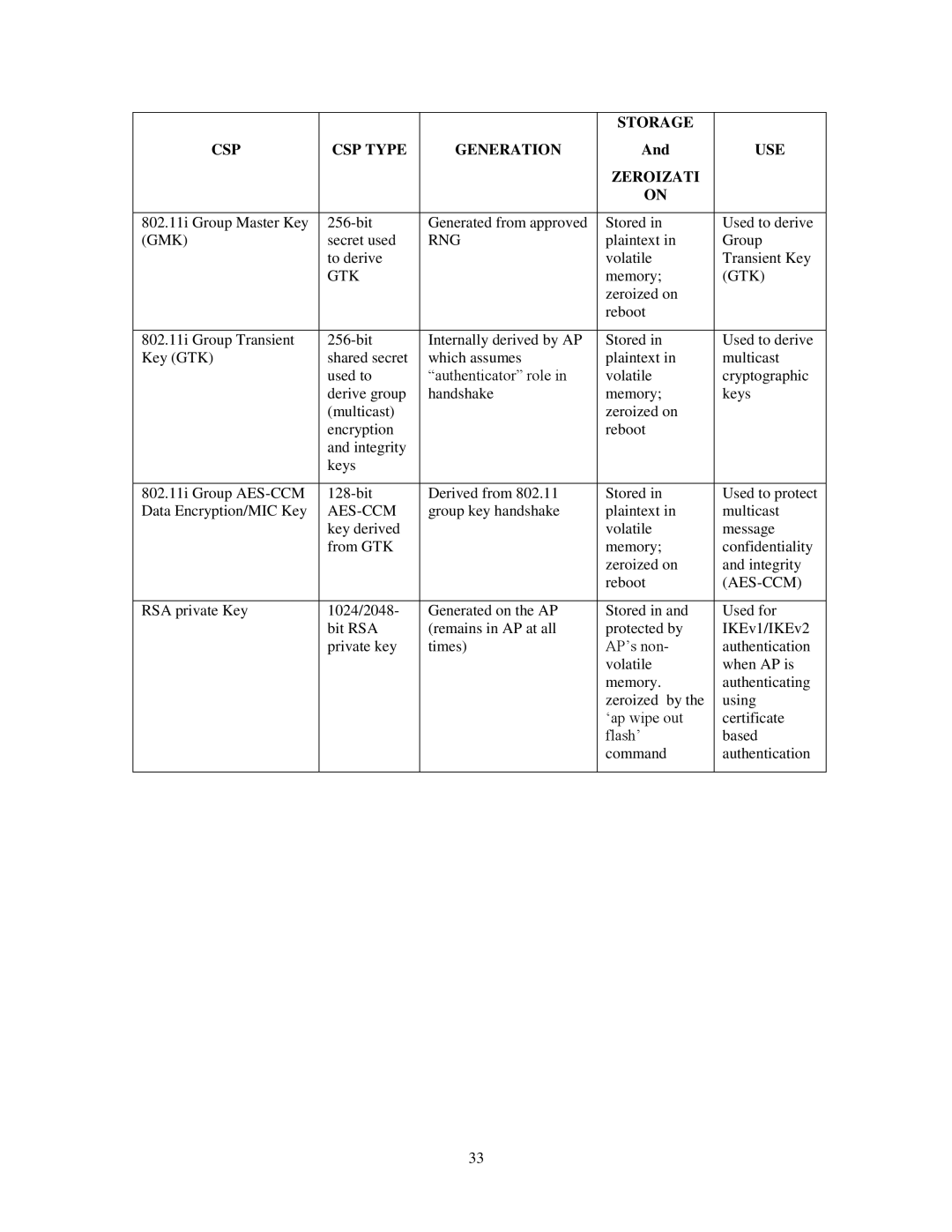
|
|
| STORAGE |
|
CSP | CSP TYPE | GENERATION | And | USE |
|
|
| ZEROIZATI |
|
|
|
| ON |
|
|
|
|
|
|
802.11i Group Master Key | Generated from approved | Stored in | Used to derive | |
(GMK) | secret used | RNG | plaintext in | Group |
| to derive |
| volatile | Transient Key |
| GTK |
| memory; | (GTK) |
|
|
| zeroized on |
|
|
|
| reboot |
|
|
|
|
|
|
802.11i Group Transient | Internally derived by AP | Stored in | Used to derive | |
Key (GTK) | shared secret | which assumes | plaintext in | multicast |
| used to | “authenticator” role in | volatile | cryptographic |
| derive group | handshake | memory; | keys |
| (multicast) |
| zeroized on |
|
| encryption |
| reboot |
|
| and integrity |
|
|
|
| keys |
|
|
|
|
|
|
|
|
802.11i Group | Derived from 802.11 | Stored in | Used to protect | |
Data Encryption/MIC Key |
| group key handshake | plaintext in | multicast |
| key derived |
| volatile | message |
| from GTK |
| memory; | confidentiality |
|
|
| zeroized on | and integrity |
|
|
| reboot |
|
|
|
|
|
|
RSA private Key | 1024/2048- | Generated on the AP | Stored in and | Used for |
| bit RSA | (remains in AP at all | protected by | IKEv1/IKEv2 |
| private key | times) | AP’s non- | authentication |
|
|
| volatile | when AP is |
|
|
| memory. | authenticating |
|
|
| zeroized by the | using |
|
|
| ‘ap wipe out | certificate |
|
|
| flash’ | based |
|
|
| command | authentication |
|
|
|
|
|
33